Leading global brands rely on StrongDM

Faster to gather evidence for audits
Reduction in number of engineers with admin rights
Reduced time to identify and respond to incidents
Shared credentials with credential-less access for your end users

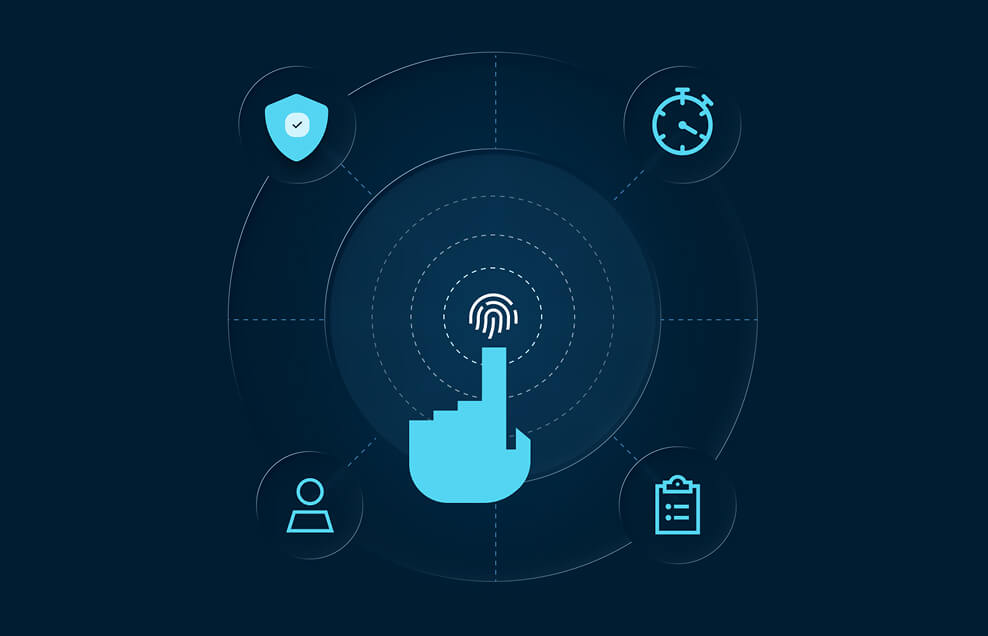

Privileged access solutions work best when you have visibility into every system for every user whether it is on-premises, in the cloud, or both
Legacy PAM solutions only works for part of your infrastructure. StrongDM extends PAM capabilities and centralizes access into one platform making it easy to understand who is accessing what, when, where, and why.

Credentials and access to critical infrastructure should only need to exist when it is needed.
With just-in-time access, end users don’t need standing credentials but still get the access they need, eliminating exposure and narrowing your attack surface.

Just-in-time access is a gap in legacy privileged access solutions, requiring standing permissions to exist that could be compromised.
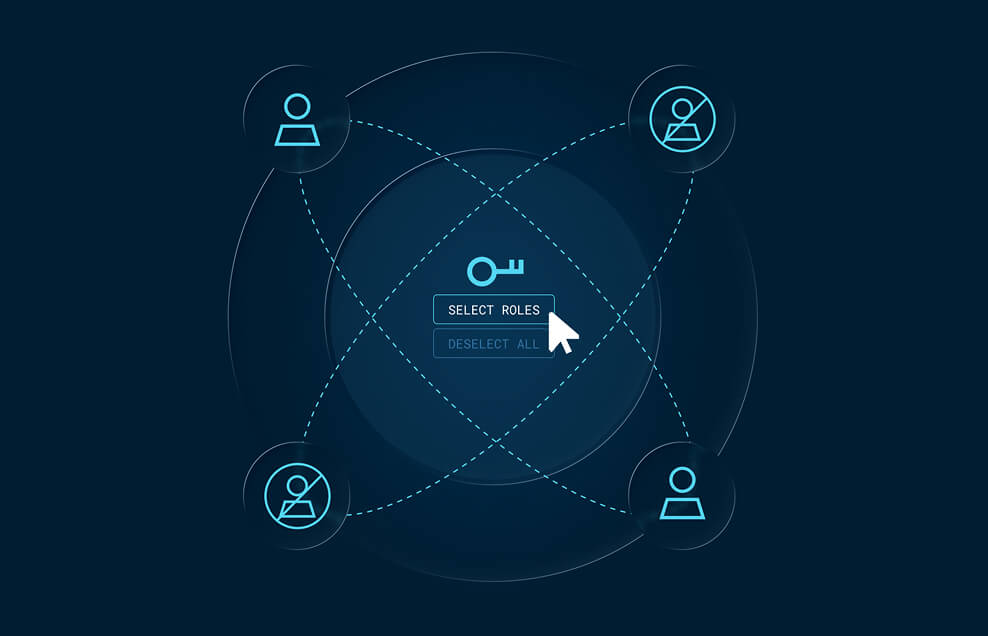
Eliminate the risk created by excessive static permissions with an enterprise-ready solution that provisions access by role, attribute, or just-in-time.

