SSO With SAML
Last modified on September 17, 2024
Overview
This guide provides instructions to set up single sign-on (SSO) using the SAML 2.0 (Security Assertion Markup Language) login standard. A successful configuration allows authentications between StrongDM as the service provider (SP) and the identity provider (IdP) of your choice.
Features
Basic features
- Users must authenticate with SSO every time they log in to StrongDM. Authentications from previous sessions cannot be reused.
Advanced features
- The current SAML integration uses SHA-256 with RSA signature encryption.
- Email address serves as the default user ID in the SAML assertion.
- A RelayState HTTP parameter cannot be included as part of the SAML request and response.
- IdP-initiated authentication is supported. If the setting is enabled, a user may initiate a login from the SSO provider.
Unsupported features
- The direct upload of an SSO provider’s metadata file is not available.
Prerequisites
To get started, make sure the following conditions are met:
- In your identity provider, you must have elevated privileges or be an administrator with the ability to manage application settings.
- In StrongDM, your permission level must be set to Administrator.
- Ensure you have a unique identifier for users. Only email address is currently supported.
Configure StrongDM
Use the following steps to configure StrongDM to work with your IdP. Once the SAML feature is enabled in StrongDM, these values can be copied to the configuration settings used for your IdP.
- In the StrongDM Admin UI, go to Settings > User Management.
- Click the Lock icon to make changes.
- Click Yes to enable single sign-on.
- Select SAML from the Provider dropdown. With this setting, users log in to StrongDM using your IdP and the SAML protocol.
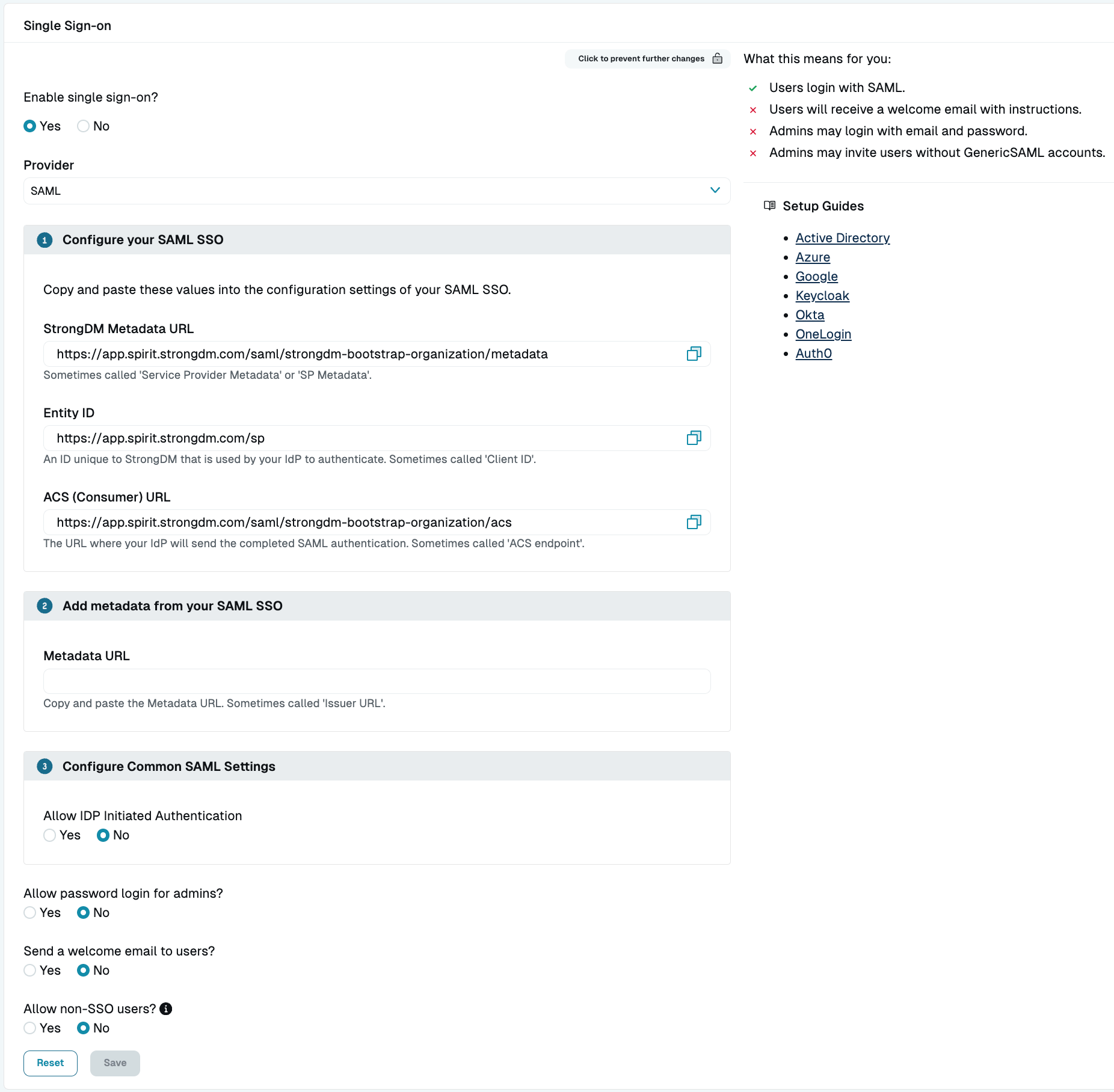
Verify the settings listed in the Single Sign-on section. Read-only fields are automatically generated based on your organization. You can copy these pre-populated values and paste them into the matching configuration settings found in your IdP interface.
