Adaptive Policy-Based Access Management Solution
Enable precise, dynamic access control with policies that adapt in real time to changing roles, resources, and security requirements, ensuring the right users have the right access at the right time.

Leading global brands rely on StrongDM

Dynamic, Real-Time Access Control
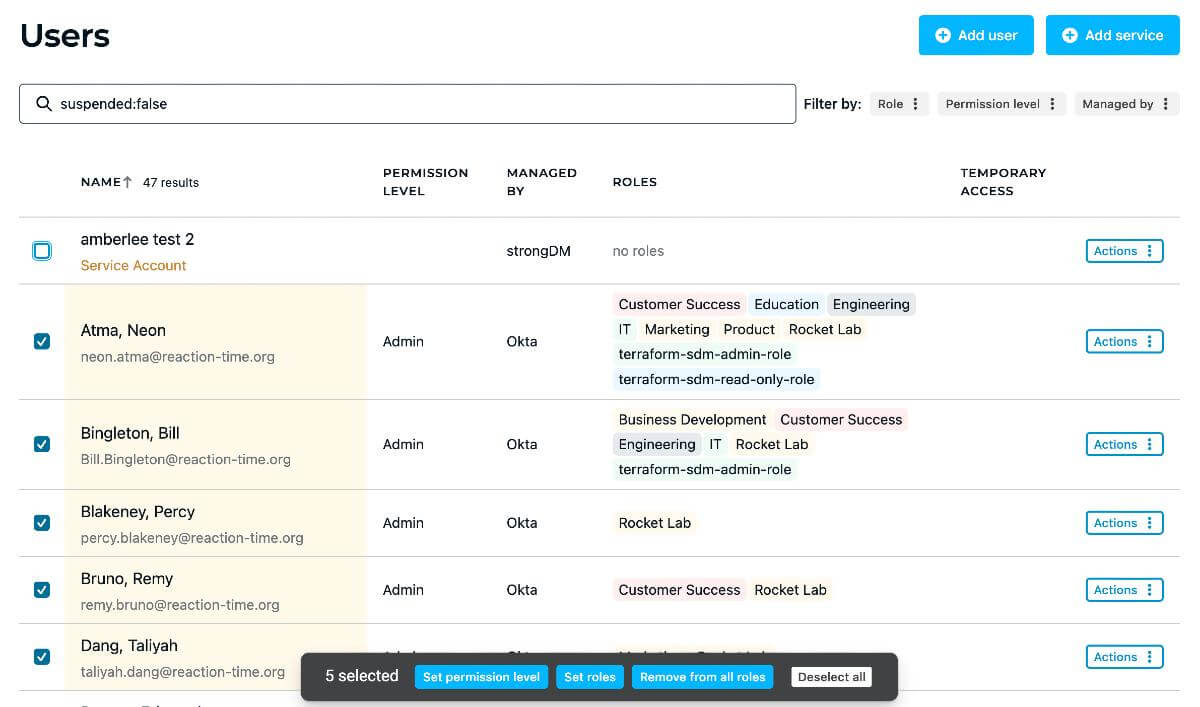
Simplified Compliance and Audit Readiness
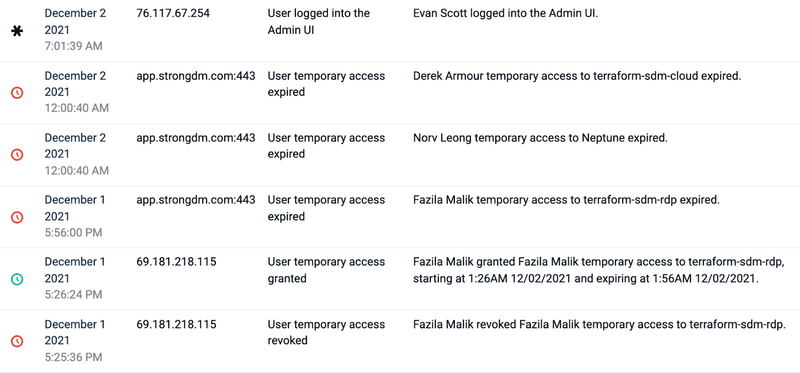

"Access is automatically assigned, and it’s easy to get new engineers up and running. From the access control perspective, that is ultimately the area that has helped us out the most. And just being able to see everybody’s queries against the database, with that granular auditing–I can’t stress enough that it was a big win."
Adaptive Policy-Based Authorization Compliance Alignment
Adaptive Policy-Based Authorization aligns with compliance frameworks such as NIST SP 800-53 and ISO 27001, which emphasize dynamic access controls and the enforcement of the principle of least privilege.
By implementing adaptive, policy-driven access management, organizations can ensure that access permissions are granted based on real-time evaluations of user attributes and contextual factors, thereby meeting stringent compliance requirements.
StrongDM's Zero Trust PAM platform facilitates this alignment by providing a centralized policy engine that automates and enforces fine-grained access controls across your entire infrastructure, ensuring continuous compliance and robust security.
Modernize Access Control Beyond Legacy PAM
Legacy PAM solutions rely on static, manual policies that can’t keep up with the speed and complexity of modern IT environments.
Adaptive Policy-Based Authorization automates dynamic, real-time access decisions, ensuring precise control, reducing operational overhead, and eliminating the security gaps that outdated tools leave behind.
Enhance Your Existing PAM with Adaptive Control
Adaptive Policy-Based Authorization augments legacy PAM solutions by introducing dynamic, real-time access controls that adjust to changing roles, resources, and contexts.
This added layer of automation and precision ensures least privilege enforcement, reduces manual effort, and fills critical gaps in access management without disrupting your existing infrastructure.
A Tailored Solution Just for Your Organization
Your technology stack is unique. Whether your infrastructure spans multiple clouds, utilizes diverse databases, or relies on critical applications, StrongDM seamlessly integrates with technologies you trust.
StrongDM is designed to fit your environment, not the other way around.











See StrongDM in action. 👀