
- Role-based, attribute-based, & just-in-time access to infrastructure
- Connect any person or service to any infrastructure, anywhere
- Logging like you've never seen

Following on the heels of our recent announcement of 2022 being the Year of Access, StrongDM continues to ease friction and remove the barriers standing between technical staff and access to the resources they need—without sacrificing security—with our latest product release.
We’ve made it even easier to manage access to backend infrastructure in an increasingly ephemeral computing environment. Simply put, this is the most impactful, far-reaching release we’ve done to date, and early feedback from our customers has been a resounding “yassssssss.”
Take a look.
Simplify Provisioning with Deeper Identity Provider Integrations
We listened to our customers and, by far, the feature everyone was clamoring for was deeper integrations with identity providers. In fact, according to our recent survey, 53% of organizations take hours or weeks to grant access to infrastructure. Additionally, 88% of organizations require two or more persons to approve access requests.
With the release of tighter integrations with Okta and Microsoft Entra ID (formerly Azure AD) (or any SCIM-based directory service for that matter), you now have the ability to manage just-in-time, least-privilege access to your critical infrastructure right from your preferred identity provider (IdP), dramatically reducing the time needed to approve requests and grant access.
This means increased developer productivity and faster development cycles, all while supporting Zero Trust security for hybrid and multi-cloud environments. Not too shabby, eh?
More specifically, you can now:
- Automate user and group provisioning with a single source of truth.
- Synchronize Role assignments from your IdP to StrongDM.
- Choose which users and groups of users you want your IdP to manage in StrongDM.
- Manage policy exceptions via StrongDM by assigning IdP-managed users to StrongDM-managed Roles or StrongDM-managed users and service accounts to IdP-managed Roles.
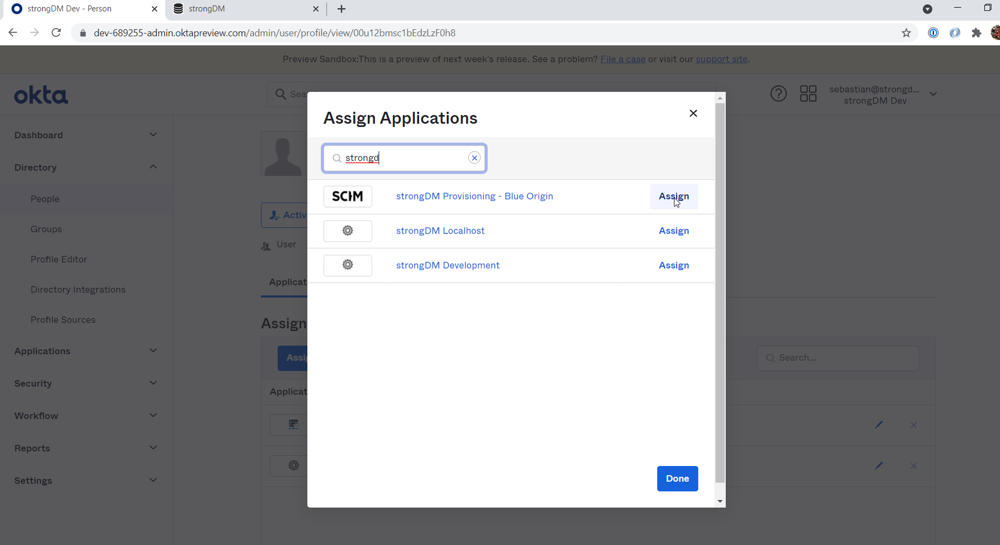
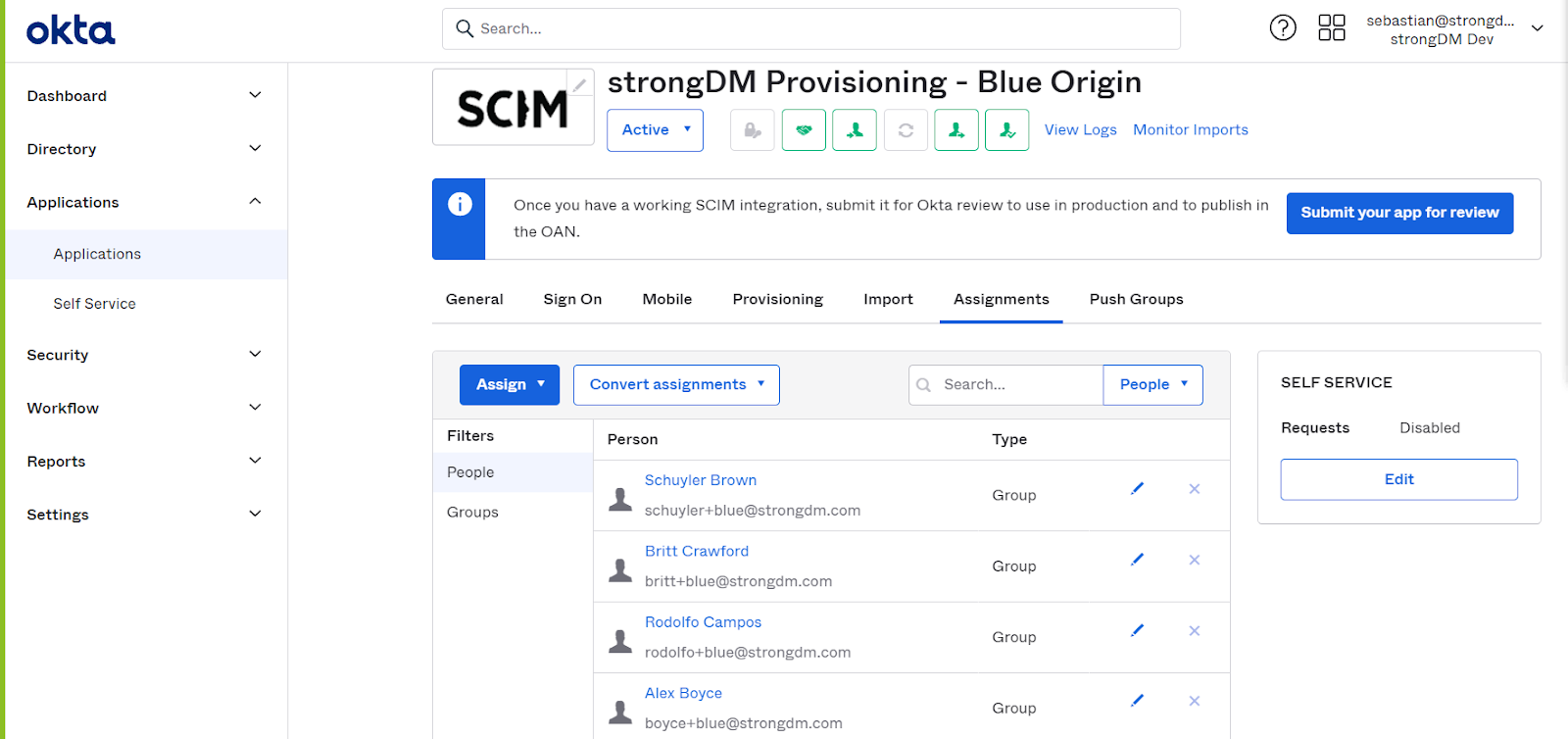
