Log Encryption and Storage
Last modified on February 27, 2024
On this page
Log Encryption & Storage allows you to define where and how your logs of queries, sessions, and replays are stored. You may enable StrongDM server storage, gateway or relay storage, or both. If you choose not to store logs on StrongDM’s servers, you must enable log storage on your relays or gateways.
sdm.log file. The storage location of these types of logs cannot be altered.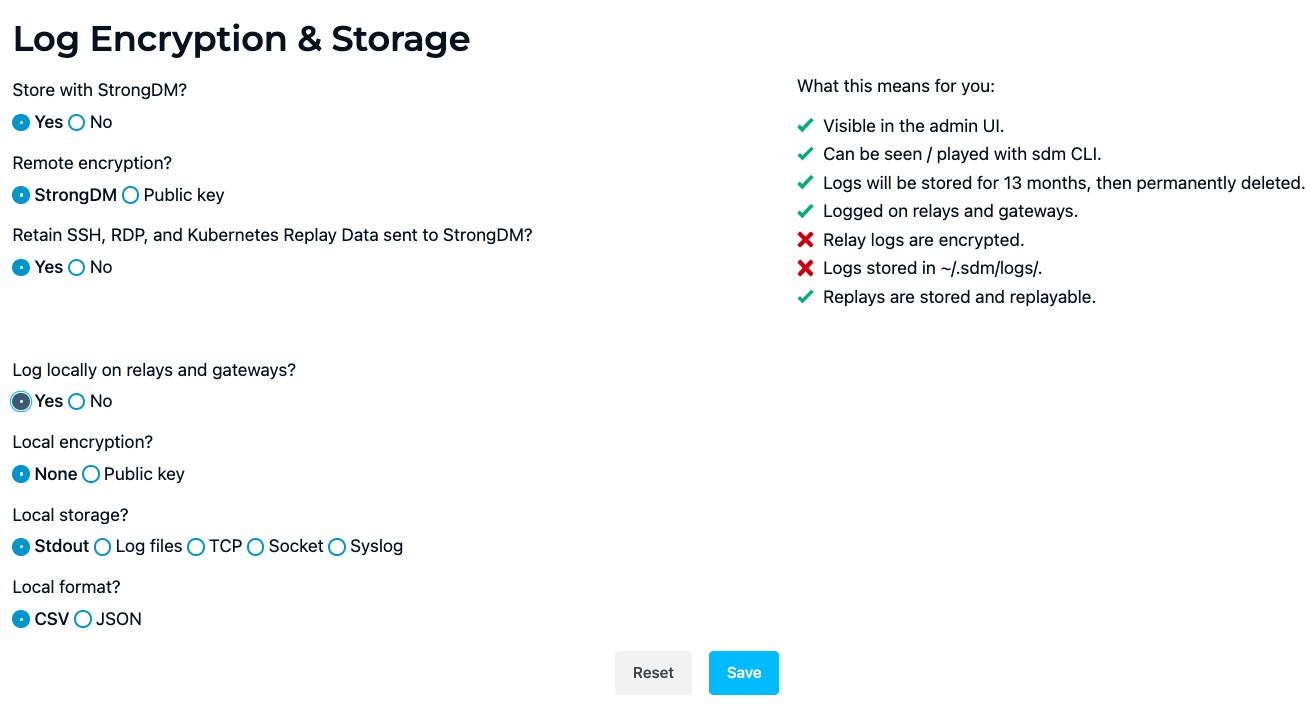
StrongDM Storage
Storing logs on StrongDM servers makes it possible to view or watch logs in the Admin UI and the CLI. Logs shown in the Admin UI are a much smaller subset of what is available via the CLI. Logs are stored and accessible via the CLI for 13 months. See our log retention policy for more details.
Remote encryption
When you store logs via StrongDM servers, you must configure a remote encryption option: choose either StrongDM or public key.
The StrongDM option encrypts logs using a StrongDM-generated key. The advantage of this is that StrongDM can decrypt and deliver logs to you on demand.
The Public key option lets you configure a public/private key pair. That is, the system uses your generated key to encrypt logs, but only you can decrypt them. This means that if StrongDM stores these logs, it can only send them back to you still encrypted.
Replay data
The Retain SSH, RDP, and Kubernetes Replay Data sent to StrongDM? option lets you choose what to do with replay data from SSH, RDP, and Kubernetes sessions.
If you select Yes, replays are stored and replayable.
If you select No, new replays are not stored remotely, replay attempts are disabled, and only session metadata (that is, user, resource, and total replay time) is stored. No replay data is stored.
