
- Role-based, attribute-based, & just-in-time access to infrastructure
- Connect any person or service to any infrastructure, anywhere
- Logging like you've never seen
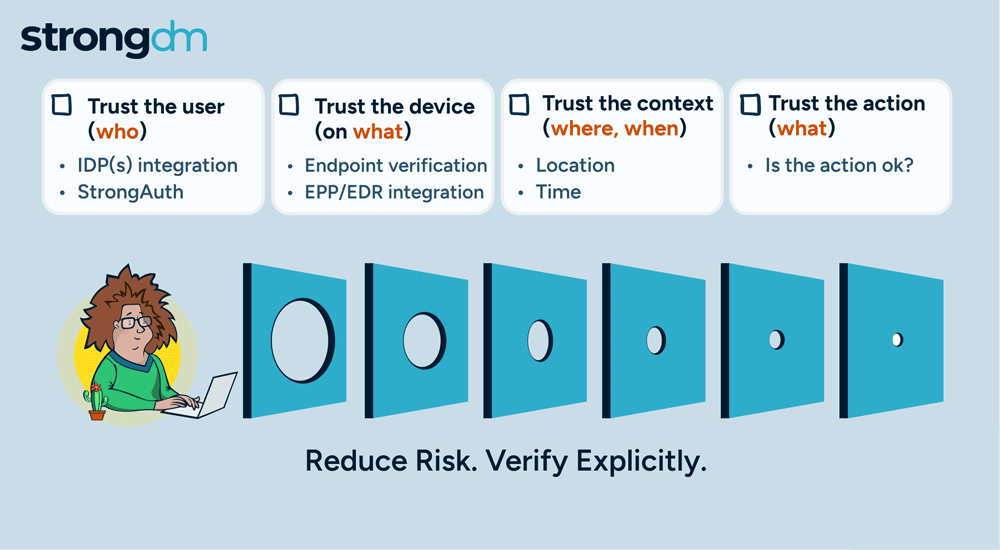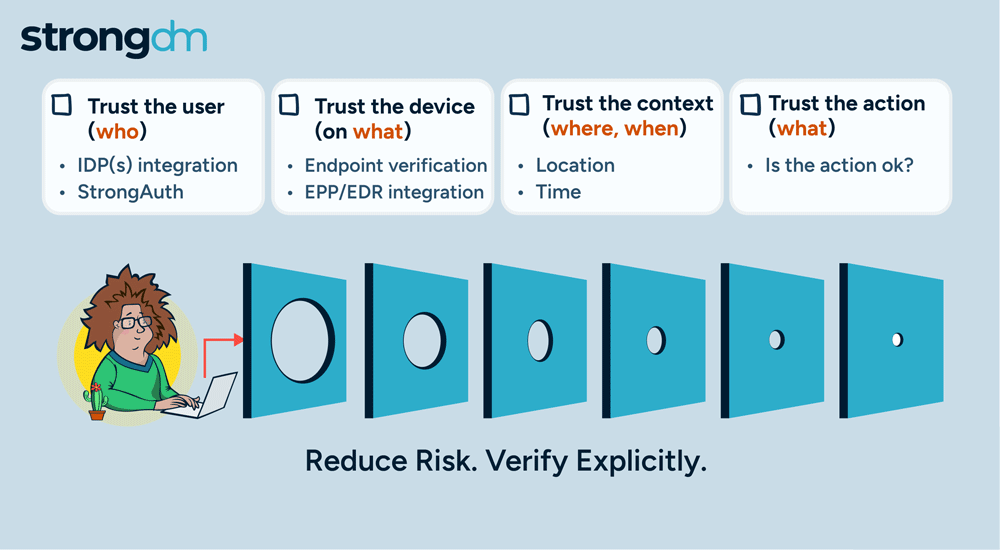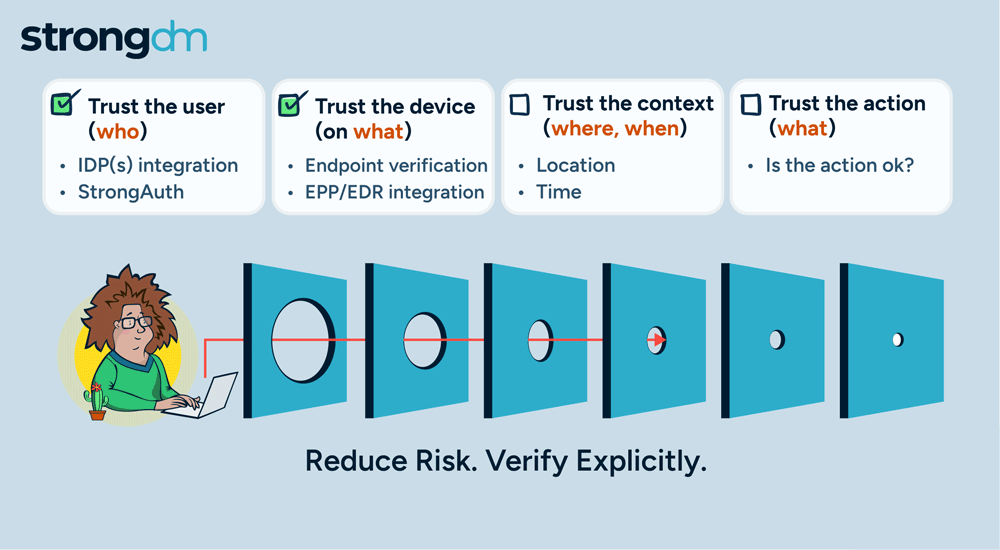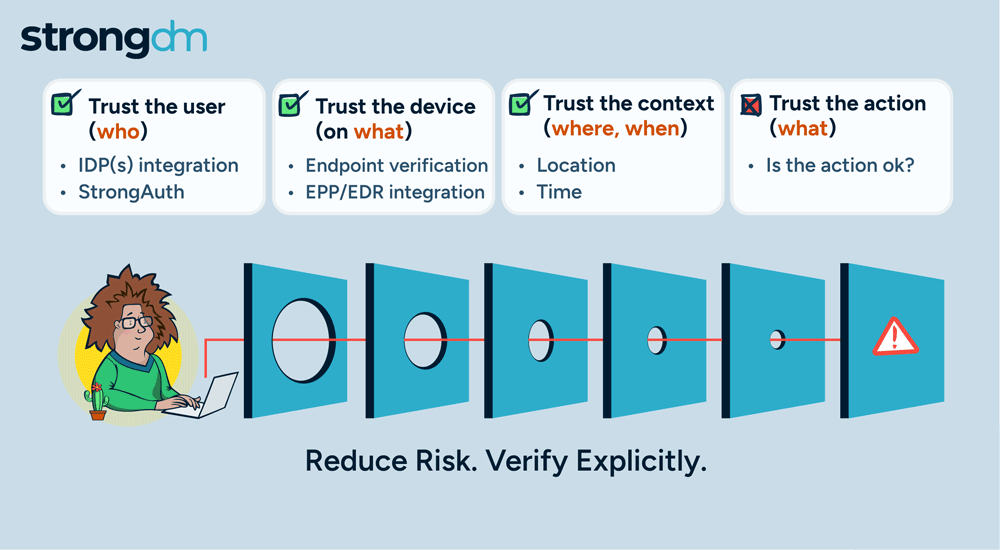
Access is no longer the primary challenge in enterprise security; it's the actions of users that are most aligned with managing risk. By focusing on how actions are authorized, StrongDM is giving customers a more effective approach to enterprise security. Our policy-based action control ensures that, in addition to access, every user action is scrutinized, delivering a higher level of security tailored to meet the complex demands of modern enterprises.
Today, we are adding another pillar in our Zero Trust PAM approach with the general availability of policy-based action control for Postgres databases. This new feature extends our security framework, allowing organizations to implement fine-grained, policy-driven controls over user access and actions within their Postgres environments. With this enhancement, you can ensure that every interaction with your Postgres databases is continuously authorized and aligned with your security policies, and that will deliver a higher level of protection and compliance for your critical data.
Here’s how this enhancement will benefit StrongDM users.
Proactively Respond to Changing Business Environments and Security Threats
Policy-based action control enables rapid adaptation to evolving business needs and emerging security threats. By facilitating and managing dynamic policies, security teams can modify user permissions and actions based on real-time context. This flexibility ensures that security measures are always up-to-date, and provides an agile response to any situation.

Continuous authorization and trust assessment in StrongDM’s Zero Trust PAM
Reduce Administrative Overhead and Complexity
Managing fine-grained access controls can be an administrative burden that burns cycles for engineering, systems, security, and operations teams. StrongDM simplifies this by centralizing policy management and automating the application of security policies. Administrators can define and adjust policies through a user-friendly interface, reducing the complexity and time required to manage access and action controls. This streamlining allows IT and security teams to focus on strategic initiatives rather than routine security management.
Narrow the Aperture for Access
Legacy PAM solutions see access as a one-and-done proposition, and their default position is to grant broad permissions that ultimately increase the risk of unauthorized actions. With policy based action control, you can narrowly define what users can and cannot do with their access. By specifying allowed or forbidden actions, you significantly reduce the risk of misuse. For example, a user may be permitted to read data but forbidden to modify it, which ensures that only authorized actions are performed.
