Secure Access Governance
StrongDM Zero Trust PAM enforces adaptive policies for secure and compliant real-time access control.

Leading global brands rely on StrongDM

Eliminate Siloed Access
Fragmented systems create access silos, hindering visibility and control across applications and data, creating compliance risk.
5x
Faster to gather evidence for audits
70%
Reduction in number of engineers with admin rights
6x
Reduced time to identify and respond to incidents
0
Shared credentials with credential-less access for your end users
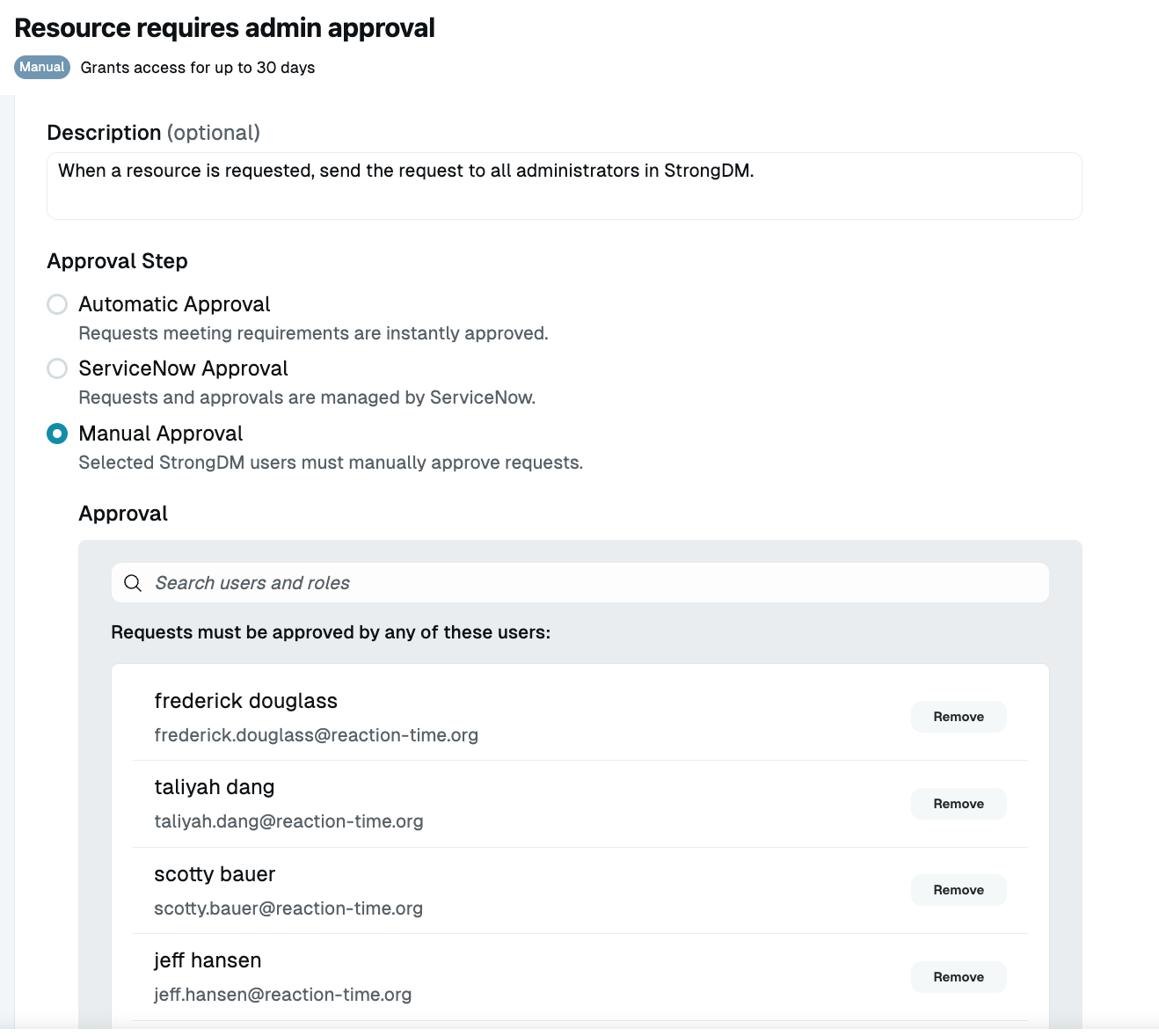
Policy-Based Access, Simplified
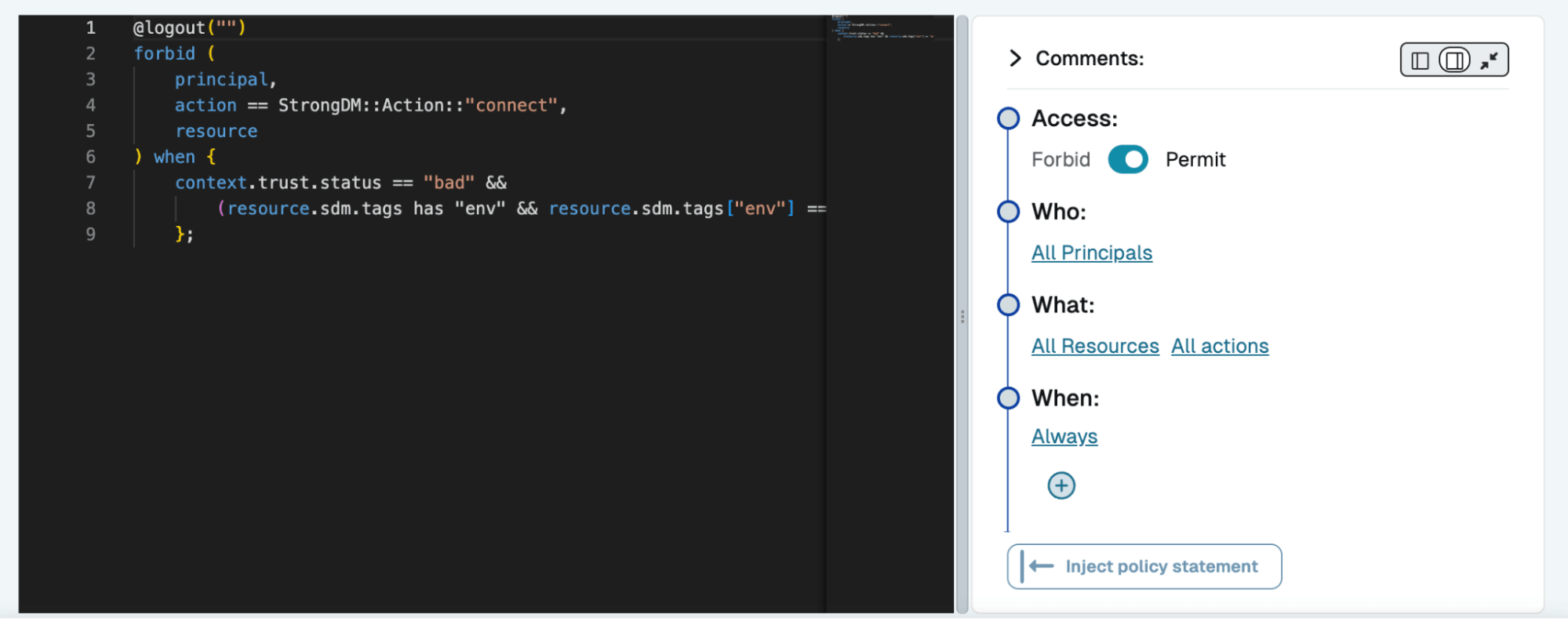
Streamlined Secure Workflows
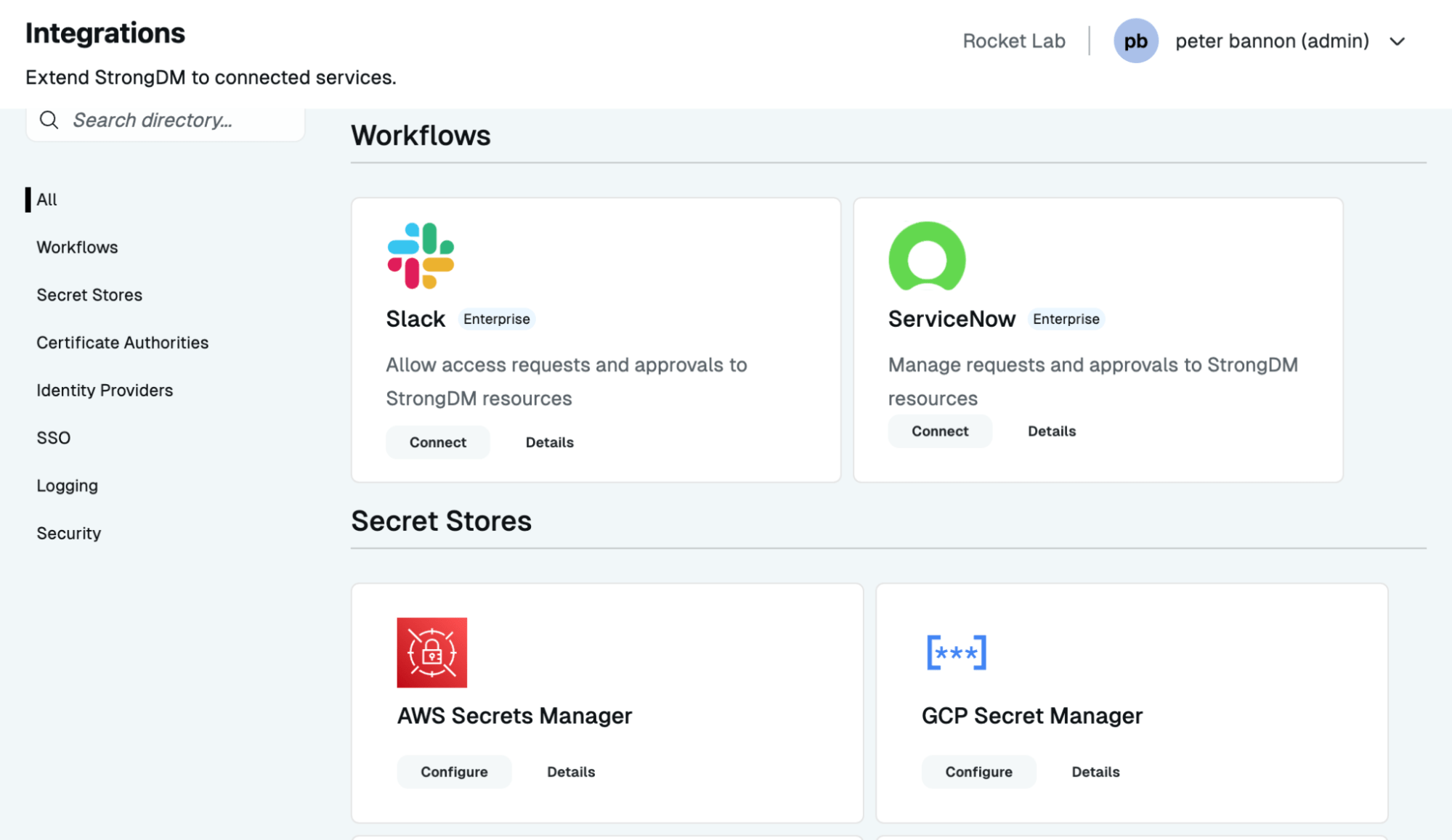
Flexible Access with Open APIs
StrongDM vs. Alternatives
Alternatives |
StrongDM |
|
Policy-Based Action Control |
Policy-Based Action Control |
|
Real-Time Policy Enforcement |
Real-Time Policy Enforcement |
|
Customizable Workflows |
Customizable Workflows |
|
Just-in-Time Access |
Just-in-Time Access |
|
Open APIs for Integration |
Open APIs for Integration |
|
Centralized Access Management |
Centralized Access Management |
|
Dynamic Policy Adaptation |
Dynamic Policy Adaptation |


“The biggest impact of rolling out StrongDM has been that it's been a boon for compliance and regulatory adherence, as well as freeing the data in a way as it's much easier to access now.”
Helpful Resources

StrongDM Brought PAM Back to Life
StrongDM Architecture Overview

How Zero Trust PAM Defines Modern Enterprise Security
Connect your first server or database in 5 minutes. No kidding.
Free for 14 days. No credit card required.