Centralize access management with one solution that connects to cloud, databases, servers, clusters, and web applications, no matter what the environment.

Users no longer need to input keys and credentials to connect to their resources. Just log into StrongDM and connect, eliminating credential exposure and reducing the attack surface.
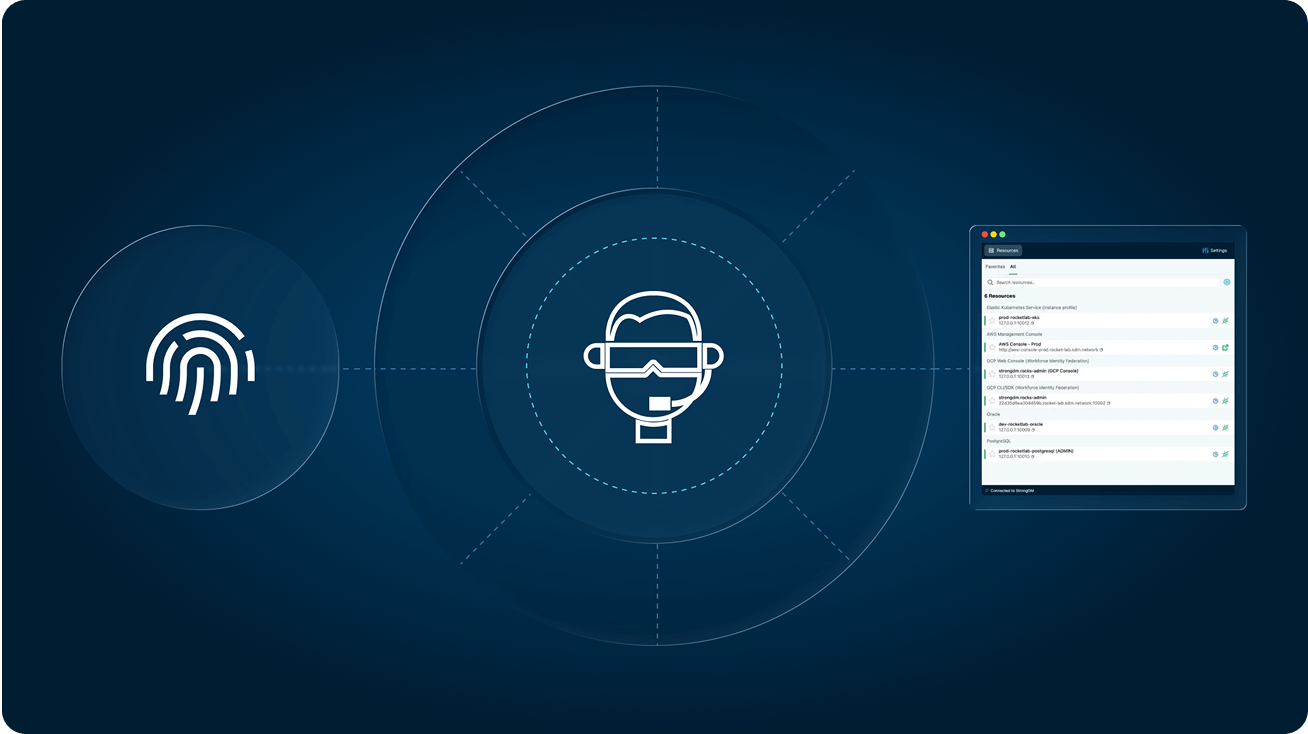
