Bridged Proxy Cluster
Last modified on April 9, 2025
Overview
You can deploy a StrongDM proxy cluster in “bridged” mode to enable access to a high-security internal network that only allows outbound network connections. The bridged proxy cluster has bridge workers outside the internal network and proxy workers inside the network. The proxy workers inside the network make outbound connections to one or more bridge workers running outside the network, which can then forward client traffic back to them.
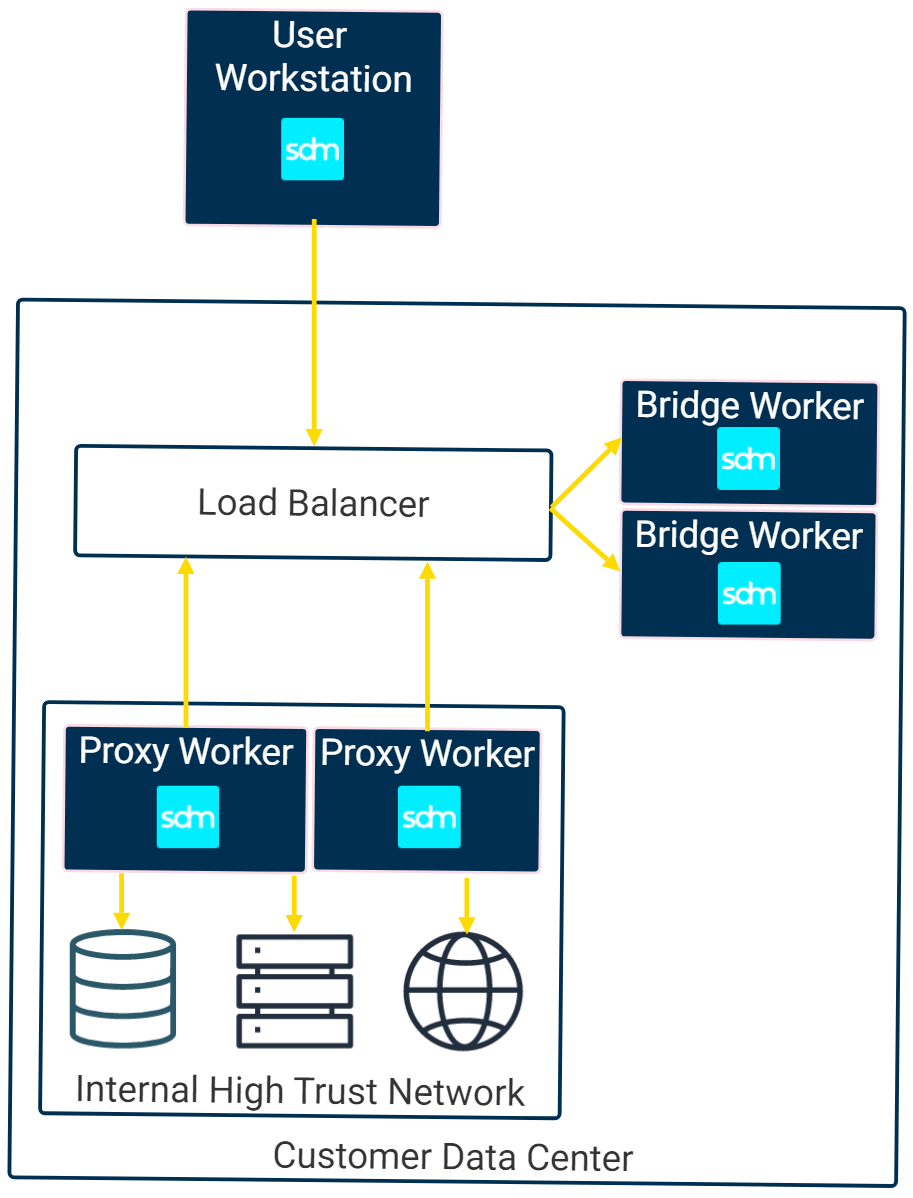
To deploy bridge workers, follow the steps to deploy a normal proxy cluster and add the following variable to the bridge workers’ environment:
SDM_BRIDGE=local
sdm install command, you can use the --bridge flag to set this variable.This instructs the workers to run in bridge mode. StrongDM recommends running multiple bridge workers behind a load balancer for high availability.
Once the bridge workers are deployed, you can deploy proxy workers inside your sensitive network and configure them to connect to the bridge workers by adding the following environment variable:
SDM_BRIDGE=<PROXY_CLUSTER_ADDRESS>
Instead of binding to a local port and listening for incoming traffic, the proxy workers connect to the load-balanced bridge workers and start accepting client traffic from them.
- You do not need to allow inbound traffic into your sensitive network.
- You do not need to deploy a second load balancer inside the network.
Proxy Egress Requirements
Workers in a bridged proxy cluster have the same egress requirements as in a normal proxy cluster. In addition, the proxy workers must be allowed to egress to the bridge workers.
Third-party Certificates
Third-party certificates are supported the same as in a normal proxy cluster. You must ensure the relevant environment variables are set on both the bridge workers and proxy workers.