Access on Your Terms: Seamless, Secure, and Dynamic
StrongDM provides comprehensive privileged access management for servers, databases, Kubernetes, cloud platforms, and more—all powered by fine-grained, policy-based, dynamic authorization.



















Meet StrongDM: Your Partner in Zero Trust Privileged Access









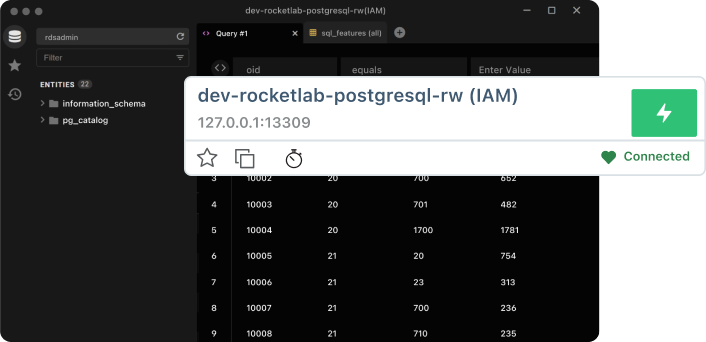

Granular Control, Maximum Security. Just Like You Want.
Set dynamic policies with precision. Reduce risks, eliminate standing access, and enforce Zero Trust—all while staying ahead of threats.
Learn more
Meet Compliance on Your Terms with Real-Time, Auditable Access.
Streamline audits, ensure policy consistency, and maintain continuous compliance with zero standing privileges and granular reporting.
Learn more
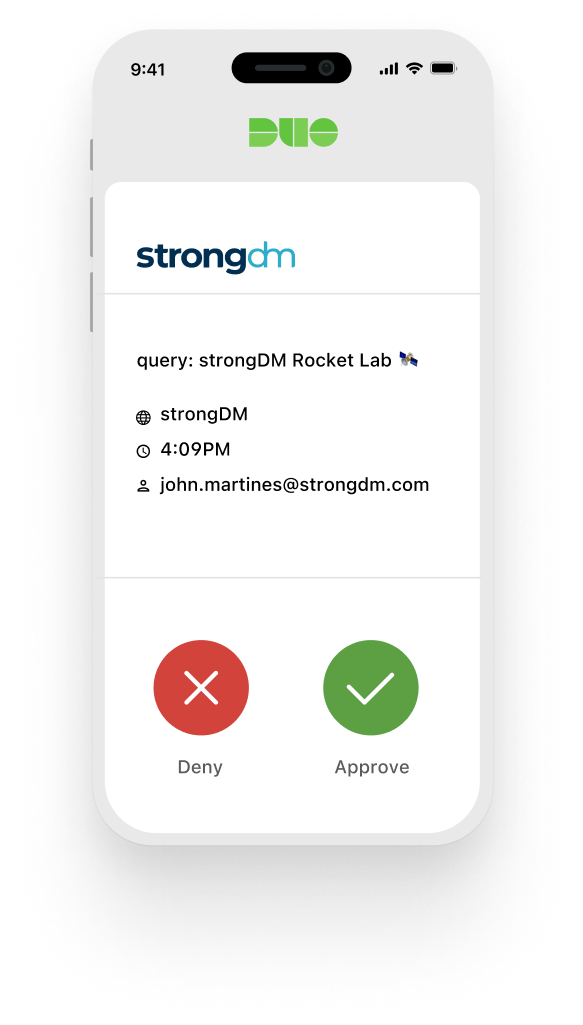
Access When You Need It Without the Wait (or Frustration).
Get instant, hassle-free, secure access to the resources you need, seamlessly integrated into your workflows—because security shouldn’t slow you down.