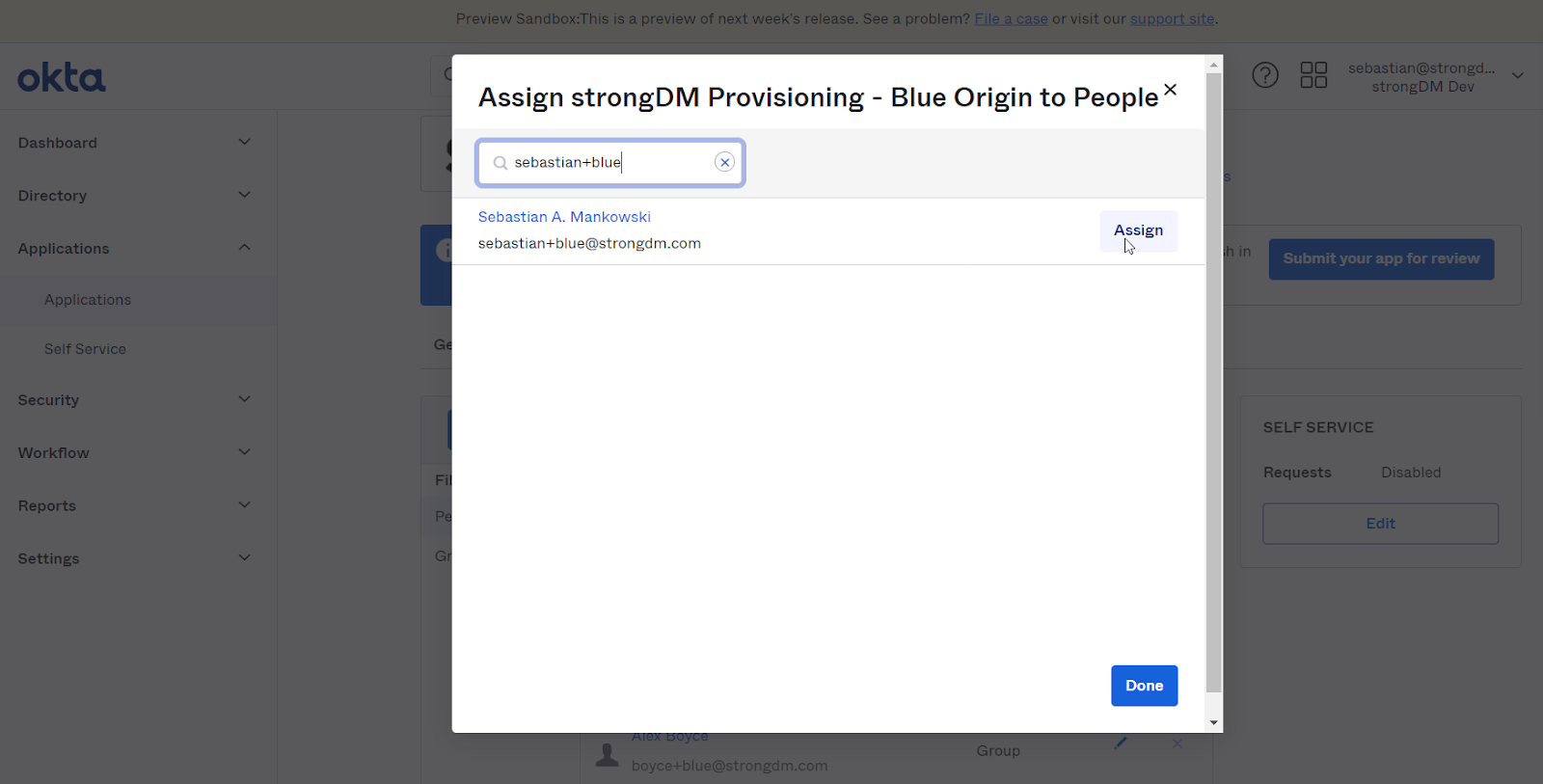
Here’s a more in-depth product video that gives you a taste of what these integrations can do.
- Okta documentation
- Microsoft Entra ID (formerly Azure AD) documentation
Get More Flexibility with Dynamic Access Rules
A perfect complement to static access rules, dynamic access rules eliminate loads of manual administrative work, giving businesses more granular control when provisioning infrastructure and enabling staff to access the resources they need more quickly.
Dynamic access rules enable businesses to enforce a powerful set of rules based on attributes such as tags and resource types. With this model, also known as attribute-based access control (ABAC), access is granted dynamically to Roles and their users every time a resource gets spun up or torn down.
This is particularly useful for companies with large installed bases with lots of resources on the backend, especially ephemeral ones. Basing access rules on tags offers much more flexibility with so much ephemerality in today’s computing landscape.