If you attempt to replay a session via the CLI or SDKs while this option is set to No, then all recorded replays will present the session metadata, but no data can be queried. This behavior persists even if the option is set to No and then is later set to Yes because StrongDM doesn’t retain such data for recorded sessions when retention is disabled.
Note that if you set this option to No and then set it to Yes again, you will be able to attempt to replay those sessions in the Admin UI, but because there is no data to render, the replay will show a black screen for the total duration of the session.
Relay and Gateway Storage
You can configure query, session, and replay logs to be stored on your relays or gateways as the sole storage option or in addition to StrongDM server storage. Additionally, you have the option to store these logs in either CSV or JSON format.
Local encryption
When you store logs locally on your relays or gateways, you have two encryption options: none or public key. The public key option lets you configure a public/private key pair.
Relay and gateway destination options
The Local storage? option lets you choose the destination of your relay or gateway logs: STDOUT, a log file, a TCP port, a local socket, or a syslog.
- If you choose Stdout, the relay or gateway logs to
STDOUT, and you need to ensure that you have the relay or gateway process wrapped in a script that captures that output to redirect to a location of your choosing. - If you choose Log files, the relay or gateway writes logs to
<SDM_RELAY_HOME_DIRECTORY>/.sdm/logs/. This log rotates if the current log file grows to 100 MB. - The TCP option lets you specify a host/port combination to send logs. You can use this option to send directly to a log aggregator or SIEM that can accept syslog-style log delivery.
- The Socket option sends to a specified local socket. This option is primarily useful for log aggregators that put agents on individual hosts and expect logs to be delivered via socket.
- The Syslog option lets you specify the host/port combination of a syslog server to send logs using the syslog protocol. You can use this option to send logs directly to a syslog aggregator or a security information and event management (SIEM) solution.
For more information, see Log Locally to Gateways.
Gateway Log Encryption
By default, logging is enabled only to StrongDM servers. By turning on gateway or relay logging, you have logs located on the individual gateways and relays for your organizations, if any. Enabling public key encryption for relay logging encrypts these logs so they cannot be viewed without the private key.
To turn on relay encryption, ensure that Log locally on relays? is set to Yes and Local encryption? is set to Public key.
At this point, a text box displays, allowing you to paste in the public key you already created. Copy and paste the entire contents of the key into the text box, including the -----BEGIN PUBLIC KEY----- and -----END PUBLIC KEY----- lines.
Finally, click on the update button. You will receive a confirmation notice before the changes take effect.
Log Locally to Gateways
If you have configured StrongDM to save logs locally on your relays and/or gateways, you can extract queries and replays from the log files. Admin UI activities, on the other hand, are always stored on the StrongDM server.
You can configure relay logging to go to STDOUT or to the default ~/.sdm/logs location. The instructions that follow refer to whichever files hold logs in your configuration.
There are several event types in relay logs, but the ones that are generally most useful are start events, as they contain query data and SSH/RDP session information, including the Capture ID.
Encryption
If you have configured relay log encryption, your logs are not directly readable. To decrypt them, you need to use the sdm crypto parse-logs utility with the private.key file present.
Example:
cat logfile | sdm crypto parse-log private.key > decrypted-log
Queries
To find queries in the relay logs, look for start events that are of the following forms, containing the actual query.
The easiest way to find queries is to use grep to search for the datastore or query.
CSV example
`2023-03-23 18:10:54.265186636 +0000 UTC,start,af9e303c-07f7-42ee-84c4-279ca7b9de28,1333,psql-server-6,1016,Joe Admin,"SELECT name, setting FROM pg_settings WHERE source = 'session';",dc1952385fab5663c36c17579337686e71d6145f`
JSON example
{
"type": "start",
"timestamp": "2023-01-01T13:14:15.820199164Z",
"uuid": "01a2B3cd4Efghi567jKlMnop8qRs",
"datasourceId": "rs-123a45678910b123",
"datasourceName": "cli_example mysql",
"userId": "a-0a12b34c567d89d1",
"userName": "Jane Admin",
"query": "/* ApplicationName=DBeaver 7.3.5 - Metadata */ SELECT * FROM information_schema.COLUMNS WHERE TABLE_SCHEMA='mysql' AND TABLE_NAME='db' ORDER BY ORDINAL_POSITION",
"hash": "1234a56b7c891dab012ef3456g78h9i1jk2l3m45"
}
Replays
SSH
To view SSH session replays that are contained in relay logs, you must first find the Capture ID of the session you want to view. There are a couple ways to get the Capture ID.
