Proxy Clusters
Last modified on June 20, 2025
There are multiple ways to arrange your StrongDM deployment, as explained in the Deployment page. The recommended way to deploy StrongDM is through the use of proxy clusters. Proxy clusters are one of the available ways for you to proxy client traffic to your resources. They also provide a way to segment your network so that particular proxies are used to access particular resources. Proxy clusters sit behind your load balancers, and they allow you to scale your infrastructure to handle large amounts of traffic as needed; but they can also be run with only one or two proxy workers for simple network segments.
When your organization is set up with proxy clusters, administrators can create proxy clusters, configure resources in StrongDM and attach them to the proxy clusters. Then, they allow users access to those resources through standing access with Roles or through Just-in-Time (JIT) access with Workflows.
Once they have been granted access, users can use the desktop app or CLI (/cli/) to connect to your resources. Their client reaches out to the appropriate proxy cluster. One of the workers in the cluster handles the request, verifies the client is authorized to connect, and obtains credentials to connect to the resource. The connection is proxied without the credentials ever being exposed to that user. The user simply clicks to connect and begins working on the resource, unaware of any of these behind-the-scenes actions.
Overview
A StrongDM proxy cluster comprises one or more proxy workers. A proxy worker is a process that mediates connectivity between clients and resources.
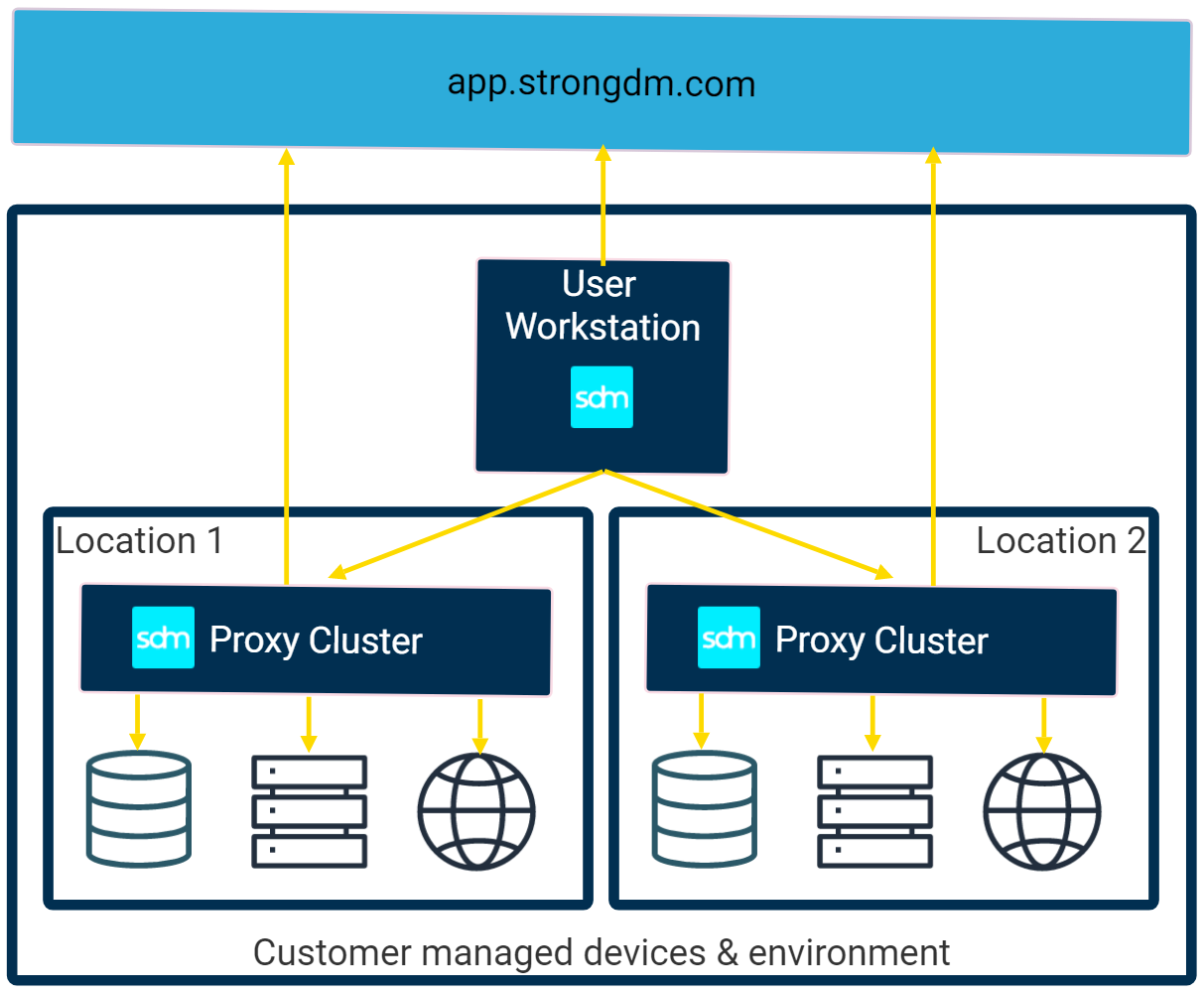
When a client connects to a StrongDM resource, it looks up which proxy cluster the resource belongs to and uses that cluster to connect. One of the proxy workers in the cluster parses and logs the request; fetches, decrypts, and injects credentials as necessary; and forwards the connection to the resource.