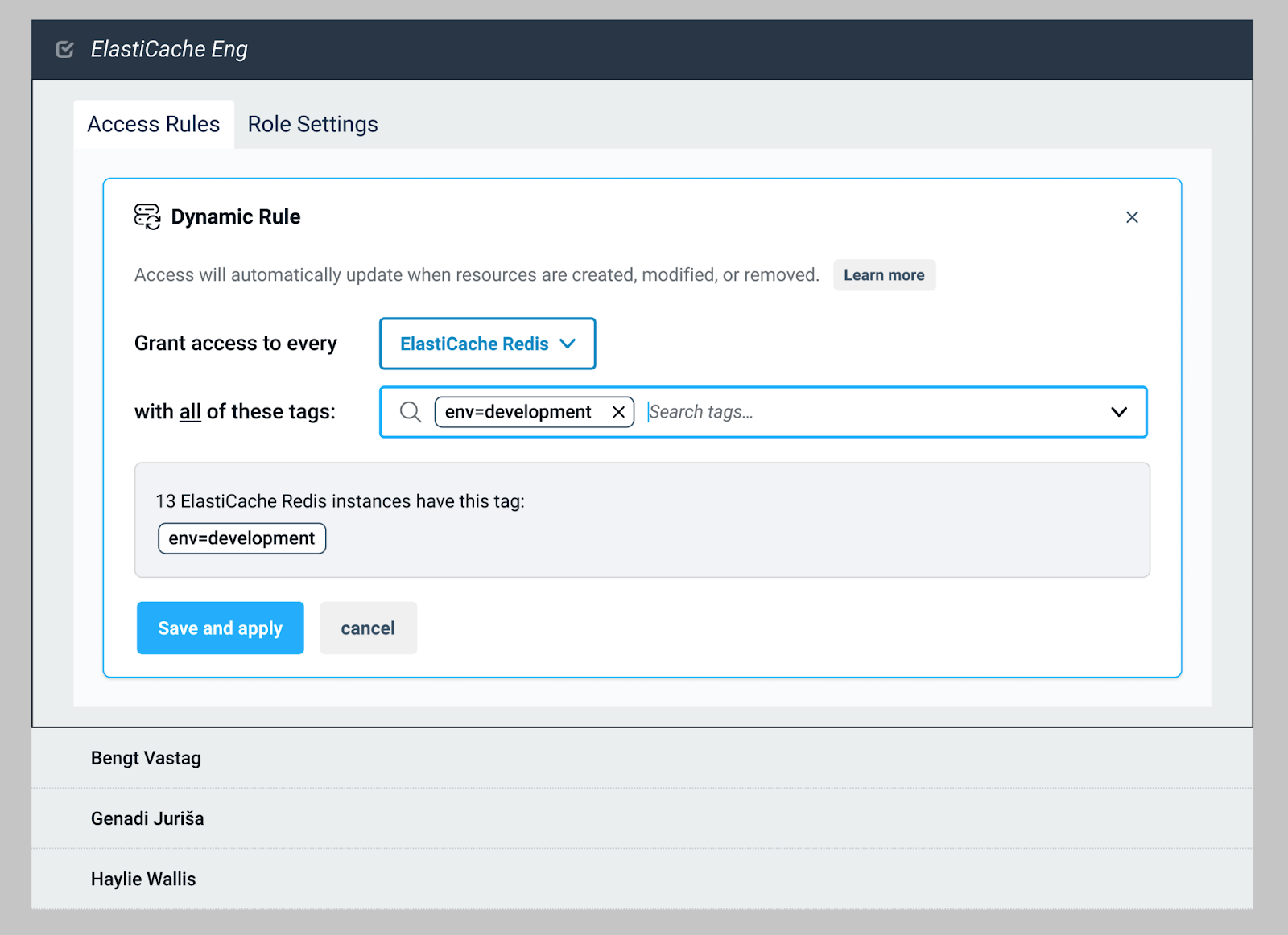
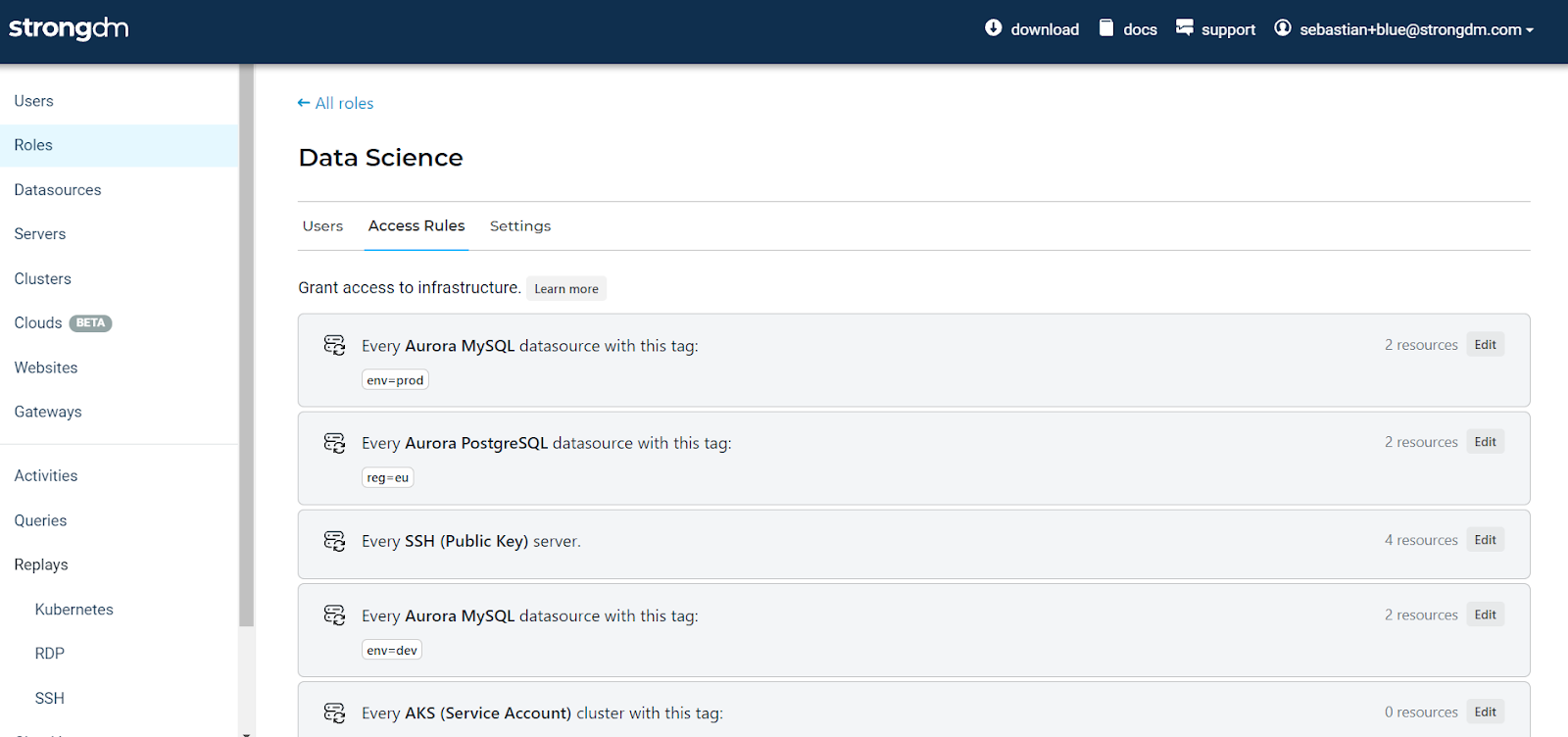
If you’re interested in seeing dynamic rules in action, check out this short video and let us know what you think. Good or bad.
- Dynamic Access Rules documentation
New to StrongDM? Sign up for our free no-BS demo and discover how frustration-free Zero Trust can work for you. Or, feel free to check out the results of our survey to see how you stack up against your peers.
About the Author
StrongDM Team, Zero Trust Privileged Access Management (PAM), the StrongDM team is building and delivering a Zero Trust Privileged Access Management (PAM), which delivers unparalleled precision in dynamic privileged action control for any type of infrastructure. The frustration-free access stops unsanctioned actions while ensuring continuous compliance.

You May Also Like




