
Latest blog posts from Angela

People come, and people go, and while digital identities should cease to exist after a departure, many times, this doesn’t happen. At any given time, organizations can have thousands of user identities to manage and track, so when processes aren’t automated, it’s easy for many identities to fall through the cracks. This phenomenon is called Identity Lifecycle Management, and when it comes to access and security, it’s worth the time to get it right.
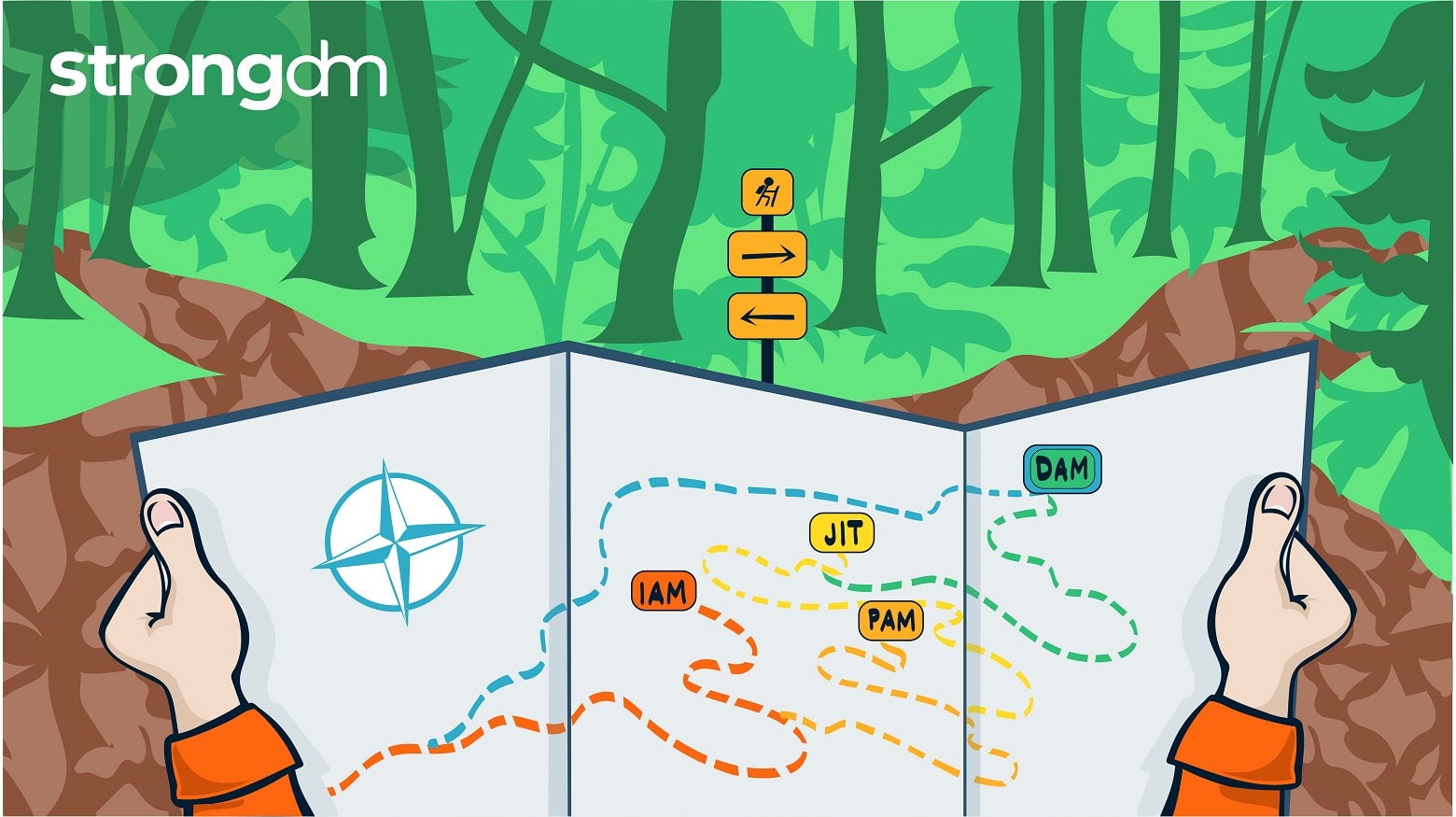
Historically, finding an infrastructure access management solution that is secure while still being easy to use has been extremely difficult. Too often, ease of use and complexity end up at odds. StrongDM addresses this challenge–and does so by integrating with your existing identity-based security initiatives. This blog details how StrongDM enables organizations to level up their access management approach to meet the requirements of Dynamic Access Management (DAM), bolster security, and
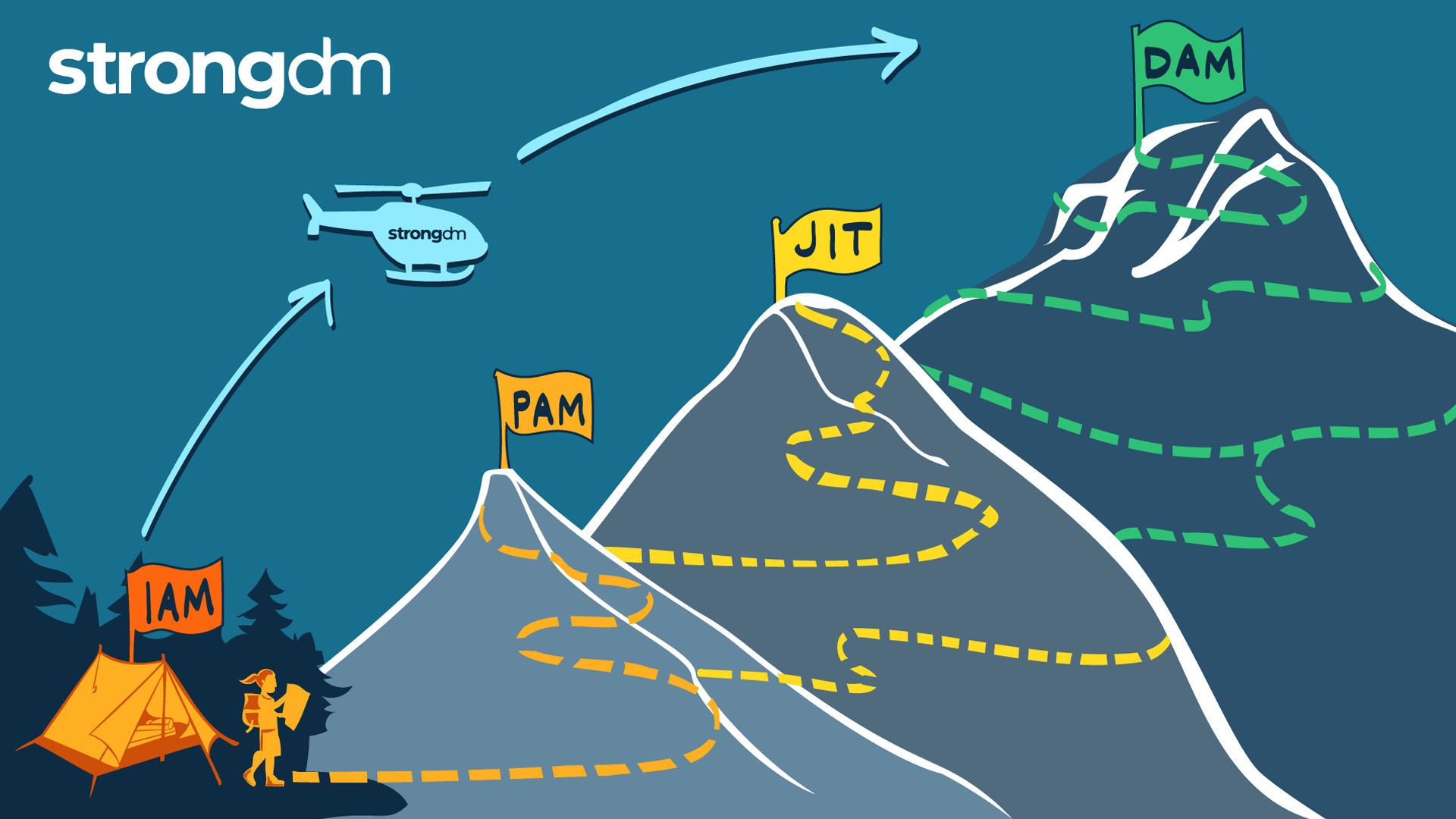
This article is your map for taking the work you’ve done with identity and your identity provider (IdP) and using it as your launchpad for access management. Shifting from identity-based access to a more dynamic access approach is necessary for organizations looking to modernize their access management and better protect sensitive resources at scale and in the cloud.

Infertility, Miscarriage, and the Workplace: Why Sick Time Isn’t Enough and How Companies Can Fix It
World Infertility Awareness Month happens every June to increase awareness regarding numerous infertility issues faced by couples across the globe. An estimated 1 in 6 people globally are affected by infertility, according to a new report from the World Health Organization. Yet, despite the prevalence of these issues, many workplaces still do not have adequate policies in place to support their employees during these difficult times.
So, you’ve decided to conduct an annual access audit. Now comes the obvious question: where do I start? Just like you wouldn’t embark on a mountain climbing excursion without a clear understanding of the terrain and gear you need, the starting point for an annual access audit requires an understanding of the process, people, and tools you’ll need to get started. Let’s go!