We recommend the following best practices when deploying a proxy cluster:
- Deploy one proxy cluster in each environment where you host resources.
- A cluster should consist of at least two proxy workers behind a load balancer for high availability.
- Configure the load balancer to accept connections on port 443 and forward them to the individual proxy workers on port 8443.
- Use a network load balancer to forward TCP traffic directly to the proxy workers without any processing.
- If the load balancer supports client IP address preservation, enable it.
- Use a DNS domain name to route traffic to the load balancer rather than an IP address.
Proxy worker egress requirements
Proxy workers must be able to send traffic to several destinations in order to function correctly:
Follow instructions in the tab for your organization's StrongDM region, not your location.
For more information, please see the Ports Guide.
Additionally, if your organization requires outbound traffic from your infrastructure to pass through your own corporate proxy, you must either or both of the SDM_HTTP_PROXY/SDM_HTTPS_PROXY environment variables. Please see the Enviroment Variables for a list of available environment variables for use with StrongDM.
Authentication keys
Each proxy cluster uses authentication keys to link proxy workers and (optional) bridge workers to that specific cluster. The default limit for keys is four per proxy cluster, which enables optional rotation. The access key and secret key are stored in the configuration file /etc/sysconfig/sdm-worker along with any SDM environmental variables.
Deploy a Single-Worker Proxy Cluster
This guide explains how to deploy a simple test cluster containing one proxy worker. For production environments we recommend using infrastructure tools to deploy multiple workers in a high availability configuration behind a load balancer. See these guides for platform-specific instructions if they apply to you:
Set up a 64-bit Linux instance with at least 2 CPUs and 4 GB of memory. Make sure the firewall allows clients to connect to the instance on port 443.
Note the IP address of the instance.
Log in to the StrongDM Admin UI.
Go to Networking > Proxy Clusters.
Click Add proxy cluster. You can name the cluster here or modify it later.
Enter the address of your Linux instance (with port 443 included) in the Advertised Address field (for example:
111.111.111.111:443).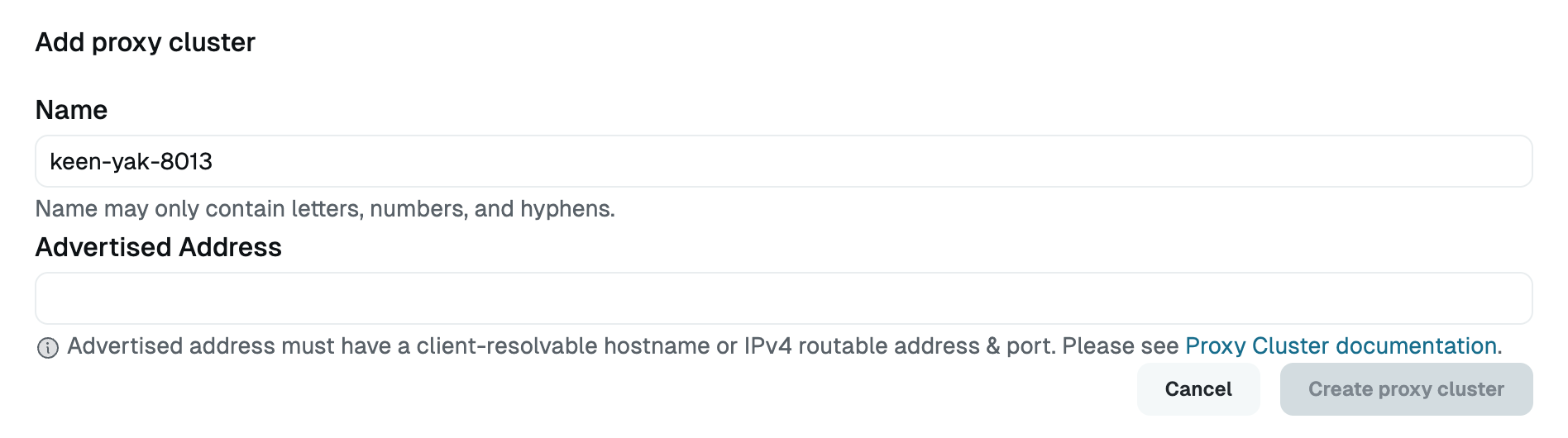
Add a New Proxy Cluster Click Create proxy cluster.
