Enterprise Privileged Credential Management Solution
Automate the management, rotation, and security of privileged credentials, ensuring continuous protection and compliance without manual hassle.
Leading global brands rely on StrongDM


Automated Credential Rotation
Stop relying on manual processes to manage privileged credentials. This feature automatically rotates passwords and keys on a schedule, reducing the risk of misuse or compromise. You ensure credentials are always fresh and secure without the time-consuming upkeep.
Learn more about SrongDM's credentials and secrets management.

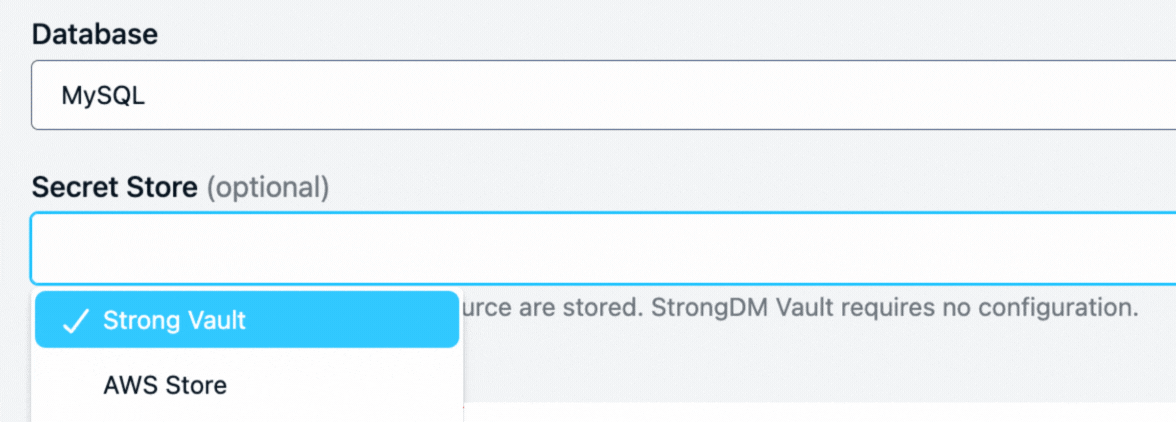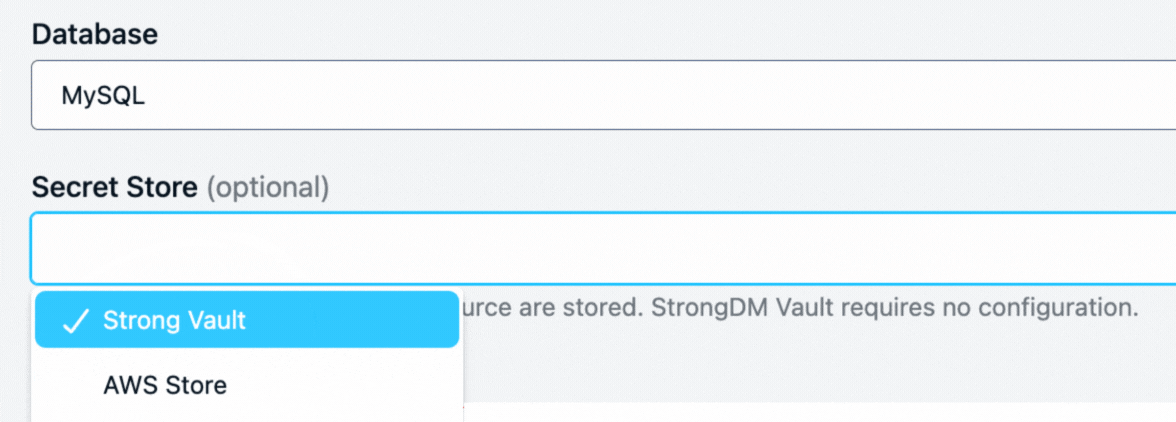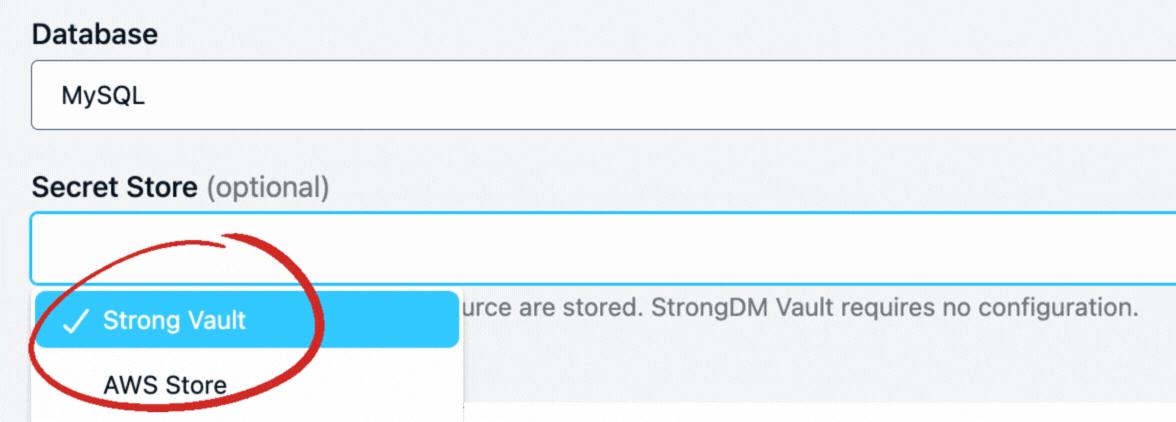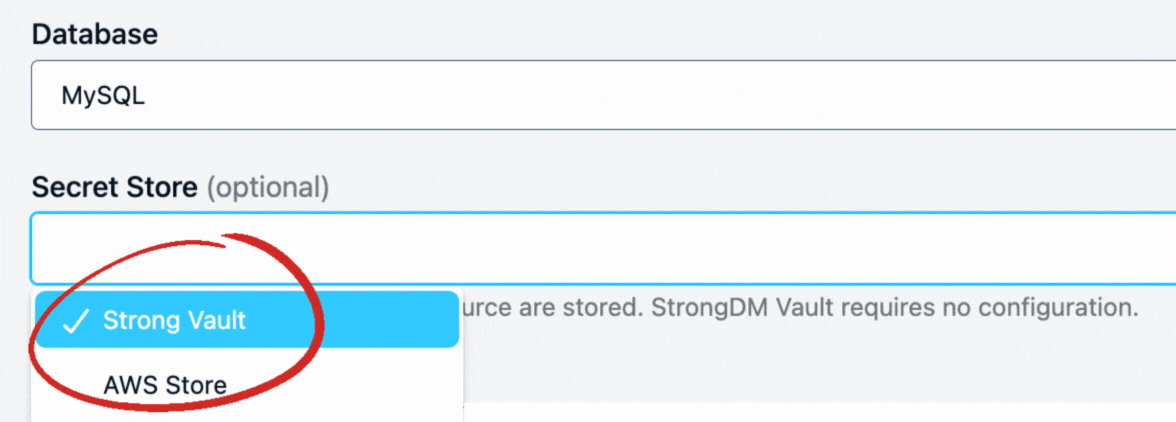
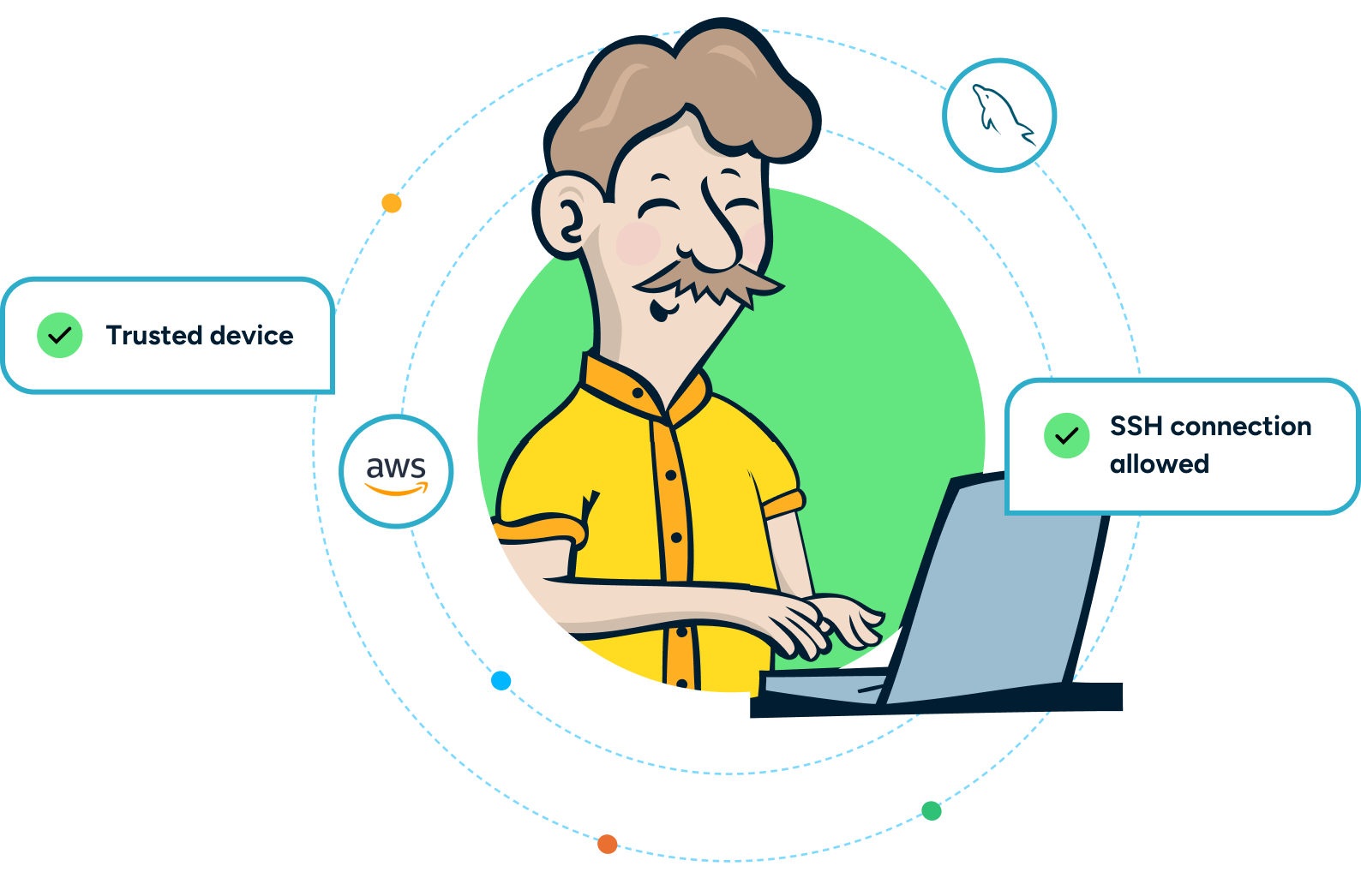
Secure Vaulting for Sensitive Accounts
Privileged credentials are securely vaulted, preventing unauthorized access and reducing the risk of credential theft. With this feature, even administrators don’t need to know or see the credentials, providing an extra layer of security for your most sensitive accounts.
Real-Time Access Control
Immediately grant or revoke access to privileged credentials as needed, ensuring that only authorized users have the right permissions at the right time.