Ensure Continuous Verifiable Compliance
Compliance requirements are constantly evolving, and changes in environments make alignment a massive challenge. With continuous authorization, StrongDM ensures that user actions always comply with the latest regulations and will adhere to the specific resource and environment configurations. Policies can be created to require justification for certain actions, which would add context to audits. StrongDM delivers audit logs and compliance reports that provide verifiable evidence of adherence to security policies, reducing the risk of fines and penalties associated with non-compliance.
Ensure Data Integrity and Reduce Risk of Data/System Misuse
Granular control is essential for protecting the integrity of your data and systems. Our solution allows for the creation of detailed policies that specify not only who can access data but also what they can do with it. This level of control helps prevent accidental or intentional misuse or alteration of data, safeguarding the accuracy and reliability of your information.
Decoupling Authorization from Business Logic with StrongDM
The StrongDM platform decouples the authorization engine from business logic, which is crucial for creating efficient, scalable, and flexible systems – that remain secure and compliant. Here's why:
- Flexibility and Efficiency: Our Zero Trust PAM platform ensures that flexibility does not come at the expense of efficiency. We deliver a streamlined approach that balances both aspects seamlessly.
- Component Reusability: With authorization decoupled from the business model, the permission management system becomes more generalizable and reusable across different systems. This saves development and maintenance time, and also enhances consistency across the organization.
- Separation of Concerns: By decoupling authorization from application logic, we allow business and security personas to operate independently. Each persona accesses only the data they need, reducing confusion and simplifying tasks. Security teams manage permissions without entangling themselves in business information.
- Independent Evolution: Operating with decoupled systems means that changes in business logic or schema do not necessitate alterations to the authorization engine. Each system can evolve independently, allowing for smoother updates and greater adaptability to new requirements.
StrongDM's continuous authorization empowers organizations to achieve these benefits, ensuring that business logic remains agile and security protocols are robust and manageable.
Enhancing Postgres Database Security with Policy-Based Action Control
StrongDM Policy-Based Action Control for Postgres provides comprehensive visibility into all database interactions and actions, and supports the entire range of Postgres operations. With this level of control, security teams can monitor and audit every action taken within the database, ensuring that they comply with the defined security policies and providing a detailed record for compliance purposes.
There is another level to how StrongDM Policy-Based Action Control defines and enforces access rules; it introduces mechanisms to block or add friction to non-compliant actions. These mechanisms can include multi-factor authentication (MFA), access workflows, and justification requirements, which add layers of security to sensitive operations. For example, if a user attempts to perform a high-risk action that is not fully compliant with the security policy, they may be required to provide additional authentication or justification before proceeding. This approach ensures that even if a user gains initial access, their actions within the system are continuously evaluated and controlled.
Policies for action control are enforced at the resource level, meaning that authorization controls are applied directly to the specific data or tools being accessed. This granularity ensures that security measures are not only comprehensive but also precisely targeted, reducing the risk of unauthorized access or action on sensitive resources.
By applying policy-based action control to Postgres databases, the StrongDM platform becomes the primary tool to enhance security, ensure compliance, and establish an internal environment that is agile and can respond in near real-time. This is done through the following key elements of our platform:
- Policy Definition and Management: Administrators can define policies using a combination of user attributes, roles, and contextual factors such as time, location, and device. These policies are managed through a centralized console, providing a comprehensive view and control over all user actions within Postgres databases.
- Real-Time Authorization: Each user action is evaluated in real-time against the defined policies. This continuous authorization ensures that only permitted actions are executed, and any deviations are immediately flagged and blocked.
- Audit and Reporting: Detailed logs of all user actions and policy enforcement are maintained, enabling thorough audits and compliance reporting. This capability ensures that organizations can provide proof of compliance with various regulatory requirements and internal security policies.
- Integration with Existing Security Frameworks and Tools: The platform integrates seamlessly with existing security frameworks and tools, providing a cohesive and unified approach to database security. This integration ensures that all aspects of your security infrastructure work together harmoniously.
- Full SQL Statement and Command Inspection: The full content of SQL statements and protocol-specific commands, such as SELECT, INSERT, UPDATE, and DELETE operations are inspected with granularity, ensuring that all database interactions comply with defined security policies and detecting any unauthorized or suspicious activities in real time.
StrongDM's Policy-Based Action Control for Postgres databases offers a powerful and flexible approach to database security. By combining detailed policy rules with real-time evaluation and comprehensive visibility, StrongDM ensures that every user action is scrutinized and authorized, providing a higher level of protection and compliance for your critical data.
Policy Use Cases
Let’s look at some actual policy examples, demonstrating how StrongDM Policy Based Action Control, powered by the Cedar Policy Language, can be applied to your Postgres databases and broader infrastructure.
Forbid Access for All Except a Role for a Tagged Resource
Scenario: As an administrator, you might want to restrict access so that only a specified user group or subset of users can perform all actions on development databases, while having read-only access to production databases.