You can use the sdm audit ssh command, as described in Use StrongDM Logs, to collect a list of SSH sessions that occurred during a specific time frame, and get their Capture IDs. Once you have the Capture ID, you can use the sdm ssh split command to extract all captures from a log file. They are saved as individual SSH files named after the Capture ID.
Example:
$ sdm ssh split relay.1521828535.0.log
5783cb5e-e1c8-44ba-b8ee-4bc4d8c28c7d.ssh
9d880e13-f608-4fe0-b1e7-deeb35bb9f2c.ssh
-j option to perform this operation correctly (for example, sdm ssh split -j relay.1521828535.0.log).Once you have the SSH file for the session you want to review, you can dump it to a text file and look at it in a text editor. Alternatively, you can cat the file to replay it at full speed.
Another way to get the Capture ID is to look in the relay logs. The Capture ID is shown in the relay logs in start events that are of the following form, containing a JSON document with connection parameters.
In the following example, the Capture ID is 9d880e13-f608-4fe0-b1e7-deeb35bb9f2c:
2023-03-23 18:10:02.970395873 +0000 UTC,start,9d880e13-f608-4fe0-b1e7-deeb35bb9f2c,1334,prod-312-test,1016,Joe Admin,"{""version"":1,""width"":92,""height"":25,""duration"":0,""command"":"""",""title"":null,""env"":{""TERM"":""xterm-256color""},""type"":""shell"",""fileName"":null,""fileSize"":0,""stdout"":null,""lastChunkId"":0}`
sdm ssh split command directly on the encrypted log by adding the -k flag: sdm ssh split -k private.key logfileRDP
If you have relay logging enabled, RDP session contents are also stored within them, although remote reassembly is not currently supported.
Remote Log Encryption
If you choose to set up log encryption (under Settings > Log Encryption & Storage), the logs, queries, and sessions recorded by StrongDM are encrypted, either on StrongDM, on the individual gateway or relay, or both. This section describes how to set up and use public-key encryption with StrongDM.
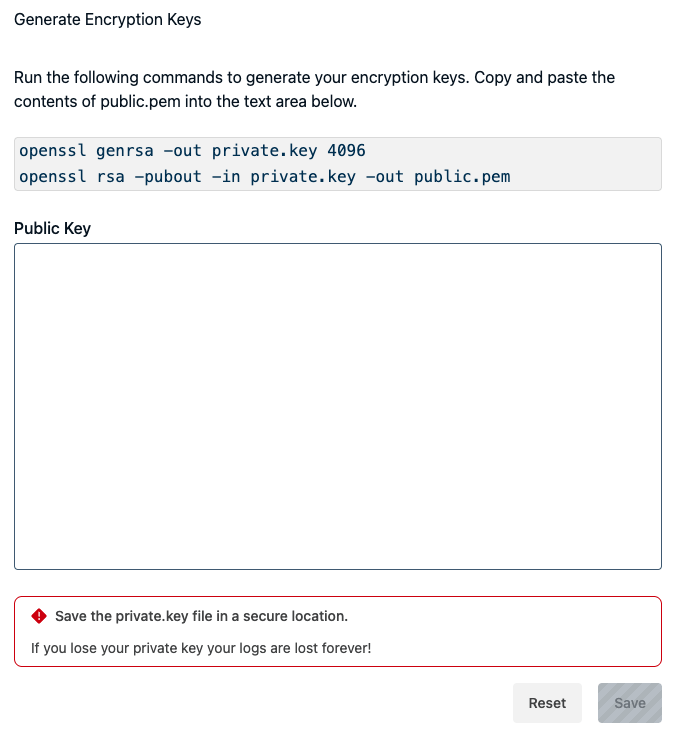
Setting up a public/private key pair
Run the following commands at a Linux or macOS command line to generate the private and public keys.
openssl genrsa -out private.key 4096
This command generates a private key in the specified location (private.key). Next you need to extract the public key, which is shared with StrongDM to encrypt logs and other data.
