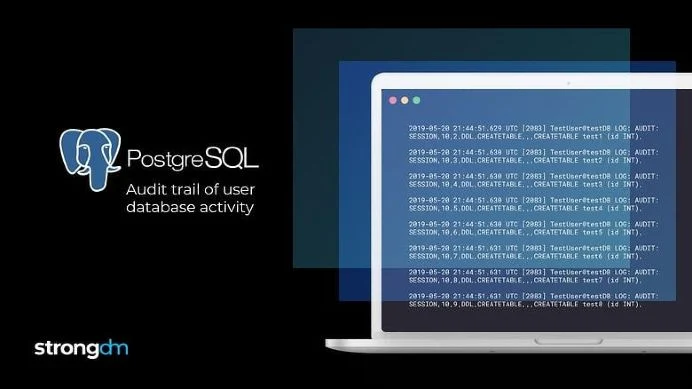
Modern tech stacks hum with resources galore: DBs, servers, clusters, web apps, clouds–the list goes on and on. Maintaining logs on hundreds of instances can make getting answers feel like a logistical nightmare.
When auditors need evidence, or an incident needs investigating, you can’t afford delays in tracking down logs. StrongDM delivers total visibility into every action on every system, so you have crisp answers to access control questions across your entire backend infrastructure.
Track and secure every privileged account
Don’t let failed compliance audits hurt your business. Give Security and Compliance teams faster answers to who did what, where, and when.
Generate and store all access and activity logs to ensure that customers and stakeholders have confidence in your security practices.

See into every action on every system
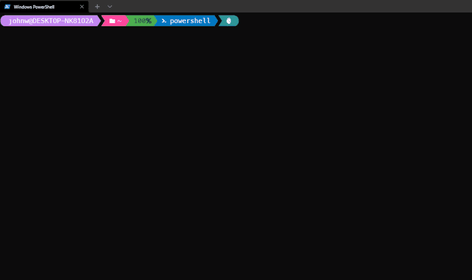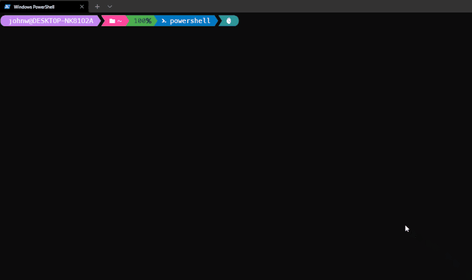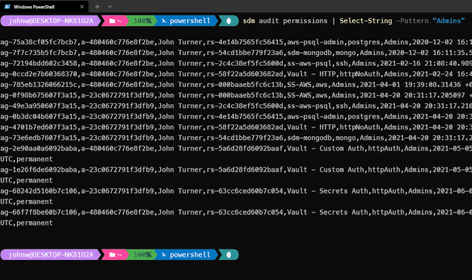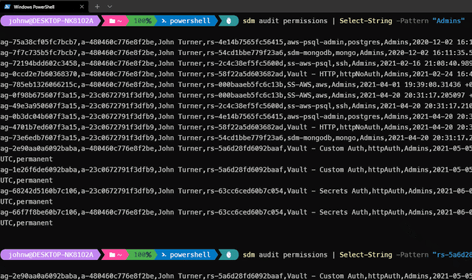
Track all events, including permission changes and operations. Capture every session, query, and command across your entire infrastructure.
Review logs to see admin activities, queries, live replays of SSH or RDP sessions, and even search within these captured sessions.
Logging and reporting, the way you like it
You have full control over where your logs are stored and how they’re encrypted.
Consolidate your access audit logs with StrongDM, log locally, or ship to a SIEM, SOAR, or log aggregation tool to develop a clear picture of access risk.
For security analysis, SOC 2, and HIPAA compliance, we need to be aware of all the operations that happen inside an environment. We need the ability to audit everything. We need the ability to go back and see what happened on a specific instance, the ability to go back and see the queries on a given day. The audit trail using StrongDM’s gateway is way more efficient than configuring each data source one by one.”
Jean-Philippe Lachance
Team Lead - R&D Security Defense, Coveo


Dream More. Deliver More.
_Leader_Leader-2.png?width=125&height=162&name=PrivilegedAccessManagement(PAM)_Leader_Leader-2.png)
_BestSupport_QualityOfSupport-1.png?width=125&height=162&name=IdentityandAccessManagement(IAM)_BestSupport_QualityOfSupport-1.png)
_BestEstimatedROI_Mid-Market_Roi-2.png?width=125&height=162&name=IdentityandAccessManagement(IAM)_BestEstimatedROI_Mid-Market_Roi-2.png)
_MomentumLeader_Leader-1.png?width=125&height=162&name=PrivilegedAccessManagement(PAM)_MomentumLeader_Leader-1.png)
_HighPerformer_HighPerformer.png?width=125&height=162&name=IdentityandAccessManagement(IAM)_HighPerformer_HighPerformer.png)






See StrongDM in action. 👀