Click Add authentication key. The access key and secret key appear in a modal. Copy these and save them for use in a later step.
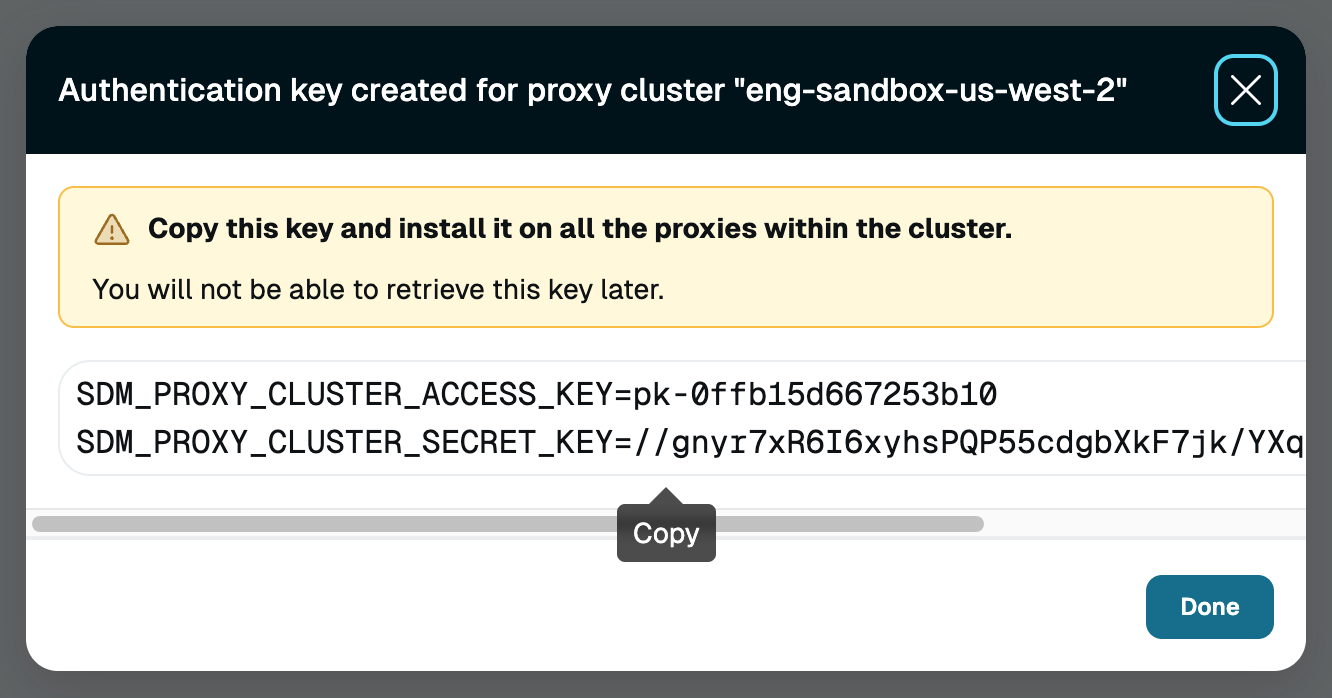
Proxy Cluster Key Log in to the Linux instance.
To run the worker via Docker (recommended), first install Docker. Then run the following command, substituting the access key and secret key you created:
Follow instructions in the tab for your organization's StrongDM region, not your location.