openssl rsa -pubout -in private.key -out public.pem
If you look at public.pem you see text similar to the following:
-----BEGIN PUBLIC KEY-----
MIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAyfST3A2ayVY9NVEoYk88
wA73JQEieNML0yS4gGXuTnvoPwijXh2Ez/eDbtg2u9+R1iz9kxE2LOfQB9OH2qzo
omlt7ua1IHGRQS+tGWeoA5Im4tRZOcS3w28uOnepy2ofoc+MtwpXyuY7ch4s+fUD
slcUY+BLhCWJpqp2cIgqivcVjcwNaF+nonqKzPpfqquke3u4bno3Urcq9qIHEb+H
ebomt96nFqwXqOyZrr8kvhckuKHZzBAdQiTocAhjvAxmzl+NzDanE3VAnLIZgapH
NawjUiiSBo6Ox2d65qtv+lg7dh3zq7iSgmm4ljeYjlXdASz6OW8EfCyltX3Vuc4W
GGUMtjEVxD6jKmheKHvbIig9NiewpgxFXQUznM70PguByWw5GPkt/jj5WWPx2X1Z
ab3J2JKqoWoOEvtR9aje1MKasZVD47CQKRE+MYN3J2I3mhsXNt/9dZTz/VLtRTUa
pMexP7N/i7wPhbsIgFyqqCqWgEZ+qgWJ+Yl13aI20GfFrUwTdh34o4t6LboCWs9e
Pn9ntRIxbaC448DDBylxnxyZUCE5eK8QBQfY72yLwnLHLztjJeLy4l7wv5fZwDlz
9HasFk0H8cZkNU3UZMjezYv0tYcaN8ko31TD2uLcquc/lylIWGlE0W4oXbOFcIvt
FRpBqdDfjdHwUVhJIfy8DkECAwEAAQ==
-----END PUBLIC KEY-----
This data is what you copy and paste into the StrongDM Admin UI when you turn on encryption at the StrongDM and/or relay level.
Store your private key (private.key by default) in a safe place. If you lose this key you cannot decrypt your logs, queries, and sessions.
Log destinations
There are two places you can enable log encryption: the StrongDM Admin UI and the local relay level. Either or both can be protected with the public key you just set up.
StrongDM
When logging is enabled to the StrongDM servers, queries and server sessions are visible for viewing and replay from the Admin UI and also can be accessed via the CLI. If you turn on StrongDM encryption, however, queries and sessions are not directly visible in the Admin UI. You are still able to access them via the CLI, however.
To turn on StrongDM server log encryption, ensure that Store with StrongDM? is set to Yes and Remote encryption is set to Public key.
At this point, a text box displays, allowing you to paste in the public key you already created. Copy and paste the entire contents of the key into the text box, including the -----BEGIN PUBLIC KEY----- and -----END PUBLIC KEY----- lines.
Finally, click on the update button. You will receive a confirmation notice before the changes take effect.
Use StrongDM Logs
When logging is configured for the StrongDM Server, you can view the following kinds of log entries:
- Administrative activities
- Queries
- SSH, RDP, or Kubernetes session replays
These logs can be viewed directly through the StrongDM Admin UI or by using the CLI.
Admin UI
Within the Admin UI, you can look at activities, recent datasource queries, and replay SSH and RDP replays.
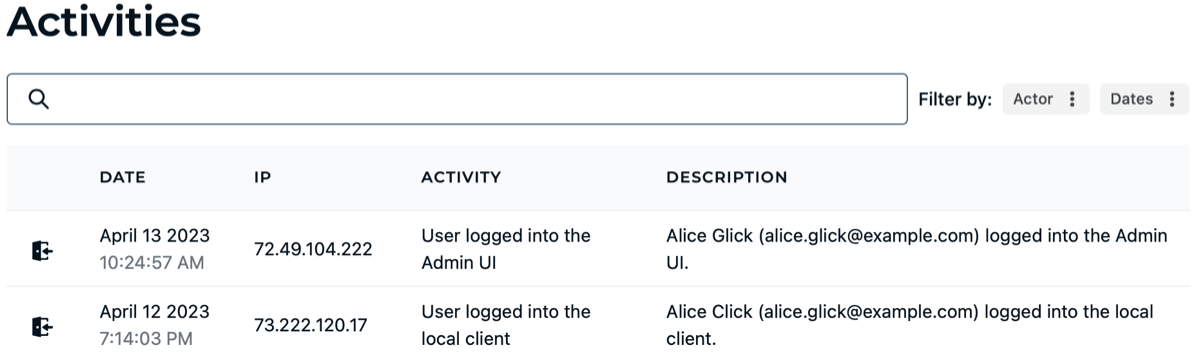
Activities
On the Activities page, you can view administrative activities, and browse from recent to older using the navigation at the top and bottom of the page.