The Metadata URL field typically comes from your IdP configuration and is required for StrongDM and the IdP to communicate. Follow the steps in the Add SAML Metadata section to add this URL value in StrongDM.Field Example Value Description Metadata URL https://app.onelogin.com/saml/metadata/<RANDOM_STRING>Public URL where StrongDM can request metadata for an IdP’s SAML configuration in order to communicate with the IdP; establishes trust by allowing StrongDM to correctly sign and validate signatures from the IdP StrongDM Metadata URL https://app.strongdm.com/saml/<ORG_NAME>/metadataPublic URL where the IdP can request metadata for StrongDM’s SAML configuration in order to communicate with StrongDM; establishes trust by allowing the IdP to correctly sign and validate signatures from StrongDM Entity ID https://app.strongdm.com/spString that uniquely identifies StrongDM as the SP entity to receive the SAML authentication message from the IdP ACS (Consumer) URL https://app.strongdm.com/saml/<ORG_NAME>/acsThe StrongDM Assertion Consumer Service (ACS) endpoint where the IdP sends its authentication response; responsible for receiving and parsing the SAML assertion Select the desired general SSO settings. If you wish to allow users to log in via a link from the SSO provider, enable Allow IDP Initiated Authentication.
Leave the StrongDM browser window open until you can obtain the Metadata URL from your identity provider.
Configure the Identity Provider
In general, you must consider the following items to configure SAML in your IdP dashboard and to create a successful SAML integration. These steps may differ from identity provider to identity provider.
On the IdP side, add StrongDM as an application that leverages SAML SSO.
Once the StrongDM application is created in your IdP admin dashboard, configure the SAML settings in your identity provider. Redirects are required, and some providers do not allow redirects by default (such as Jumpcloud). If there is a setting in your provider’s SSO configuration for allowing redirects, enable it. There may be additional settings to consider, but you can start by copying and pasting the values generated in step 4 of the Configure StrongDM section:
- StrongDM Metadata URL
- Entity ID
- ACS (Consumer) URL
In order to get SAML working with Microsoft Entra (formerly Azure AD) SSO, you have to add the user URN to the app on the Azure side, as specified in the Microsoft documentation. For information about additional settings not covered by this guide, please consult the IdP’s documentation.Confirm that the email addresses for all users are identical in both StrongDM and your identity provider.
To ensure users can access all intended resources, you may have to add each user to the StrongDM application created in your identity provider.
Once you have configured settings in your IdP, continue with the next section to add your SAML metadata to StrongDM.
Add SAML Metadata
SPs and IdPs swap XML metadata to share configurations, establish trust, and communicate with each other. For this purpose, you can copy the SAML metadata from your identity provider to the SSO section in the StrongDM Admin UI. After configuring the application settings in your identity provider, use these steps to add the IdP metadata URL to StrongDM. This value is required for your SSO configuration to work correctly.
- Find the IdP metadata URL in your identity provider.
- Go to the StrongDM browser window you left open while configuring the SAML settings in the Admin UI.
- In the Single Sign-on section, paste the copied IdP metadata URL from your identity provider into the Metadata URL field in StrongDM.
- Click Save to complete the setup.
Troubleshooting
When troubleshooting your SAML integration, note that the following can prevent successful user logins:
- The correct SAML metadata URL must be added in StrongDM. If this URL is incorrect, you may get errors that the XML is invalid during login attempts.
- If the application is misconfigured or the field values are wrong in your IdP, you can get a permission denied error in StrongDM. This error may also display if the user is not added to the app in your IdP.