Granular Access Controls Solution
Achieve secure, granular access across all resources with policy-based controls that empower teams to define, enforce, and audit specific permissions and actions in real-time, minimizing risk and ensuring compliance at every level.

Leading global brands rely on StrongDM

Precise Control with Policy-Based Permissions
Streamlined Compliance Management
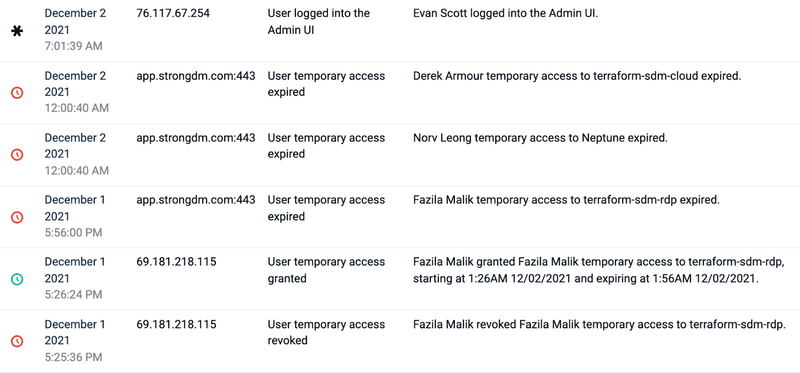

“Remaining in compliance and auditing is another benefit. We are able to share data from StrongDM with auditors and show that we have temporary access within our defined limits, with the ability to get more granular by defining roles by geography... Showing that people from this location aren't accessing data from another location.”
Compliance Framework
SOC 2 and NIST CSF strongly emphasize granular access control as a core part of secure information management.
Granular access control within a Zero Trust PAM solution enhances SOC 2 and NIST CSF compliance by providing precise, policy-based permissions that restrict access to only necessary resources.
This approach not only reduces security risks but also simplifies the compliance process, enabling real-time monitoring and a clear audit trail that strengthens accountability and facilitates efficient audits.
Legacy Replacement
Replacing legacy PAM with granular, policy-based controls lets companies set precise permissions across all resources, enhancing security with enforced least-privilege access and streamlined compliance.
Real-time monitoring and centralized audits make access tracking effortless in dynamic environments, eliminating the limitations of traditional PAM solutions.
Legacy Augmentation
Enterprises can augment their legacy PAM with granular, policy-driven access control which add precision to access management, helping organizations enforce least-privilege access, streamline compliance, and minimize risk.
This elevates security standards with real-time monitoring and centralized auditing capabilities to track access and ensure accountability across all resources.
A Tailored Solution Just for Your Organization
Your technology stack is unique. Whether your infrastructure spans multiple clouds, utilizes diverse databases, or relies on critical applications, StrongDM seamlessly integrates with technologies you trust.
StrongDM is designed to fit your environment, not the other way around.











See StrongDM in action. 👀