Frustration-Free Access Management
From RBAC and Just-in-Time access to Zero Standing Privileges, StrongDM delivers policy-driven security that ensures only the right people have access, at the right time.

Leading global brands rely on StrongDM

Eliminate Standing Access
Traditional access management often relies on manual processes, leaving temporary permissions in place longer than needed. This delay results in unnecessary standing access, increasing the risk of misuse or breaches. StrongDM automates Just-In-Time (JIT) access, granting privileges only when needed and revoking them immediately after use.
5x
Faster to gather evidence for audits
70%
Reduction in number of engineers with admin rights
6x
Reduced time to identify and respond to incidents
0
Shared credentials with credential-less access for your end users
Easy Just-in-Time Access
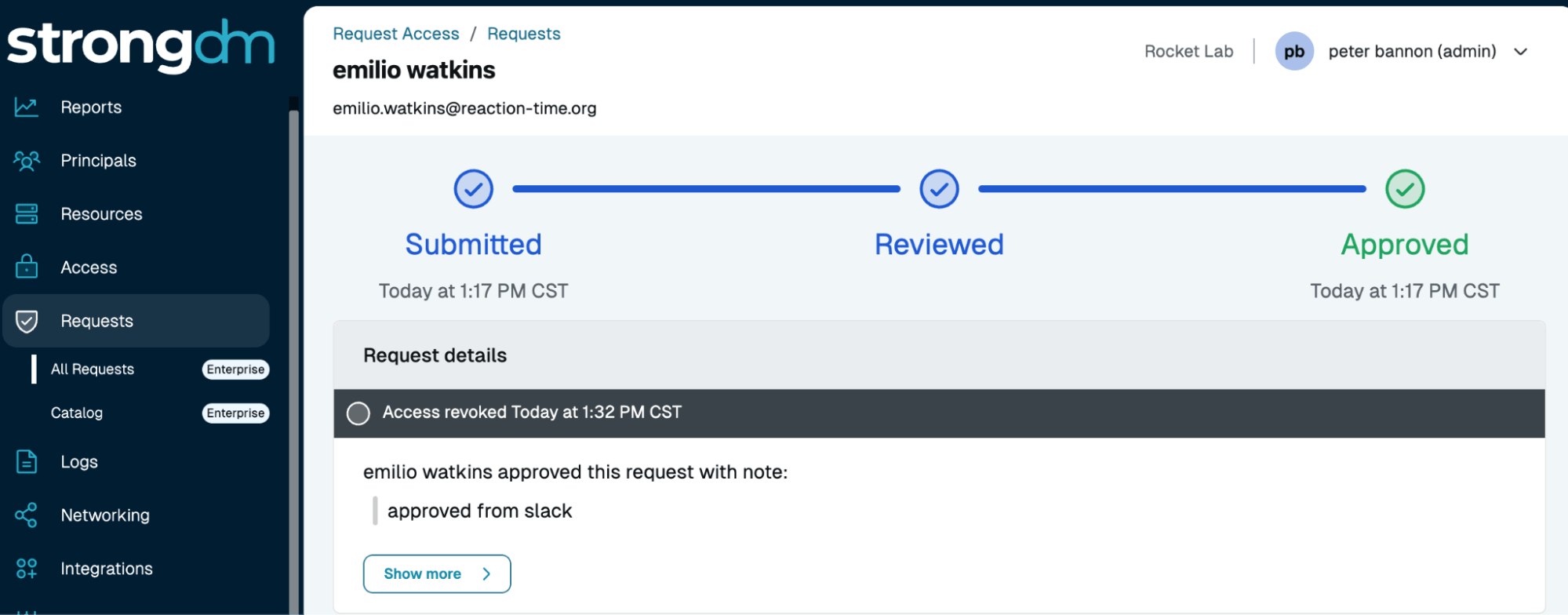
Dynamic, Policy-Driven Control
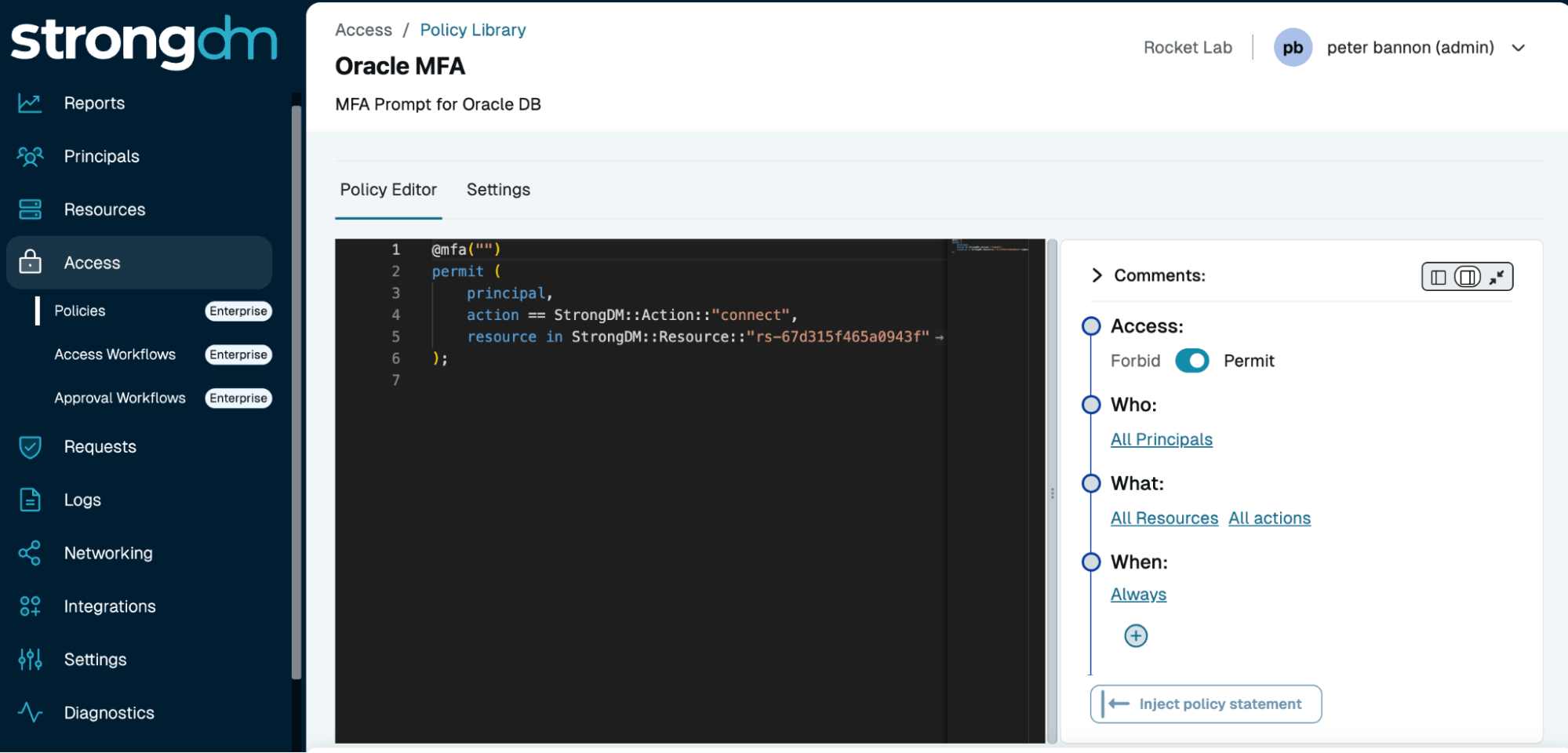
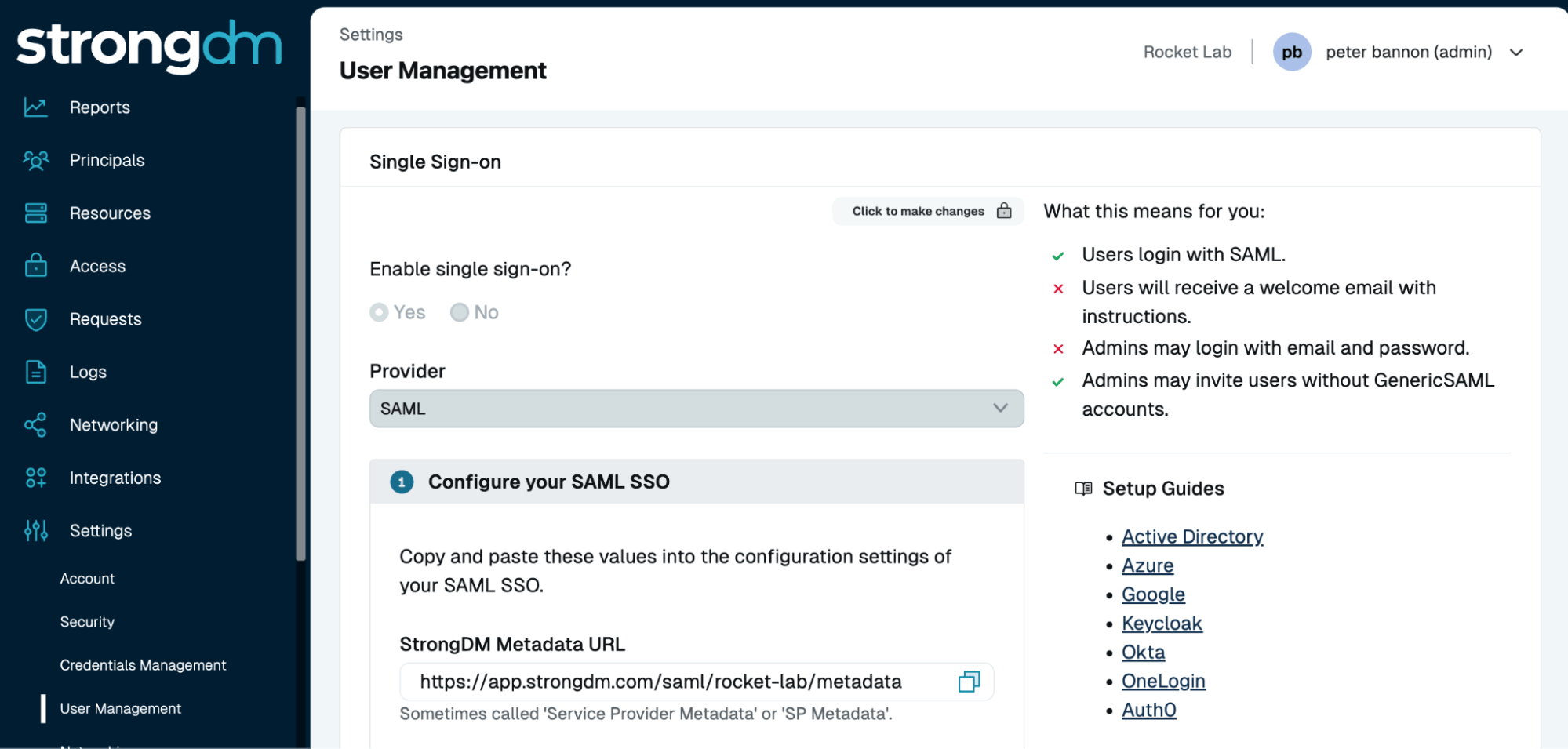
Streamlined Automation
StrongDM vs. Alternatives
Alternatives |
StrongDM |
|
Policy-Based Action Control |
Policy-Based Action Control |
|
Just-in-Time Access |
Just-in-Time Access |
|
Zero Standing Privileges |
Zero Standing Privileges |
|
Granular Control Over User Actions |
Granular Control Over User Actions |
|
Centralized Access for All Systems |
Centralized Access for All Systems |
|
Automated Access Provisioning |
Automated Access Provisioning |
|
Real-Time Policy Updates |
Real-Time Policy Updates |
|
Visibility and Auditing |
Visibility and Auditing |


“We chose StrongDM because the solution is the one solution to rule them all. You simply integrate all your data sources into StrongDM; you integrate all your servers into StrongDM; you integrate all your Kubernetes clusters into StrongDM. You give your developers one simple tool they need to connect using SSO, and they have access to what they own.”
Helpful Resources

StrongDM Brought PAM Back to Life
StrongDM Architecture Overview

How Zero Trust PAM Defines Modern Enterprise Security
Connect your first server or database in 5 minutes. No kidding.
Free for 14 days. No credit card required.