Multi-factor Authentication - TOTP
Last modified on August 23, 2023
Time-based One-time Password (TOTP) is an additional factor for authentication. With TOTP, you first log in with your username and password as normal, and then you enter your TOTP.
With TOTP, a server-side algorithm generates a one-time code that expires and is rotated very quickly. An application on your device generates a matching code. When you enter the code from your device, the two are compared, and if a match, you authenticate. This factor requires you to physically have your device, in addition to the knowledge of your username and password, to log in to the service.
TOTP is available as a multi-factor authentication (MFA) option for StrongDM. This guide describes how to set up and configure MFA using TOTP for your organization. There is also a TOTP Device Enrollment guide.
Set Up TOTP for Your Organization
In the Admin UI on the Settings > Security page, under Multi-Factor Authentication, you can choose to enforce multi-factor authentication and then select TOTP as the method.

How to Reset TOTP for a User
Sometimes, a user may need their TOTP reset. For instance, the user may switch devices, delete their TOTP application, or require their device to be factory reset. In these cases, they have TOTP enabled as an authentication factor with an enrolled device that they can no longer use. This situation requires an administrator to reset their TOTP.
You can reset TOTP for a user in two places.
In the Users page in the Admin UI, in the Actions menu, there is an action in the list to Reset TOTP.
Additionally, in the details page for an individual user, the same actions are available on the right side of the page.
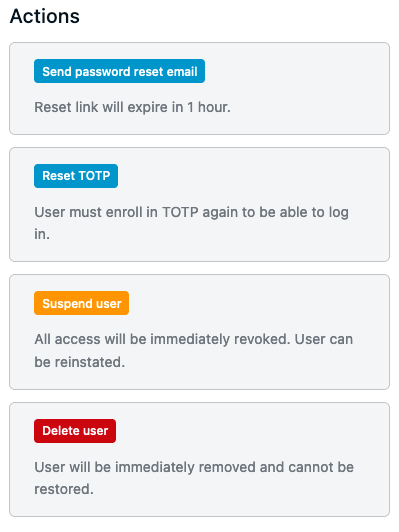
In either case, once you have reset the user’s TOTP, they need to re-enroll in TOTP in order to continue authenticating to StrongDM.
Troubleshoot MFA With TOTP
You may run into issues authenticating your StrongDM account with TOTP MFA enabled. The following topics can help you troubleshoot any errors you receive while logging in.
MFA alongside SSO
When you set up an SSO provider to authenticate with StrongDM and also enable MFA in the Admin UI, MFA prompts during logins do not occur. In this scenario, your configured MFA only plays a role to re-authenticate users when the desktop app locks due to inactivity, not during normal login attempts.
If using SSO, we recommend setting up MFA through your SSO provider to also trigger MFA prompts during user logins.