Privileged Access Management for Databases Solution
Effortlessly control, monitor, and secure privileged access to all your databases, ensuring robust security and compliance without disrupting workflow.

Leading global brands rely on StrongDM

Centralized Access Control
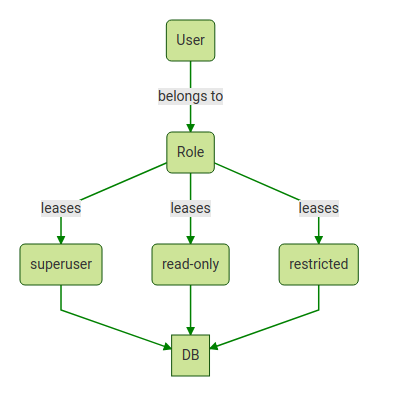
Action Control for Precise Database Governance

"With our previous PAM, we had session recordings, but they were only so useful—nobody was going to sit through hours of footage to figure out what code execution that they typed up (or most likely copy and pasted) into their query field (a motion that is not recorded as a keystroke in Legacy PAM solutions). But with StrongDM, we know exactly what's being done on the databases. StrongDM captures every query and keystroke, which has been huge for us from a compliance perspective."
Compliance Framework
StrongDM’s PAM for Databases helps organizations align with ISO 27001 and SOC 2 by providing centralized, automated control over database permissions.
This feature ensures that only authorized users can access sensitive database information, while real-time monitoring and audit trails simplify compliance reporting.
With robust access management tailored to databases, StrongDM strengthens data security and helps maintain compliance with key industry standards effortlessly.
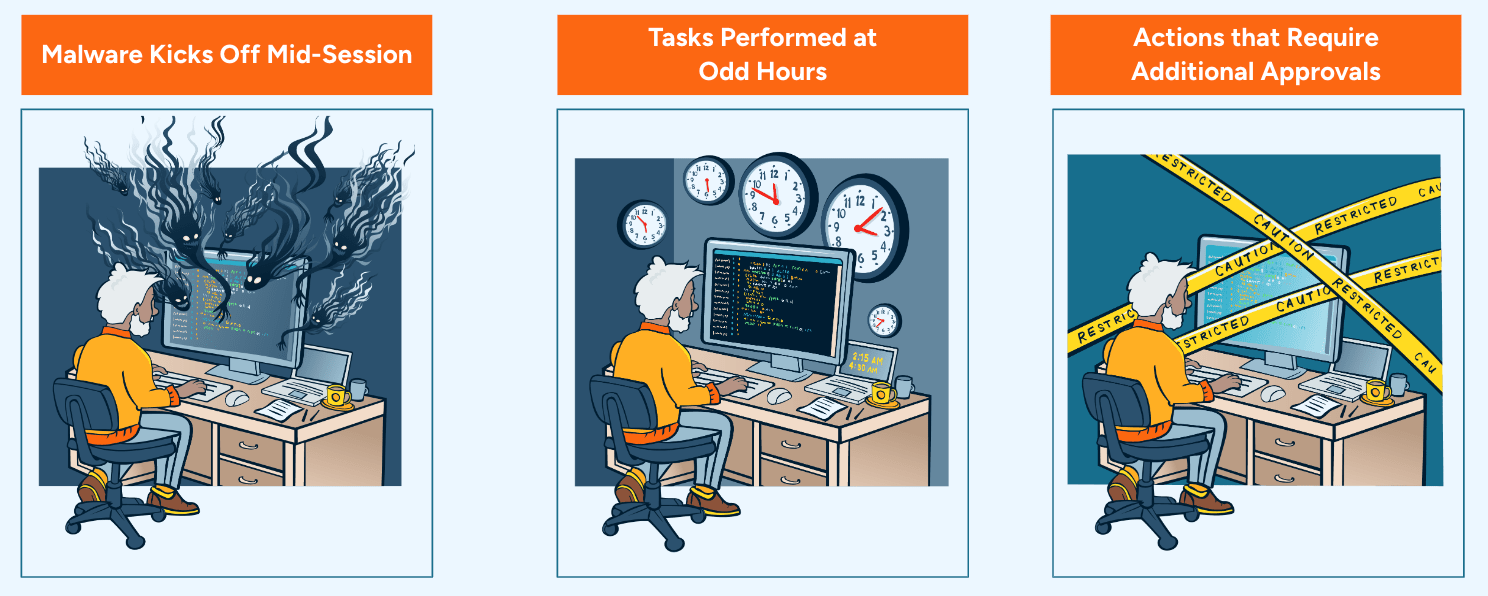
Legacy Replacement
StrongDM’s PAM for Databases capabilities offer a transformative improvement over legacy PAM systems, which often struggle with static controls and limited database visibility.
