Total Identity Control, Zero Access Friction








Is your privileged access management solution difficult to deploy, manage, and adopt?
5x
Faster to gather evidence for audits
70%
Reduction in number of engineers with admin rights
6x
Reduced time to identify and respond to incidents
0
Shared credentials with credential-less access for your end users



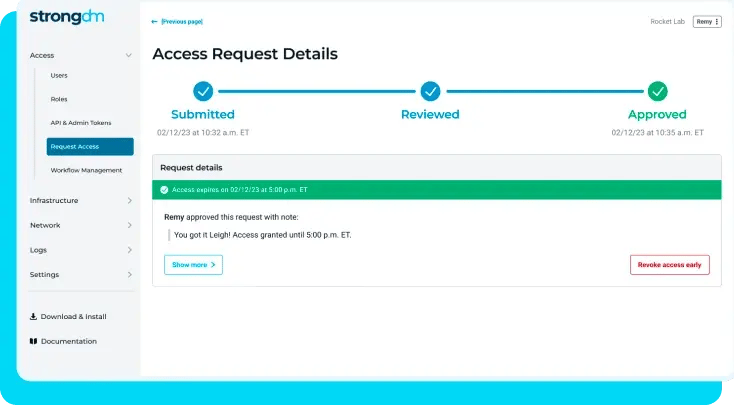


One PAM, all of your infrastructure
Easily connect users to every part of your infrastructure on-premises or in the cloud–with a solution that is easy to deploy, manage, and maintain.
Enforce security that doesn’t add complexity, ensuring that every technical employee adopts the security policies put in place. With complete control of privileged access, adhering to internal and external regulatory compliance has never been easier.

Break free from vendor shackles
With StrongDM you don’t need to be tied to a particular vendor. We have integrations across your identity and access management tech stack, so that your team can use the solutions they prefer.
Select the identity provider of choice. Store secrets in any or multiple vaults. Export logs to your preferred SIEM. With StrongDM’s integration-first approach, privileged access is managed all from a single platform.
Adopt Zero Standing Privileges
StrongDM enables security where legacy PAM solutions fall short. Enable just-in-time access for all resources and eliminate the need for standing access, forever.
Users only have access to what they need when they need it, no credentials required. Simply log into StrongDM and connect.

“The biggest impact of rolling out StrongDM has been that it's been a boon for compliance and regulatory adherence, as well as freeing the data in a way as it's much easier to access now.”
Dynamic access is the foundation for a Zero Trust strategy
- Supports every protocol
- Credential-less access
- Just-in-time all the time
- Granular audit logs
- Actionable Insights