Eliminate unnecessary standing access to your resources on-premises and in the cloud. StrongDM makes Zero Standing Privileges a reality.
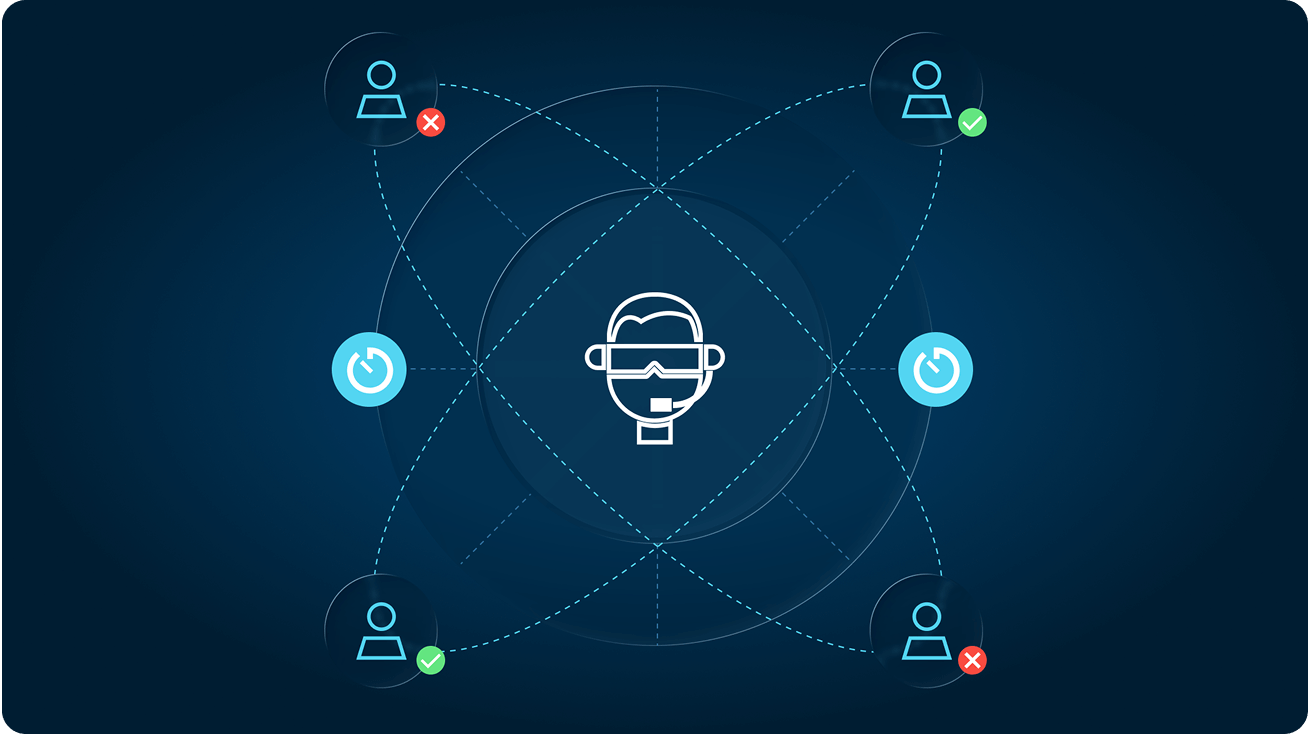
Enhance observability with a record of every activity and query, and improve mean-time-to-investigate (MTTI) and mean-time-to-respond (MTTR) to incidents.
Access reports identify unused privileges, surface your most sensitive access grants, and so much more.