This real-time control minimizes security gaps and enables you to respond quickly to any changes in personnel or access requirements.


“The access control has helped us out the most. And with audit logging, it’s very easy for the auditors to see what queries are being run by a particular person at a particular time. That granular level auditing – I can’t stress enough how big of a win it is.”
NIST 800-53 Compliance
StrongDM automates credential management to align with NIST 800-53 requirements, ensuring that privileged credentials are securely vaulted and regularly rotated. This reduces the risk of misuse and provides comprehensive audit trails for every access event, helping your organization meet the stringent access controls and oversight necessary for compliance.
ISO 27001
StrongDM simplifies compliance with ISO 27001 by automating the entire lifecycle of privileged credentials—securely vaulting, rotating, and managing access. With built-in audit trails and real-time monitoring, StrongDM ensures that your organization maintains continuous compliance with the high standards required for managing sensitive information and access control.
Credential Security for Legacy PAM Upgrades
StrongDM’s privileged credential management improves upon legacy PAM systems by automating key processes like credential vaulting and rotation. While legacy solutions often rely on manual, error-prone tasks, StrongDM provides real-time, automated credential management, enhancing security, reducing workload, and ensuring continuous compliance—all with minimal effort.
Enhance Your Legacy PAM with Automated Credential Management
StrongDM seamlessly augments your legacy PAM solution by automating critical functions like credential rotation and vaulting. Instead of relying on manual processes, which are slow and prone to errors, StrongDM introduces real-time automation that improves security and efficiency without requiring a full system replacement. This enhancement allows companies to keep their existing PAM systems while benefiting from advanced credential management capabilities.
A Tailored Solution Just for Your Organization
Your technology stack is unique. Whether your infrastructure spans multiple clouds, utilizes diverse databases, or relies on critical applications, StrongDM seamlessly integrates with technologies you trust.
StrongDM is designed to fit your environment, not the other way around.











See StrongDM in action. 👀