To run the worker via
systemd, download the StrongDM binary, unzip it, and run the installer. When prompted, paste the access key and secret key you created. After install, usesystemctl status sdm-workerto check that the service is running.Follow instructions in the tab for your organization's StrongDM region, not your location.
The installer must be run by a user that exists in the/etc/passwdfile. Any users remotely authenticated, such as with LDAP or an SSO service, will fail to complete the installation.For production installations, we recommend you configure the workers to bind to a higher port (8443 is the default) and use a load balancer to remap that to port 443.Confirm the proxy worker is running by verifying that the address is accessible from the appropriate end user network, as in the following example. If everything is working correctly, the proxy worker returns an HTTP 404 status code.
curl -k https://111.111.111.111
404 Not Found
Deploy with the CLI
Proxy clusters, like gateways or relays, can also be deployed using the CLI. This uses the sdm admin nodes command structure.
sdm admin nodes create-proxy-cluster --name <CLUSTER_NAME> <ADDRESS>:<PORT>
For more details, see the CLI Reference page for sdm admin nodes create-proxy-cluster.
Add Resources to a Proxy Cluster
To add resources to a proxy cluster, when adding or editing the resource in the Admin UI, select the name of the proxy cluster from the dropdown menu for the Proxy Cluster field. A resource attached to a proxy cluster will only be reachable via that proxy cluster.
Manage Existing Proxy Clusters
You can see a list of proxy clusters currently deployed in your organization in the Networking > Proxy Clusters page of the Admin UI. Selecting any cluster will bring you to the details view for that cluster, starting with the Resources tab. The Resources tab displays a list of all resources that are currently assigned to this proxy cluster. Each resource can be configured to be part of a particular proxy cluster in the configuration settings for that resource. There is also a Keys tab, which lists the available keys that can be used to add proxy workers to this cluster and allows the generation of additional keys. The Settings tab is where the cluster’s settings can be configured (name and address).
Search filters
You can use search filters in the Admin UI on the Networking > Proxy Clusters page to search for specific proxy clusters and display them according to their name, address, or tags. Searching and filtering can also be done on the Resources tab when viewing the details of a particular proxy cluster.
To use filters, type or copy/paste the following filters into the Search field, with or without other text. Do not use quotes or tick marks.
| Filter | Description | Example search |
|---|---|---|
listenaddr:<IP_ADDRESS> | Shows proxy clusters with the specified address | listenaddr:10.0.0.021:443 finds clusters that have an address of 10.0.0.021:443. |
name:<PARTIAL_STRING> or any free-form text | Shows proxy clusters with names that match the entered string; partial string OK | name:keen-coffee or coffee finds all clusters whose names contain those characters. |
tags:<TAG=VALUE> | Shows proxy clusters with the specified tags | tags:Environment=sandbox finds clusters that have the tag Environment=sandbox. |
Maintenance
See Maintenance Windows. This page provides information about how to schedule a maintenance window for gateways and relays, and it is the same process for proxy workers in a cluster.
Third-Party Certificates
The StrongDM control plane automatically signs and issues certificates for proxy clusters, but you can also configure your proxy cluster to use your own certificates. Proxy workers respect the following environment variables, which can be mixed and matched:
SDM_TLS_CERT_SOURCEdetermines where the proxy worker gets its TLS certificate from. Accepted values include:strongdm(default): The proxy worker terminates TLS using a certificate signed by the StrongDM proxy cluster CA generated by the control plane.file: The proxy worker terminates TLS using certificate and key PEM files specified by theSDM_TLS_CERT_FILEandSDM_TLS_KEY_FILEenvironment variables. The proxy worker automatically reloads the certificate from disk once per day, so the certificate should have a validity period of at least two days. Use this if you need to use your own certificates while also keeping the extra security afforded by mutual TLS.none: The proxy worker does not terminate TLS. Use this if you want to terminate TLS using your own load balancer. You must also specifySDM_TLS_CLIENT_AUTH=none.
SDM_TLS_CLIENT_AUTHcontrols how the proxy worker validates client TLS connections.direct(default): The proxy worker establishes mutual TLS directly with clients and validates their client certificates directly. This mode is incompatible withSDM_TLS_CERT_SOURCE=none.none: The proxy worker does not validate client certificates. Use this if you want to terminate TLS using your own load balancer.