Learn moreYour Zero Trust Privileged Access Management Platform
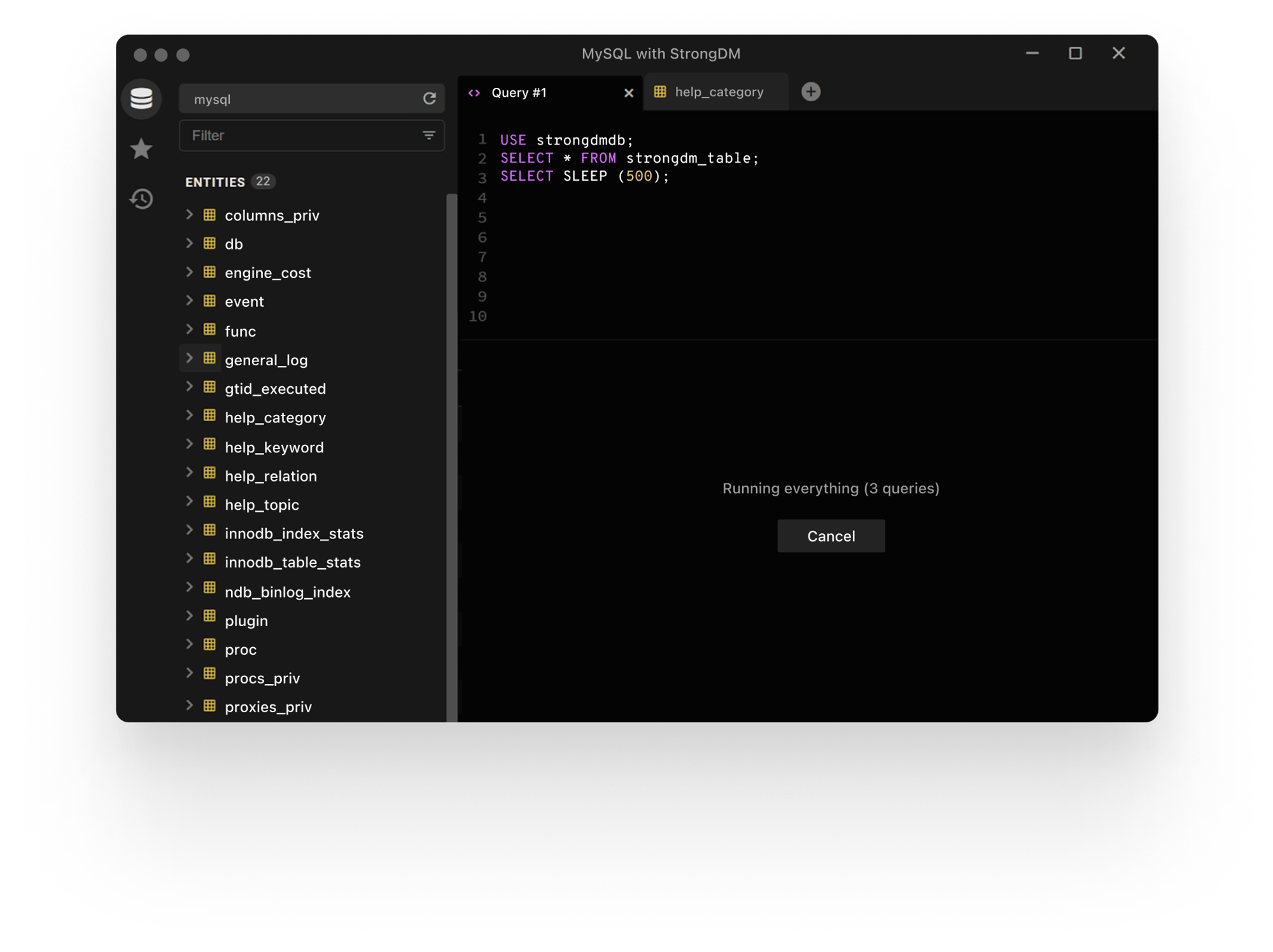
Strong Policy Engine
Our Cedar-based policy engine is at the heart of our Zero Trust approach, allowing you to create and enforce fine-grained access controls. Tailor who gets access, to what, and when — ensuring the right people have the right access at the right time.