Connect to everything you need
Centralize access management with one solution that connects to cloud, databases, servers, clusters, and web applications no matter what the environment.
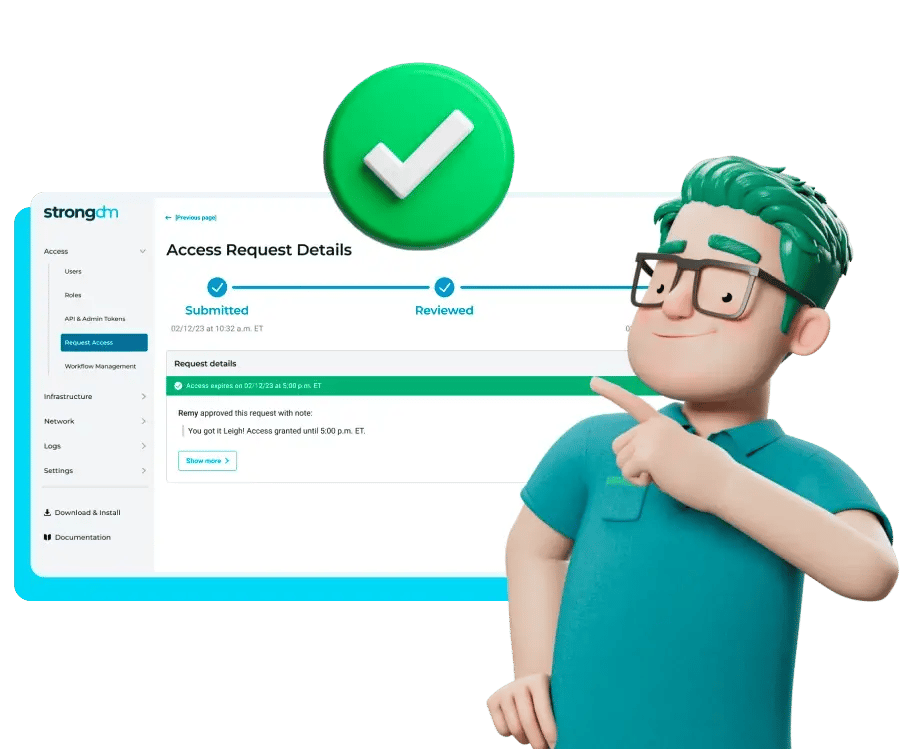
Keep your secrets safe
Users no longer need to input keys and credentials to connect to their resources. Just log into StrongDM and connect, eliminating credential exposure and reducing the attack surface.
JIT for legacy and cloud infrastructure
Eliminate unnecessary standing access to your resources on-premises and in the cloud. StrongDM makes Zero Standing Privileges a reality.
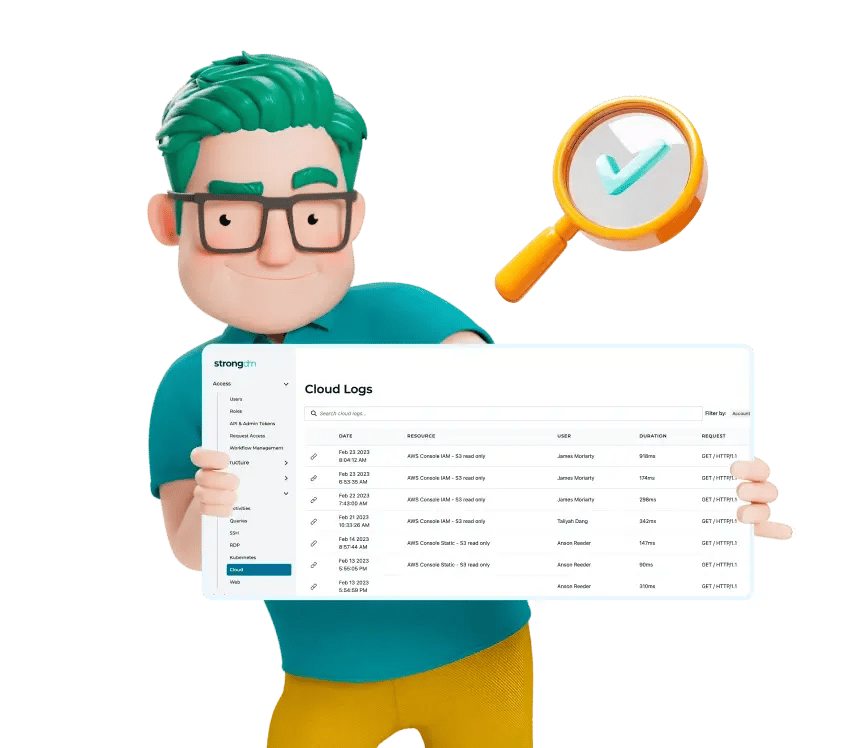
Capture every single key stroke
Enhance observability with a record of every activity and query, and improve mean-time-to-investigate (MTTI) and mean-time-to-respond (MTTR) to incidents.
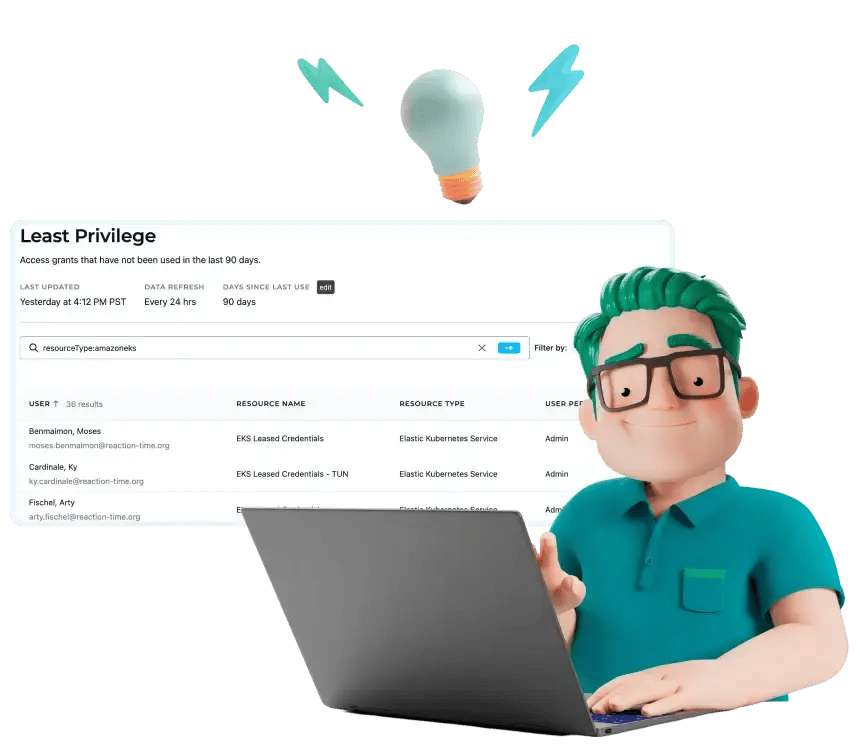
Quantify your access policies
Access reports identify unused privileges, surface your most sensitive access grants, and so much more.
Meet Compliance Standards
PCI Compliance Checklist: The 12 Requirements
.webp?width=1560&height=876&name=iso-27001-checklist-1%20(1).webp)
ISO 27001 Solution Guide