Unlike traditional solutions, StrongDM centralizes and automates permission management across all database types, enabling real-time monitoring, secure credential vaulting, and seamless compliance reporting.
This enhanced functionality reduces the risk of unauthorized access and simplifies database security management, providing a scalable and efficient alternative to outdated PAM tools.
Legacy Augmentation
For companies seeking to enhance their legacy PAM solutions, PAM for Databases offers real-time monitoring, automated permissions, and secure credential vaulting across all database environments.
Integrating these capabilities enables organizations to add centralized access control and streamlined compliance reporting, significantly reducing security risks without needing a full system replacement.
This upgrade provides strong, scalable database security in alignment with modern compliance requirements, empowering organizations to maintain seamless and robust protection for critical data.
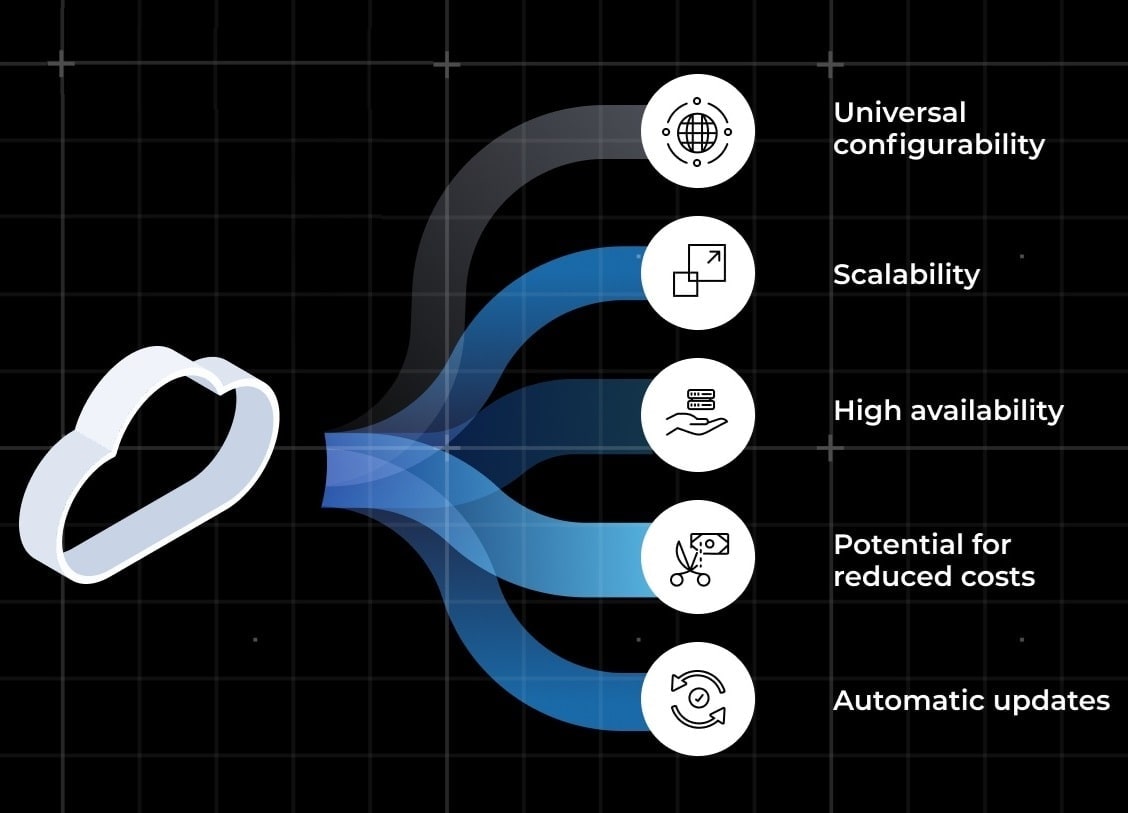
A Tailored Solution Just for Your Organization
Your technology stack is unique. Whether your infrastructure spans multiple clouds, utilizes diverse databases, or relies on critical applications, StrongDM seamlessly integrates with technologies you trust.
StrongDM is designed to fit your environment, not the other way around.











See StrongDM in action. 👀