// forbid all access
// unless the user has the `devDBUsers` role
// and the resource is tagged with `env` and `env=dev`
permit (
principal in StrongDM::Role::"devDBUsers"
action,
resource,
) when {
resource.sdm.tags has env && resource.sdm.tags.env == "dev"
};
// alternative 1: permit access for principals
// that have the `devDBUsers` role and
// want to perform specific actions in SQL
// and when the resource is tagged with `env` and `env=prod`
permit (
principal in StrongDM::Role::"devDBUsers"
action in [
SQL::Action::"select",
SQL::Action::"with",
SQL::Action::"values",
SQL::Action::"show",
SQL::Action::"set"
],
resource,
) when {
resource.sdm.tags has env && resource.sdm.tags.env == "prod"
};
// alternative 2: permit access for a principal
// who has the `devDBUsers` role
// when the resource is tagged with `env` and `env=prod`
// unless the principal is trying to write to SQL tables
permit (
principal in StrongDM::Role::"devDBUsers"
action,
resource,
) when {
resource.sdm.tags has env && resource.sdm.tags.env == "prod"
} unless {
context.sql has "writeTables"
};
// or forbid principals with the `devDBUsers` role
// when trying to write to SQL tables
// when the resource is tagged with `env` and `env=prod`
forbid (
principal in StrongDM::Role::"devDBUsers"
action,
resource,
) when {
context.sql has "writeTables" &&
resource.sdm.tags has env && resource.sdm.tags.env == "prod"
} ;
Allow Only Postgres-Supported Actions on Specified Resources
Scenario: As an administrator, I want to allow the user to run Postgres-supported actions only on the databases specified in the policy, and otherwise forbid all the actions on other resources.
Example Permit Statement
permit (
principal,
action,
resource == Postgres::Database::"r-1234/web"
Example Forbid Statement
forbid (
principal,
action,
resource
) when {
// list accepted resources here
resource != Postgres::Database::"r-1234/web"
};
);
Require MFA
Scenario: Allow access to one role with MFA
In this example, you want to create a policy statement that allows users in the oncall-dev role to access resources with particular tags, such as env=prod and region=us-east, but requires them to complete an MFA challenge prior to access to assist with the prevention of unattended access.
// Permit users in the specified role to perform actions
// against resources with particular tags after an MFA prompt
@mfa("")
permit (
principal in StrongDM::Role::"r-4eda054e645cff2e",
action in StrongDM::Action::"connect",
resource
) when {
(resource.sdm.tags has "env" && resource.sdm.tags["env"] == "prod") && (resource.sdm.tags has "region" && resource.sdm.tags["region"] == "us-east")
};
Scenario: Require MFA for delete or update actions
In this example, you want to create a policy statement that allows users to delete or update records in a Postgres resource, but requires MFA first as a security measure against destructive actions.
// Allow delete/update but require MFA
@mfa("")
permit (
principal,
action in [SQL::Action::"delete", SQL::Action::"update"],
resource in StrongDM::Resource::"rs-795ddebe62e00799"
);
Limit Query Result Set and Display Notification for Operator Role
Scenario: As an administrator, I want to restrict SQL query results to a maximum of 100 rows for users with the “Operator” role. A notification must be shown to the client indicating that the result set is limited to 100 rows.
// restricts queries to returning no more than
// the defined number of rows
@maxrows("100")
// notifies the client about the row limit
@notify("queries are limited to 100 rows")
// without additional restrictions,
// this permits StrongDM operators to execute all actions
permit (
principal in StrongDM::Role::"operator",
action,
resource
) unless {
principal in StrongDM::Role::"admin"
};
You can see more use cases and their corresponding policy statements in our documentation, and we encourage you join us for our Policypalooza webinar series which will feature topics such as fine-grained policies, continuous authorization and Zero Trust Architecture: Here’s our lineup and you can register here:
- 8/14 - MFA Everything: No System Left Behind
- 8/21 - Tag, You're It: Protecting Resources with Tag-based Policies
- 9/4 - Action Control Unleashed: Fine-grained Policies for Database Security
- 9/18 - Context Is Key: Leveraging Device Trust Signals for Smarter Access Policies
- 10/2 - Access, Granted! Crafting Dynamic Policies for Zero Standing Privileges
About the Author
Amol Kabe, Chief Product Officer (CPO), spearheads the StrongDM Zero Trust PAM platform. Previously, he was the Senior Director at Google, leading the Zero Trust and Identity and Access Management portfolio for GCP. His career includes executive roles at Netskope, driving its transition from CASB to SASE, and at Riverbed Technology. Amol was also a founding member at Tablus, a pioneer in Data Loss Prevention. To contact Amol, visit him on LinkedIn.

You May Also Like