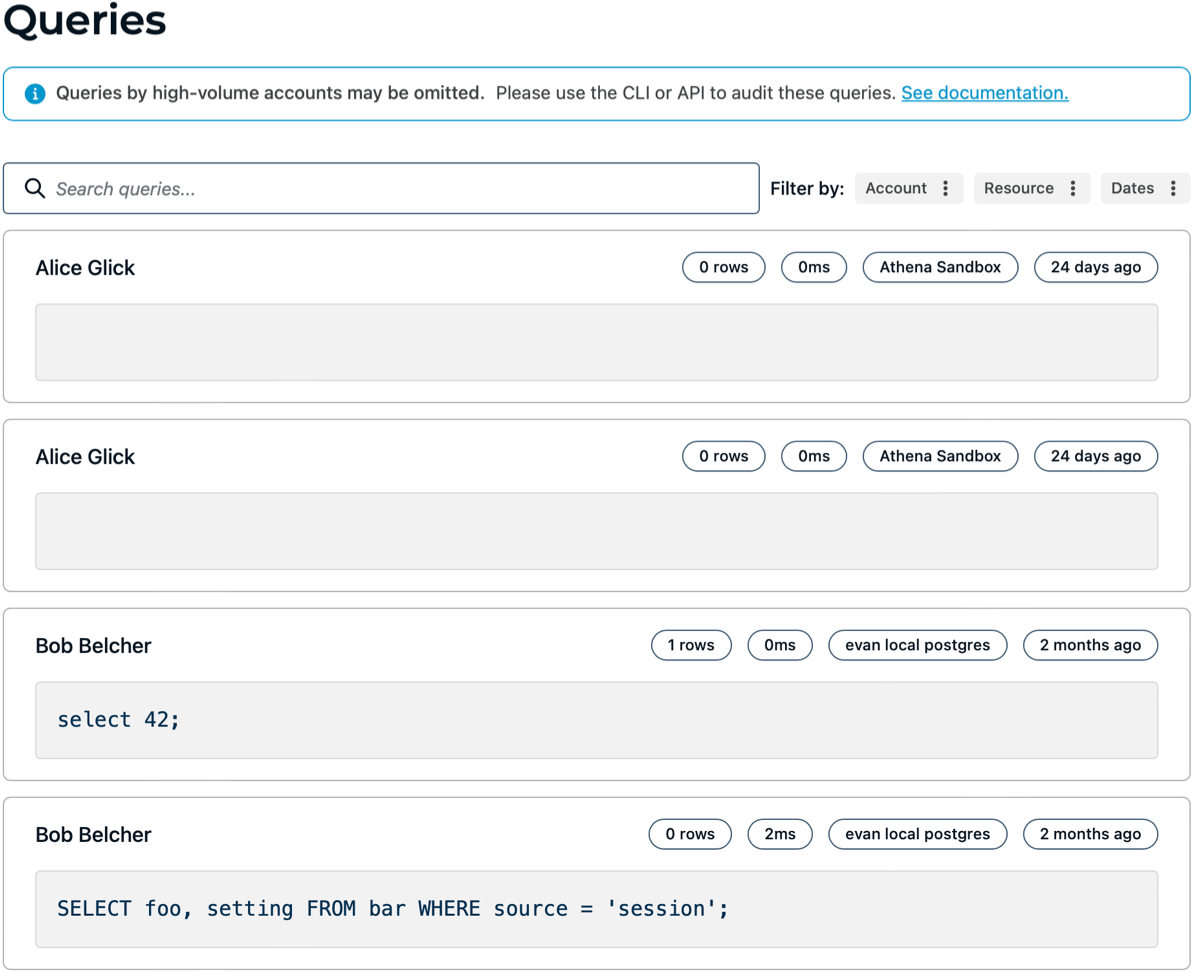
Queries
If you click on the Queries page, you can view a real-time list of recent datasource queries within your organization. To see older queries or search within a certain time frame, use the CLI sdm audit queries function, which is described in the CLI section.
Note that resource tags on queries represent a moment in time. Because tags can change for a resource, the ones that appear in the audit trail may or may not be as you expect, but rather, reflect the state of the resource’s tags at that time.
Replays
On the Replays page, you can view all SSH, RDP, and Kubernetes replays, using the navigation at the top and bottom of the page.
