Real-Time Access Analytics
StrongDM delivers real-time access analytics, threat detection, and compliance visibility to proactively mitigate risks.

Leading global brands rely on StrongDM

Eliminate Hidden Risks
Insufficient visibility into access and user actions exposes organizations to unauthorized activities, insider threats, and compliance issues. Without real-time insight into who accesses what and when security teams struggle to detect or respond swiftly to potential threats. This blind spot widens security gaps, heightening the risk of data breaches and regulatory non-compliance.
5x
Faster to gather evidence for audits
70%
Reduction in number of engineers with admin rights
6x
Reduced time to identify and respond to incidents
0
Shared credentials with credential-less access for your end users
Real-Time Access Monitoring
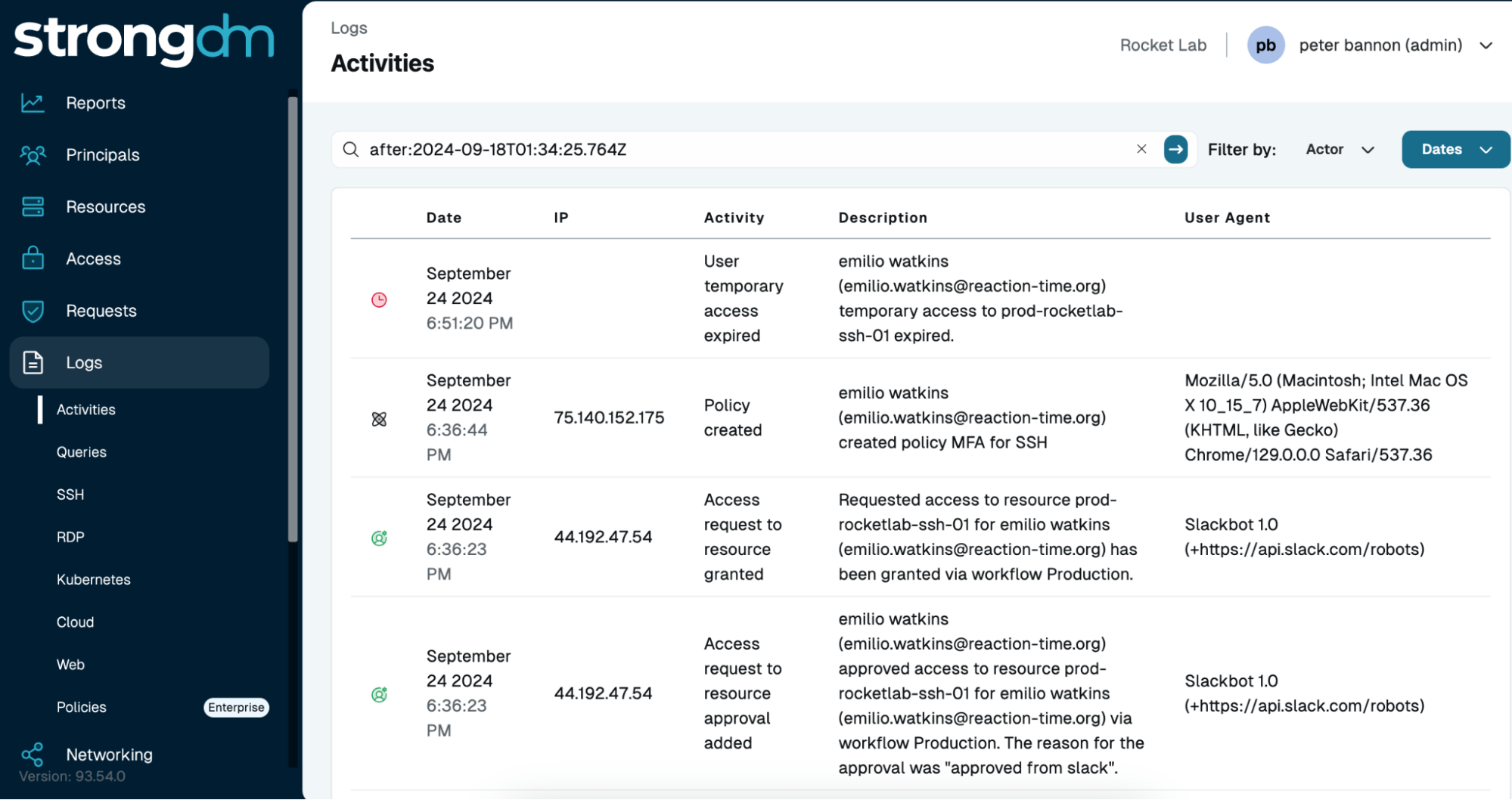
Comprehensive Threat Detection
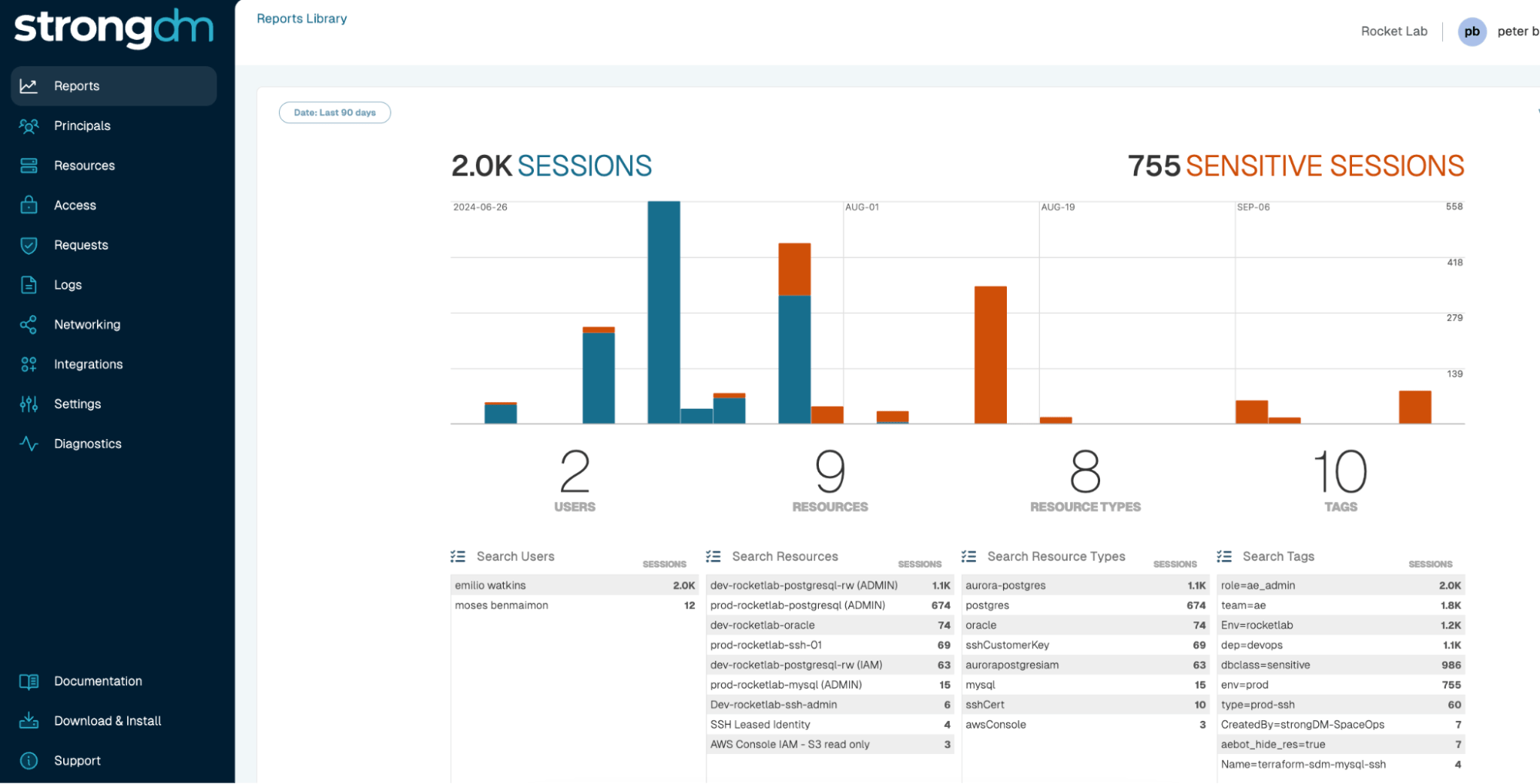
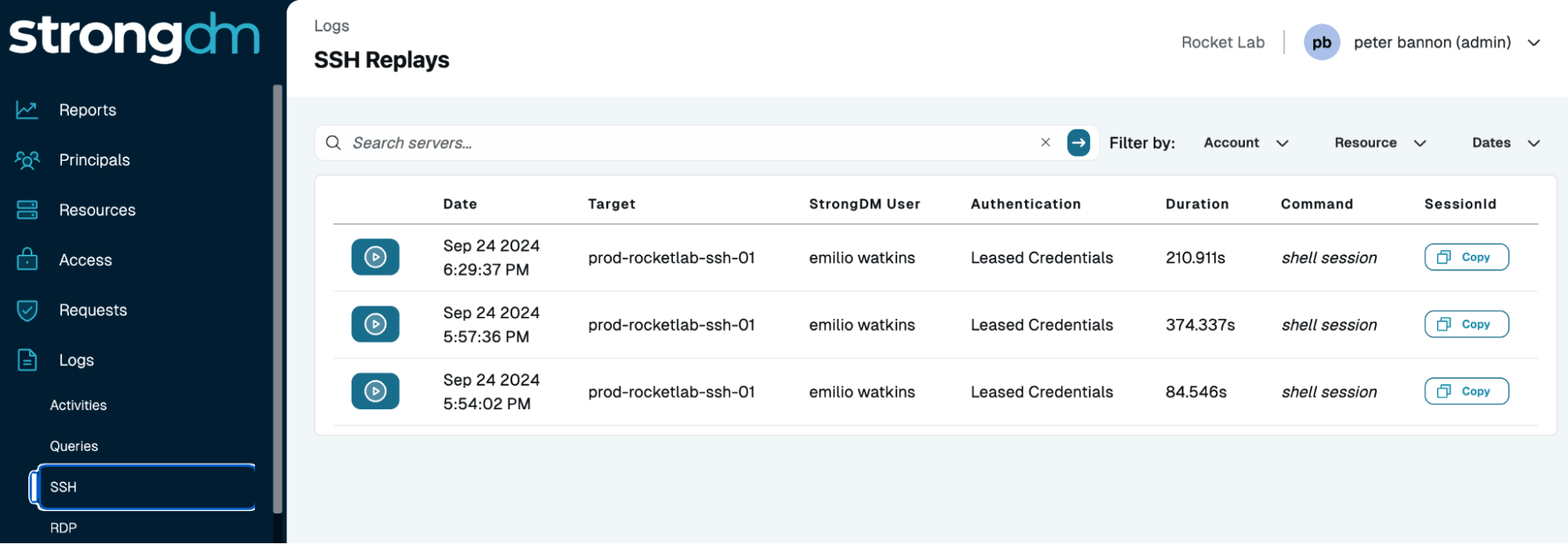
Detailed Audit Trails for Compliance
StrongDM vs. Alternatives
Alternatives |
StrongDM |
|
Real-Time Access Insights |
Real-Time Access Insights |
|
Granular Analytics |
Granular Analytics |
|
Threat Detection |
Threat Detection |
|
Unified View Across All Systems |
Unified View Across All Systems |
|
Seamless Data Lake Integration |
Seamless Data Lake Integration |
|
Automated Audit Logs |
Automated Audit Logs |
|
Just-in-Time Analytics |
Just-in-Time Analytics |


“Clearcover remains committed to the industry’s best security practices. StrongDM provides us with better insights to bolster our security posture.”
Helpful Resources

StrongDM Brought PAM Back to Life
StrongDM Architecture Overview

How Zero Trust PAM Defines Modern Enterprise Security
Connect your first server or database in 5 minutes. No kidding.
Free for 14 days. No credit card required.