Leading global brands rely on StrongDM

Saved per year onboarding and offboarding engineers to critical infrastructure.
Reduction in number of engineers with admin rights.
Reduced time to identify and respond to incidents.
Shared credentials with credential-less access for developers.






StrongDM helps eliminate standing access across all environments, ensuring your valuable assets are protected from unauthorized access—whether in development, production, on-premises or in the cloud.
Achieve robust security without sacrificing productivity.

Centralize access management with one solution that connects to cloud, databases, servers, clusters, and web applications, no matter what the environment.

Users no longer need to input keys and credentials to connect to their resources. Just log into StrongDM and connect, eliminating credential exposure and reducing the attack surface.
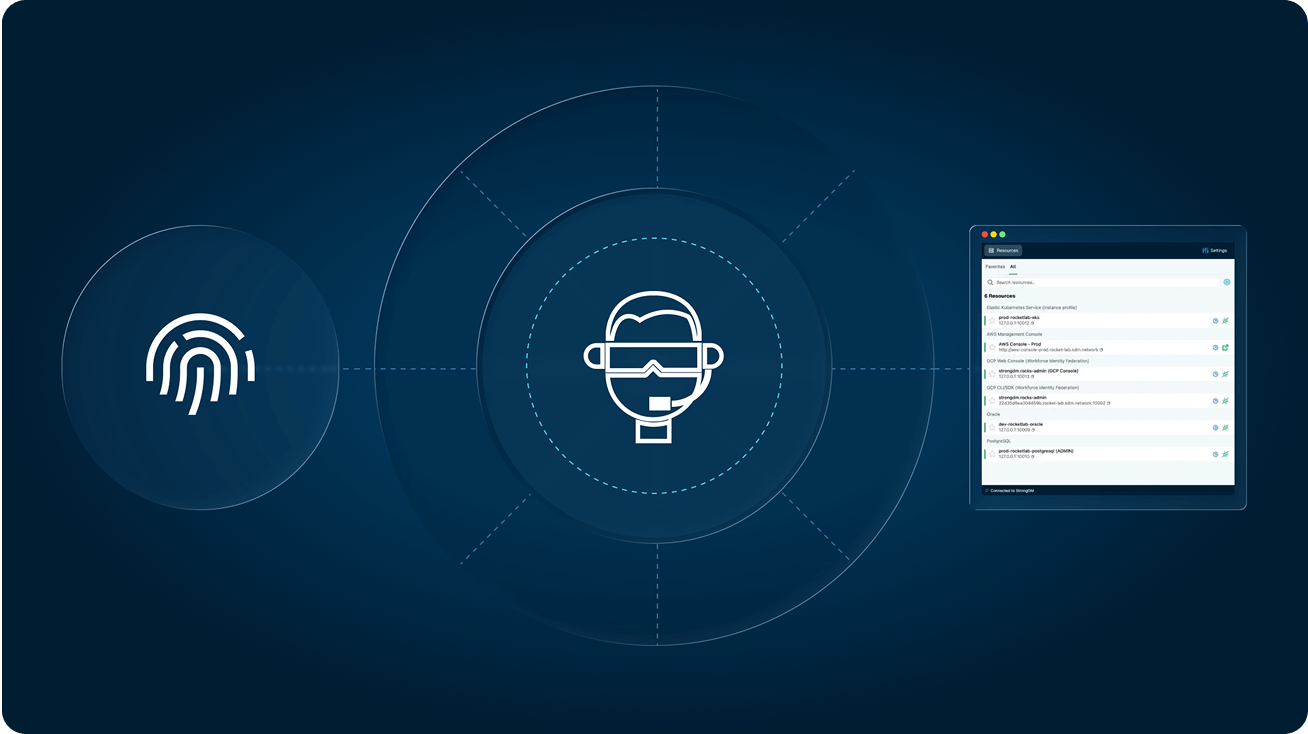
Eliminate unnecessary standing access to your resources on-premises and in the cloud. StrongDM makes Zero Standing Privileges a reality.
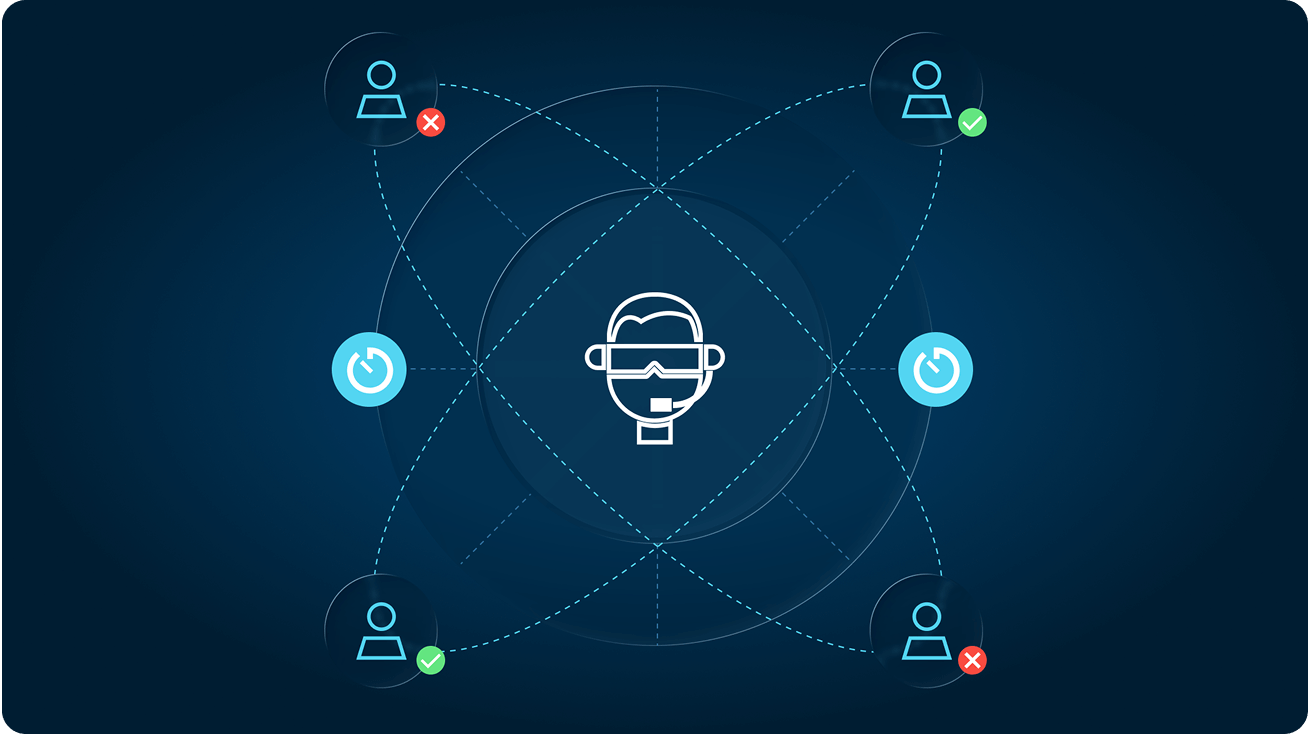
Enhance observability with a record of every activity and query, and improve mean-time-to-investigate (MTTI) and mean-time-to-respond (MTTR) to incidents.
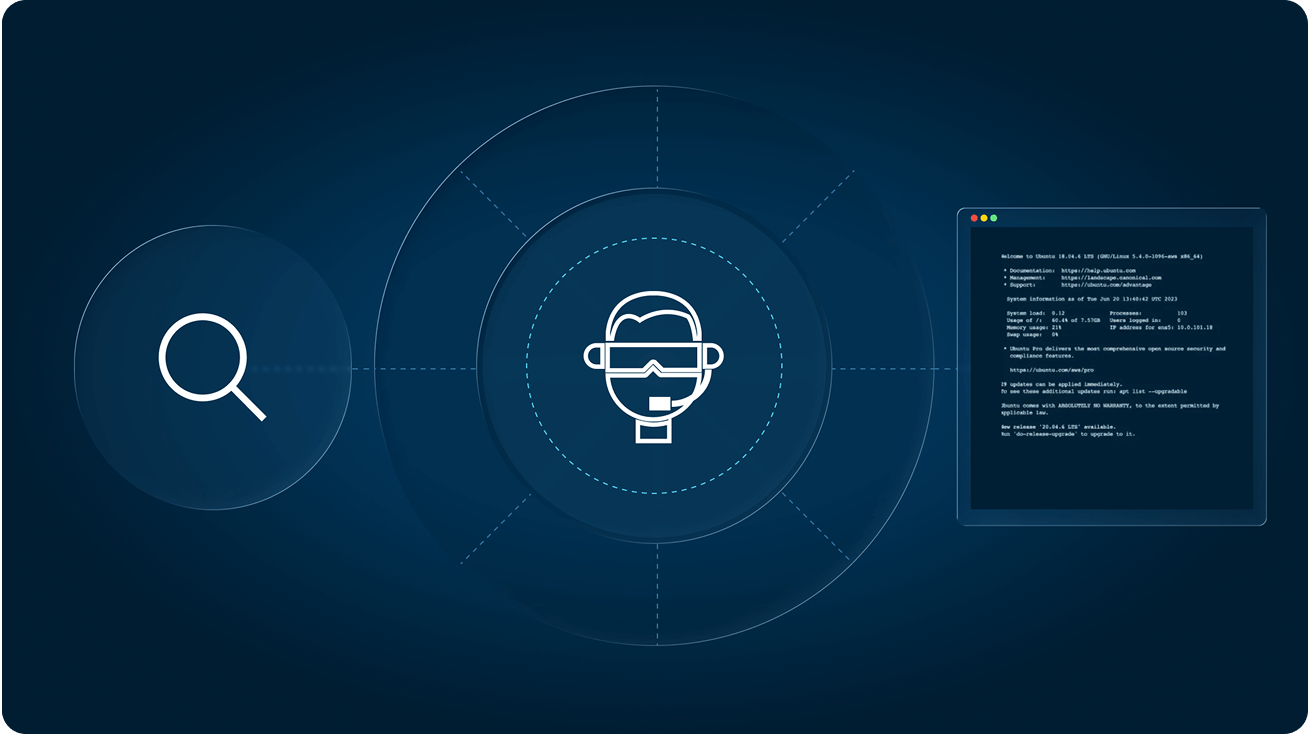
Access reports identify unused privileges, surface your most sensitive access grants, and so much more.



