Latest blog posts from Dominic

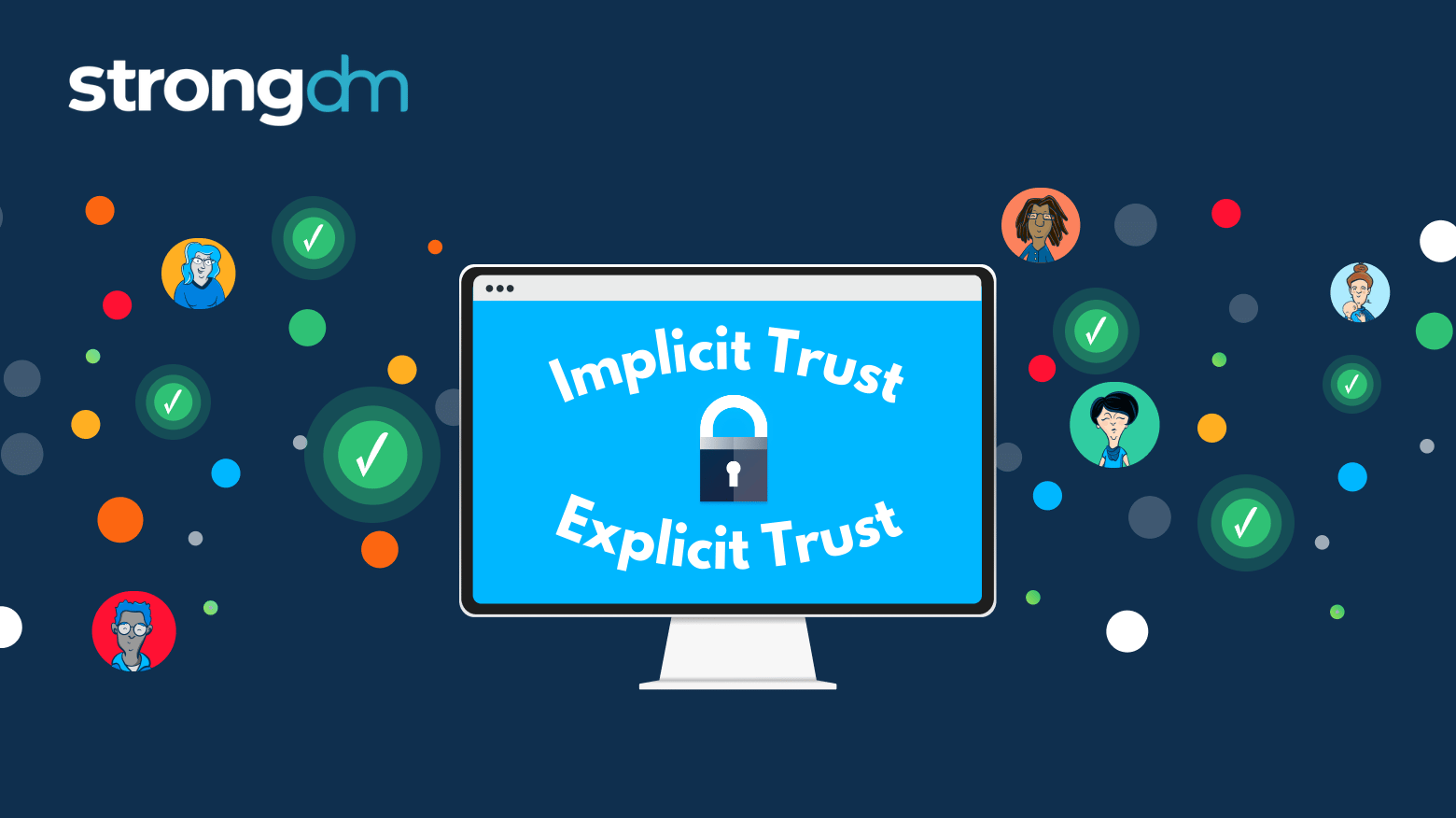
Trust is an essential cornerstone in access management. However, not all trust is created equal. When it comes to how you approach access, two types of trust stand out: implicit trust and explicit trust.

Standing Credentials. They’re a problem that seems to persist despite the latest security and access innovations. They’re also one of the main reasons that achieving zero trust is so hard–and enough of a problem that two strategic security initiatives have come to the forefront: Just-in-Time (JIT) access and Zero Standing Privileges (ZSP).
Let’s face it. If you work with any type of technology, you know that all software, hardware, and networking gear can fail in weird and unexpected ways. That’s why it’s critical that your technology stack has no single point of failure in your environment. At StrongDM, that means having options in a “break glass” scenario. We firmly believe that this is a requirement for the responsible operation of modern technology. So here’s how we tackle it.

Secret vaults ensure that sensitive and privileged credentials are well protected, rotated, and only used–or checked out–when necessary. This makes them a critical and foundational tool for credential protection in modern infrastructures.

The inability to audit, track, and understand how permissions are being used (or if they’re used at all) has been non-existent. Until now. The findings are clear: organizations need visibility into privileged access and its usage to fully understand and address their total attack surface.

We constantly hear about the gender gap in technology. Whether it’s the shortage of female founders and CEOs, claims of discrimination, or the comparatively small number of women in computer science majors, it seems that the issue has become a regular feature story in the news cycle. Disagreement over how to respond abounds on social media, in editorials, and not infrequently within tech companies themselves.
![How Better Access Improves Productivity of Tech Staff [New Research]](https://discover.strongdm.com/hubfs/better-access-improves-productivity-of-tech-staff.png)
Have you ever wondered how access impacts your productivity? If you're like most technical staff, the sum of hours lost adds up quickly across teams. It makes sense though. The longer it takes for you to access the systems you need, the less productive you are on any given day. And what happens when that access is too difficult to get? We found that teams typically set up workarounds.

Agent vs. Agentless architectures is a recurring debate - covering specifics from monitoring to security. But when it comes to Access Management, some key considerations are necessary when defining the scalability of your solution and its impact on efficiency and overhead over time.
-2.jpg)
Your guide to onboarding technical hires in 2022. Boost retention, engagement, and productivity with this new employee onboarding checklist.

The common element in all these data breaches is access control. As one security expert noted from the MyFitnessPal breach, “trust but verify” isn’t enough when data is stored in the cloud and accessed from locations outside a company’s secured internal network. The infrastructure access security gap has only expanded with the rise of remote work and increased numbers of connected systems.
strongDM asked 600 DevOps pros about the state of infrastructure access today. Their response? It’s out of control. Here’s an overview of our results.


