Privileged Access Management for Servers Solution
Enable secure, flexible access management for servers, with fine-grained permissions, real-time monitoring, and comprehensive audit trails to ensure compliance and minimize risk across cloud, on-prem, and hybrid environments.

Leading global brands rely on StrongDM

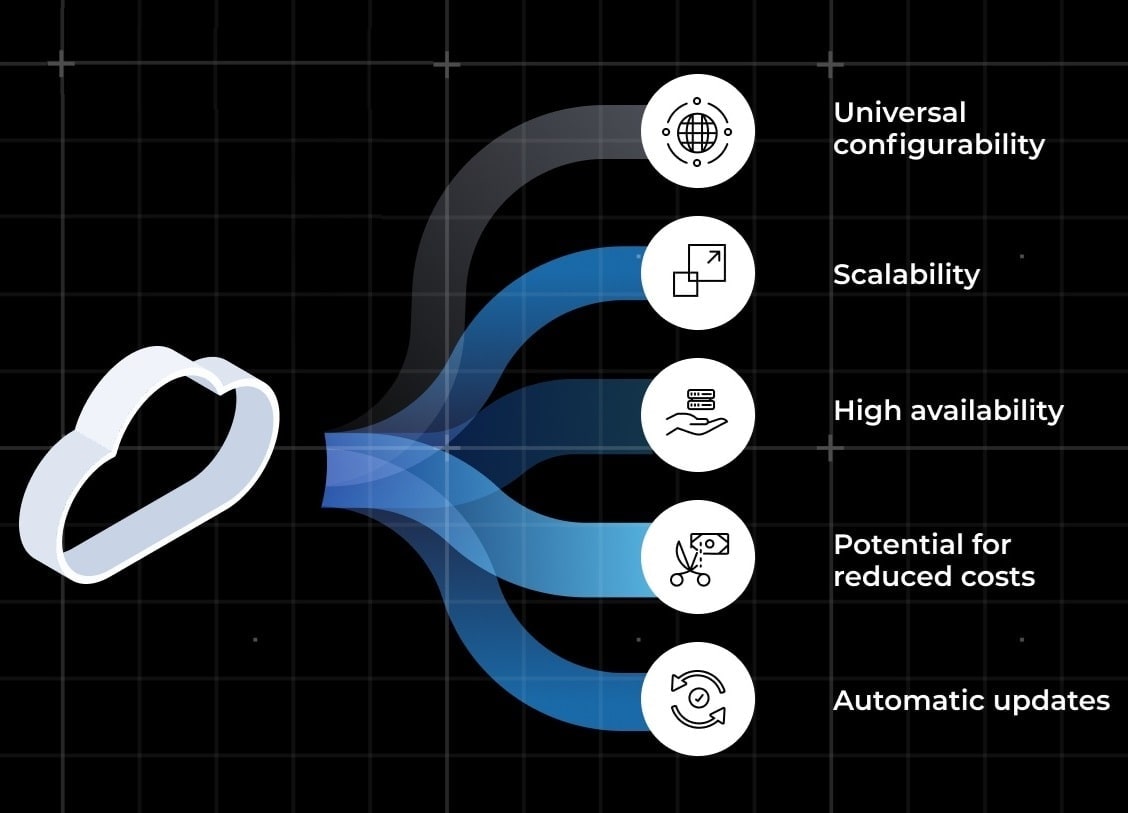
Consistent Access Control Across All Servers
Automated Credential Management

"We chose StrongDM because the solution is the one solution to rule them all. You simply integrate all your data sources into StrongDM; you integrate all your servers into StrongDM; you integrate all your Kubernetes clusters into StrongDM. You give your developers one simple tool they need to connect using SSO, and they have access to what they own."
Compliance Framework
StrongDM aligns with ISO 27001 compliance requirements, offering security teams centralized access control, enforceable least-privilege policies, and detailed activity logs essential for auditing.
This approach addresses key sections of ISO 27001, such as access management and compliance mandates by delivering a single, cohesive system to manage and secure privileged access across on-premises, cloud, and hybrid servers.
Legacy Replacement
For companies moving beyond legacy PAM, Zero Trust PAM for servers provides a unified approach to access management, enhancing control, visibility, and security across on-prem, cloud, and hybrid environments.
With real-time monitoring, enforceable least-privilege policies, and centralized credential management, this solution eliminates the operational gaps and manual burden left by outdated systems, enabling agile, compliant, and secure server access at scale.
Legacy Augmentation
Strengthen your existing PAM solution by adding unified, real-time server access management and centralized monitoring. Zero Trust for servers complements legacy systems, closing security gaps, enhancing visibility, securing credentials, and ensuring compliance without disrupting current workflows.
A Tailored Solution Just for Your Organization
Your technology stack is unique. Whether your infrastructure spans multiple clouds, utilizes diverse databases, or relies on critical applications, StrongDM seamlessly integrates with technologies you trust.
StrongDM is designed to fit your environment, not the other way around.











See StrongDM in action. 👀