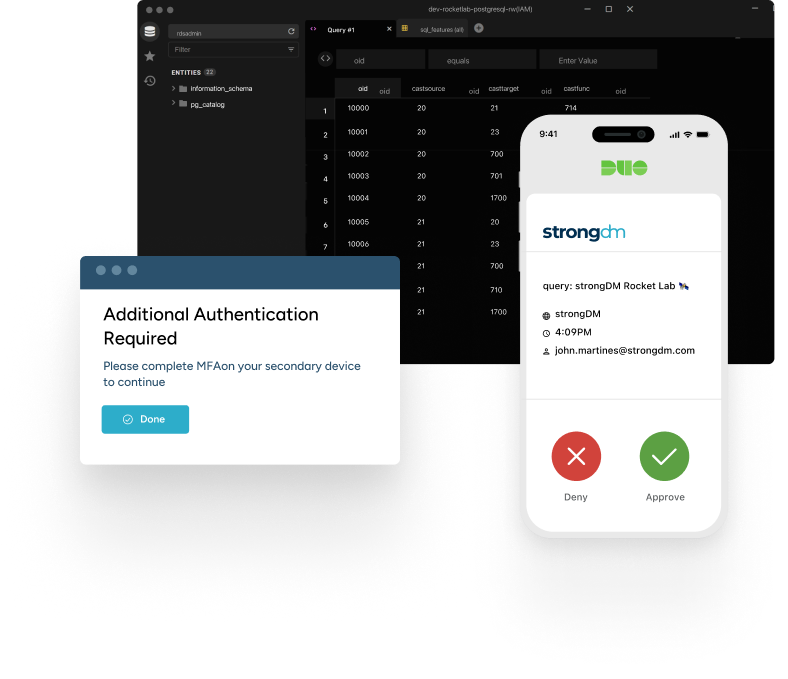
Frustration-free Access
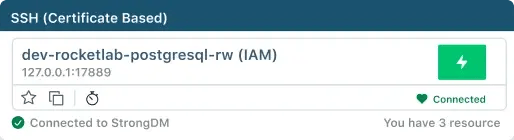
We believe security shouldn’t slow you down. That’s