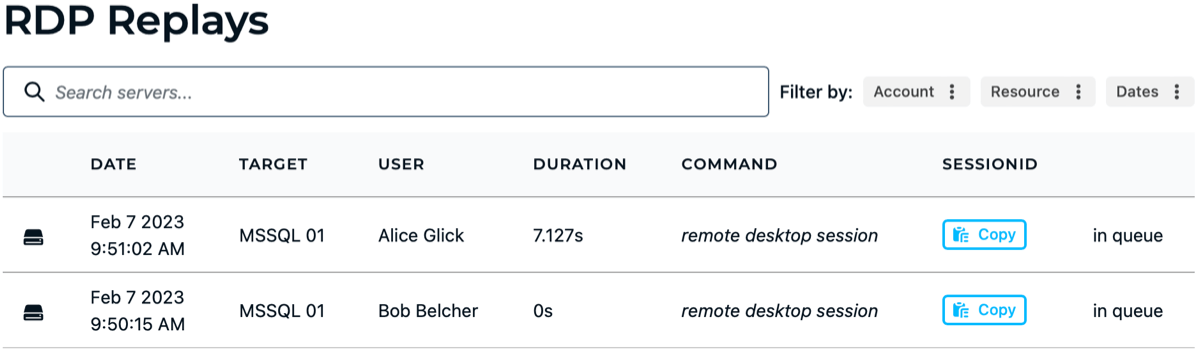
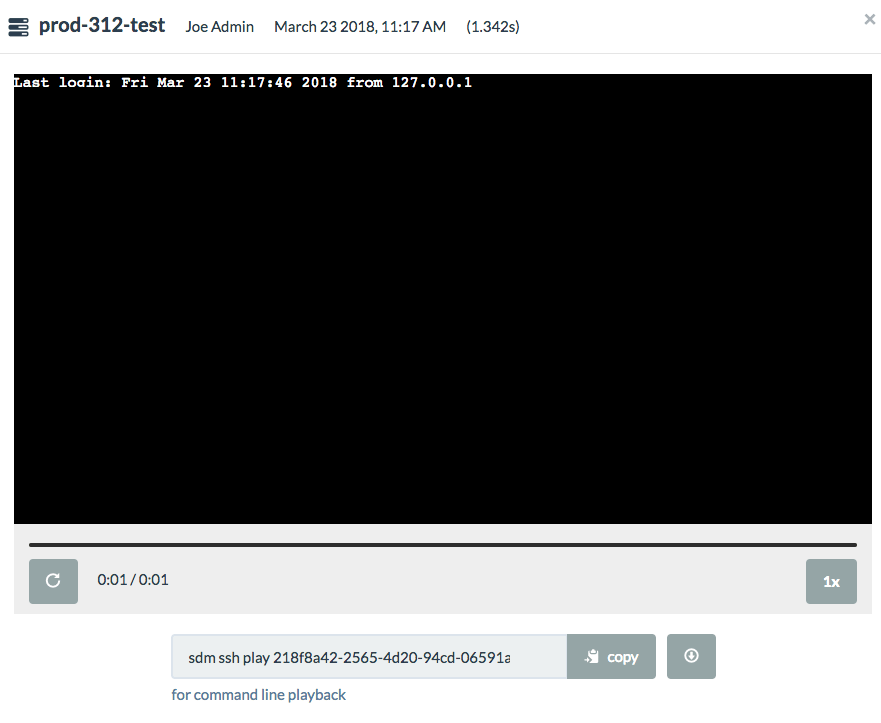
Clicking on a replay session launches a web player where you can watch the session replay in real time.
CLI
From the sdm command-line interface available on macOS and Linux, you can access all auditing—activities, queries, and replays—via the StrongDM API.
Activities
To review activities on the StrongDM Admin UI, you can use the sdm audit activities command. By default, it returns the 10 most recent Admin UI activities.
Example:
$ sdm audit activities
Timestamp,IP Address,Actor ID,Actor Name,Activity,Description
2023-03-22 12:28:40.276507 +0000 UTC,71.232.116.201,1016,Joe Admin,user logged into the UI,Joe Admin (admin@company.com) logged into the UI.
2023-03-22 15:23:26.375064 +0000 UTC,71.232.116.201,1016,Joe Admin,organization setting updated,Joe Admin (admin@company.com) changed the organization setting local log storage to none.
2023-03-22 15:23:26.376804 +0000 UTC,71.232.116.201,1016,Joe Admin,organization setting updated,Joe Admin (admin@company.com) changed the organization setting local log encode to plaintext.
2023-03-22 18:05:49.45456 +0000 UTC,71.232.116.201,1016,Joe Admin,user suspended,Joe Admin (admin@company.com) suspended Bob User (bob.user@company.com).
2023-03-22 18:05:51.002598 +0000 UTC,71.232.116.201,1016,Joe Admin,user type changed,Joe Admin (admin@company.com) changed type of Bob User (bob.user@company.com) to user.
2023-03-22 18:05:51.07059 +0000 UTC,71.232.116.201,1016,Joe Admin,user added to role,Joe Admin (admin@company.com) assigned Bob User (bob.user@company.com) to Junk.