It’s undeniable: remote work is a catalyst for positive change, bridging gaps, and creating a more equitable and interconnected world. The benefits of remote work are widespread and well-documented. Remote work reduces carbon emissions by minimizing commuting and office-related energy consumption, contributing to a greener and more sustainable planet. It also enables companies to tap into a global talent pool, fostering innovation and cross-cultural collaboration.
The great outdoors and your infrastructure have more in common than you might think. Both environments have diverse ecosystems and unique terrain, but they can also feel wild and untamed. In the spirit of adventuring and access, we wrote this blog to help you learn why you should conduct an annual access audit every year.
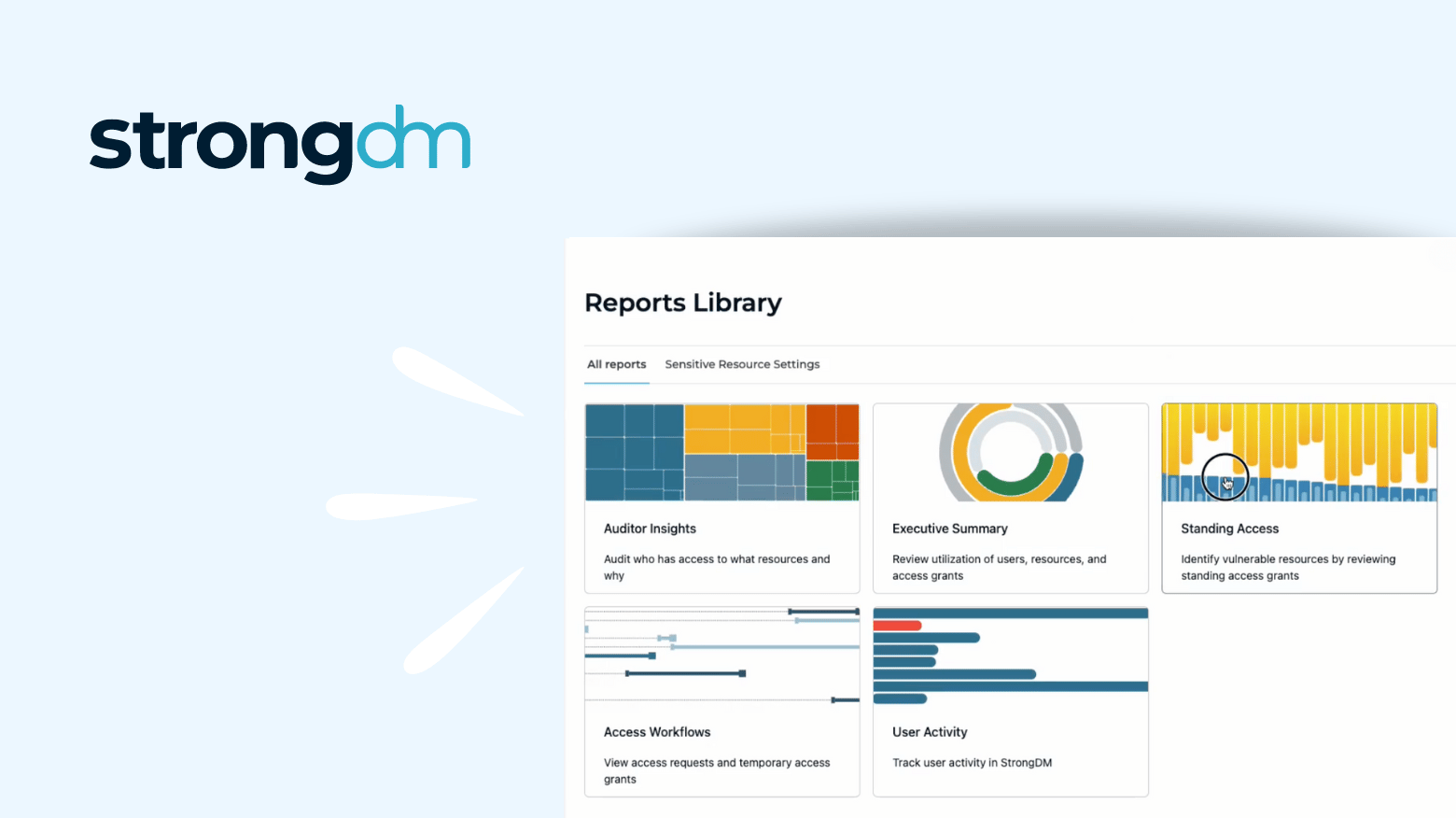
One thing is clear in the software space: New features aren’t adopted if they don’t solve specific problems for the people who actually use the product. Solving real problems means conducting research and asking hard questions. It means gathering evidence and interviewing multiple customers as well as leaders in the space to relieve the pain and positively impact the business.