2023-03-22 19:51:53.343206 +0000 UTC,71.232.116.201,1016,Joe Admin,organization setting updated,Joe Admin (admin@company.com) changed the organization setting remote log encode to strongdm.
2023-03-22 19:51:53.346103 +0000 UTC,71.232.116.201,1016,Joe Admin,organization setting updated,Joe Admin (admin@company.com) changed the organization setting local log storage to stdout.
2023-03-23 14:37:43.710974 +0000 UTC,71.232.116.201,1016,Joe Admin,user logged out from the local client,Joe Admin (admin@company.com) logged out from the local client.
2023-03-23 14:38:16.927605 +0000 UTC,71.232.116.201,1016,Joe Admin,user logged into the local client,Joe Admin (admin@company.com) logged into the local client.
To look for activity in a specific timeframe, you can make use of the --from and --to flags. Each takes a timestamp of the form YYYY-MM-DD or "YYYY-MM-DD HH:MM:SS" (note the quotes). When using these flags, you can specify --from alone, or use --from and --to together. With these flags, the command returns all activities within the specified time frame. At this point, you can further narrow your search by using grep or other text processing to look for specific user, datasource, or server activity.
To view a continuous stream of Admin UI activities or to redirect the output to another location, you can use the -f (follow) flag.
Queries
Similarly to Activities, you can use the sdm audit queries command to find the most recent queries. This command alone returns the most recent queries, but you can use the --from and --to flags to time-box your search, just as with sdm audit activities. You can also use the -f flag to get a streaming output to STDOUT.
Example:
$ sdm audit queries
Time,Datasource ID,Datasource Name,User ID,User Name,Duration (ms),Record Count,Query,Hash
2023-03-21 20:48:27.816603 +0000 UTC,1333,Local pgsql,1016,Joe Admin,1,0,SELECT VERSION(),bfdacb2e17fbd4ec7a8d1dc6d6d9da37926a1198
2023-03-21 20:49:28.022841 +0000 UTC,1333,Local pgsql,1016,Joe Admin,1,0,SHOW ALL,1ac37f50840217029812c9d0b779baf64e85261f
2023-03-21 20:49:28.530386 +0000 UTC,1333,Local pgsql,1016,Joe Admin,8,0,"SELECT oid, nspname, nspname = ANY (current_schemas(true)) AS is_on_search_path, oid = pg_my_temp_schema() AS is_my_temp_schema, pg_is_other_temp_schema(oid) AS is_other_temp_schema FROM pg_namespace",e2e88ed63a43677ee031d1e0a0ecb768ccdd92a1
2023-03-21 20:55:28.637862 +0000 UTC,1333,Local pgsql,1016,Joe Admin,0,0,"SELECT oid, nspname, nspname = ANY (current_schemas(true)) AS is_on_search_path, oid = pg_my_temp_schema() AS is_my_temp_schema, pg_is_other_temp_schema(oid) AS is_other_temp_schema FROM pg_namespace",e2e88ed63a43677ee031d1e0a0ecb768ccdd92a1
2023-03-21 20:55:28.920521 +0000 UTC,1333,Local pgsql,1016,Joe Admin,29,0,"SELECT rel.relname, rel.relkind, rel.reltuples, coalesce(rel.relpages,0) + coalesce(toast.relpages,0) AS num_total_pages, SUM(ind.relpages) AS index_pages, pg_roles.rolname AS owner FROM pg_class rel left join pg_class toast on (toast.oid = rel.reltoastrelid) left join pg_index on (indrelid=rel.oid) left join pg_class ind on (ind.oid = indexrelid) join pg_namespace on (rel.relnamespace =pg_namespace.oid ) left join pg_roles on ( rel.relowner = pg_roles.oid ) WHERE rel.relkind IN ('r','v','m','f','p') AND nspname = 'public'GROUP BY rel.relname, rel.relkind, rel.reltuples, coalesce(rel.relpages,0) + coalesce(toast.relpages,0), pg_roles.rolname;",8b62e88535286055252d080712a781afc1f2d53c
2023-03-21 20:56:29.153809 +0000 UTC,1333,Local pgsql,1016,Joe Admin,2,0,"SELECT rel.relname, rel.relkind, rel.reltuples, coalesce(rel.relpages,0) + coalesce(toast.relpages,0) AS num_total_pages, SUM(ind.relpages) AS index_pages, pg_roles.rolname AS owner FROM pg_class rel left join pg_class toast on (toast.oid = rel.reltoastrelid) left join pg_index on (indrelid=rel.oid) left join pg_class ind on (ind.oid = indexrelid) join pg_namespace on (rel.relnamespace =pg_namespace.oid ) left join pg_roles on ( rel.relowner = pg_roles.oid ) WHERE rel.relkind IN ('r','v','m','f','p') AND nspname = 'public'GROUP BY rel.relname, rel.relkind, rel.reltuples, coalesce(rel.relpages,0) + coalesce(toast.relpages,0), pg_roles.rolname;",8b62e88535286055252d080712a781afc1f2d53c
2023-03-21 20:56:32.125572 +0000 UTC,1333,Local pgsql,1016,Joe Admin,0,0,select 42;,cad5386a37b29383f33869ffa64d1585f9c93a0e
2023-03-21 20:57:17.261133 +0000 UTC,1333,Local pgsql,1016,Joe Admin,1,0,"SELECT name, setting FROM pg_settings WHERE source = 'session';",dc1952385fab5663c36c17579337686e71d6145f
2023-03-21 20:57:52.547195 +0000 UTC,1333,Local pgsql,1016,Joe Admin,1,0,"SELECT name, setting FROM pg_settings WHERE source = 'session';",dc1952385fab5663c36c17579337686e71d6145f
2023-03-21 20:58:37.72325 +0000 UTC,1333,Local pgsql,1016,Joe Admin,1,0,"SELECT name, setting FROM pg_settings WHERE source = 'session';",dc1952385fab5663c36c17579337686e71d6145f
If you have turned on StrongDM log encryption, you need to have the private key to view the query contents. You can use the -k <private.key> flag to decrypt the queries and use the result. This flag can also be used in conjunction with the -f flag to stream decrypted query logs to another location.
There is an additional option for this command, --full, that pulls query logs from long-term storage. This has the following effects:
- The time frame precision is more coarse; results are returned in one-hour blocks.
- Query results may be delayed up to one hour (that is, results may not return queries performed within the last hour).
- All queries are returned, including those that skip the Admin UI and short-term storage.
Replays
You can list replays, play them, and grep for strings (SSH specifically) within replays via the CLI.
Listing Replays
Just like Activities and Queries, you can use sdm audit ssh and sdm audit rdp to view recent or time-specified SSH or RDP sessions, using the same flags.
$ sdm audit ssh
Time,Server ID,Server Name,User ID,User Name,Duration (ms),Capture ID,Hash
2023-03-21 20:51:16.098221 +0000 UTC,1334,prod-312-test,1016,Joe Admin,8572,s1lAGI1niKKwdSYQtwi62HIuYTIO,afb368770931a2aae89e6a8801b40eac44569d93
2023-03-21 20:53:01.4391 +0000 UTC,1334,prod-312-test,1016,Joe Admin,7515,s1lAxGI1uuKe7zpgJtwi6j2dIfjY,aa4aa0646469757df9f0b92fb5ca39a9c1bfd38d
2023-03-22 21:57:10.920914 +0000 UTC,1334,prod-312-test,1016,Joe Admin,10440,s1lAxGI1niKKwSYQtwi6229NmTpG,aa4aa0646469757df9f0b92fb5ca39a9c1bfd38d
2023-03-22 23:16:40.170815 +0000 UTC,1334,prod-312-test,1016,Joe Admin,5433,s1lAGI7rekCY29NmTpGQD5G22WlK,883b03873229301e58fb6c9ccf1a3f584953d13c
2023-03-22 23:21:49.987304 +0000 UTC,1334,prod-312-test,1016,Joe Admin,4529,s1lAGIfjYkNrEW5MDbi62HIuYTIO,883b03873229301e58fb6c9ccf1a3f584953d13c
2023-03-23 01:18:02.167322 +0000 UTC,1334,prod-312-test,1016,Joe Admin,6318,s1lAA4Jkn4LPkosDulWmyHgCqqeB,883b03873229301e58fb6c9ccf1a3f584953d13c
Replays
In addition, you may view live replays of SSH sessions, much like the replay window in the StrongDM Admin UI. To do so, you first need the Capture ID, which is conveniently displayed in the output of the sdm audit ssh command. Once you have the Capture ID of the capture you want to replay, you can use the sdm ssh play command to replay it in your command-line window.
$ sdm ssh play s1lAA4Jkn4LPkosDulWmyHgCqqeB
[... output elided ...]
If you just want to dump the commands and outputs from an SSH session to a file, perhaps for further analysis, you can use sdm ssh dump with the same syntax. This command dumps the contents of the session to STDOUT, letting you redirect the output to a file if you choose.
Similarly to queries, you need to use the -k <private.key> flag with capture replay/dump if you have turned on StrongDM log encryption.