why StrongDM is designed for simplicity, enabling users to securely access the resources they need without frustration. It’s about making your day smoother, not more complicated.
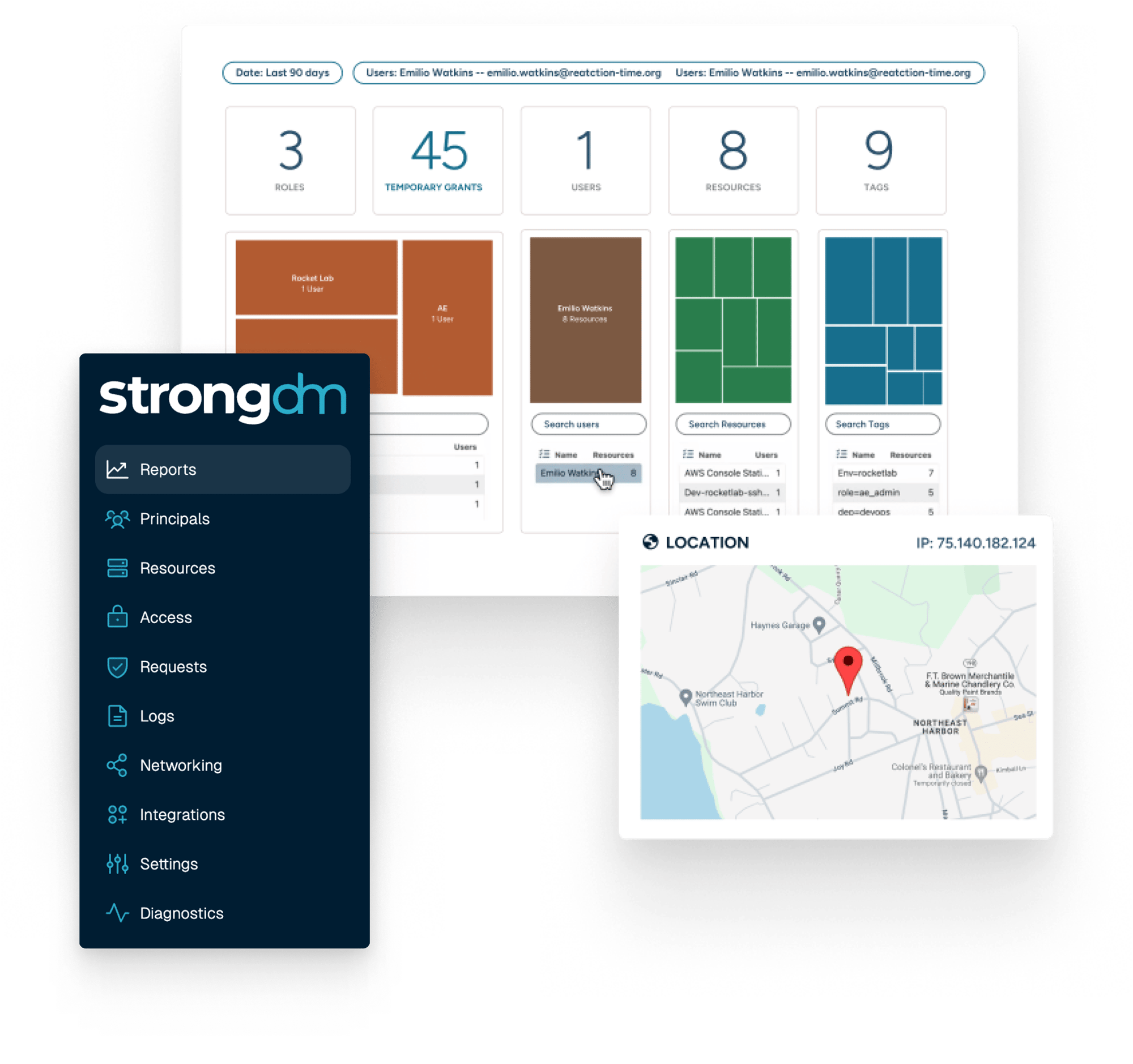
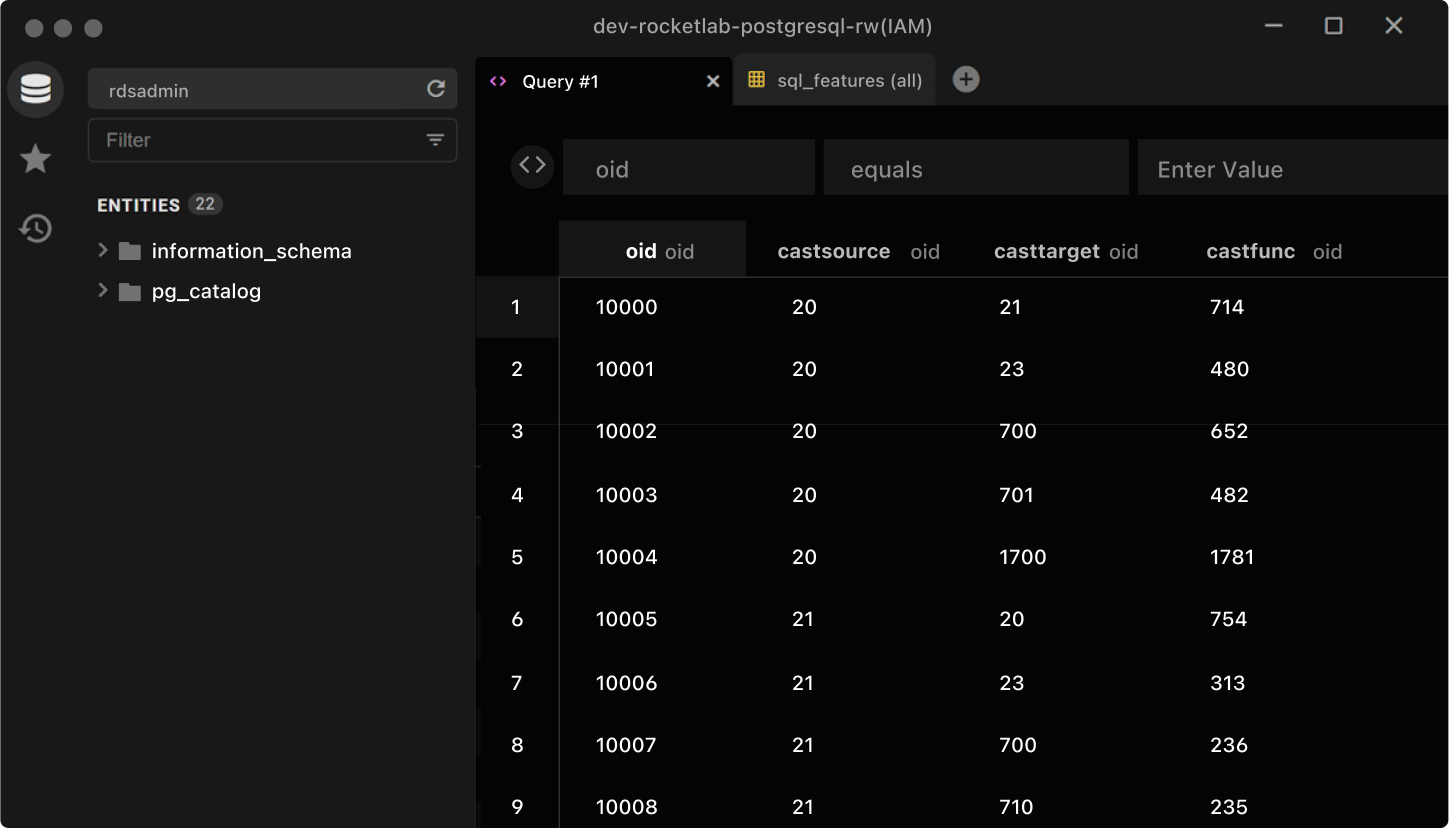
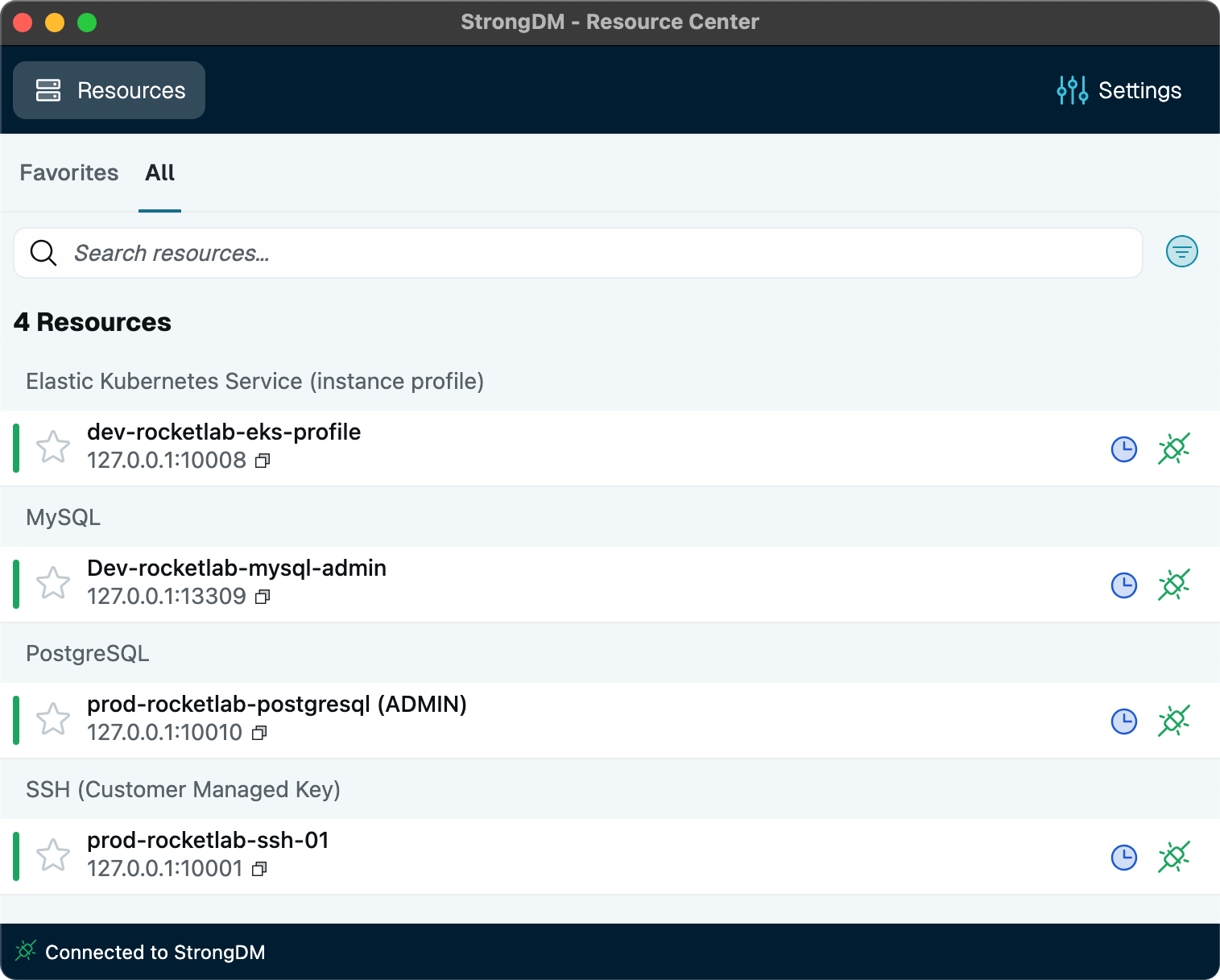
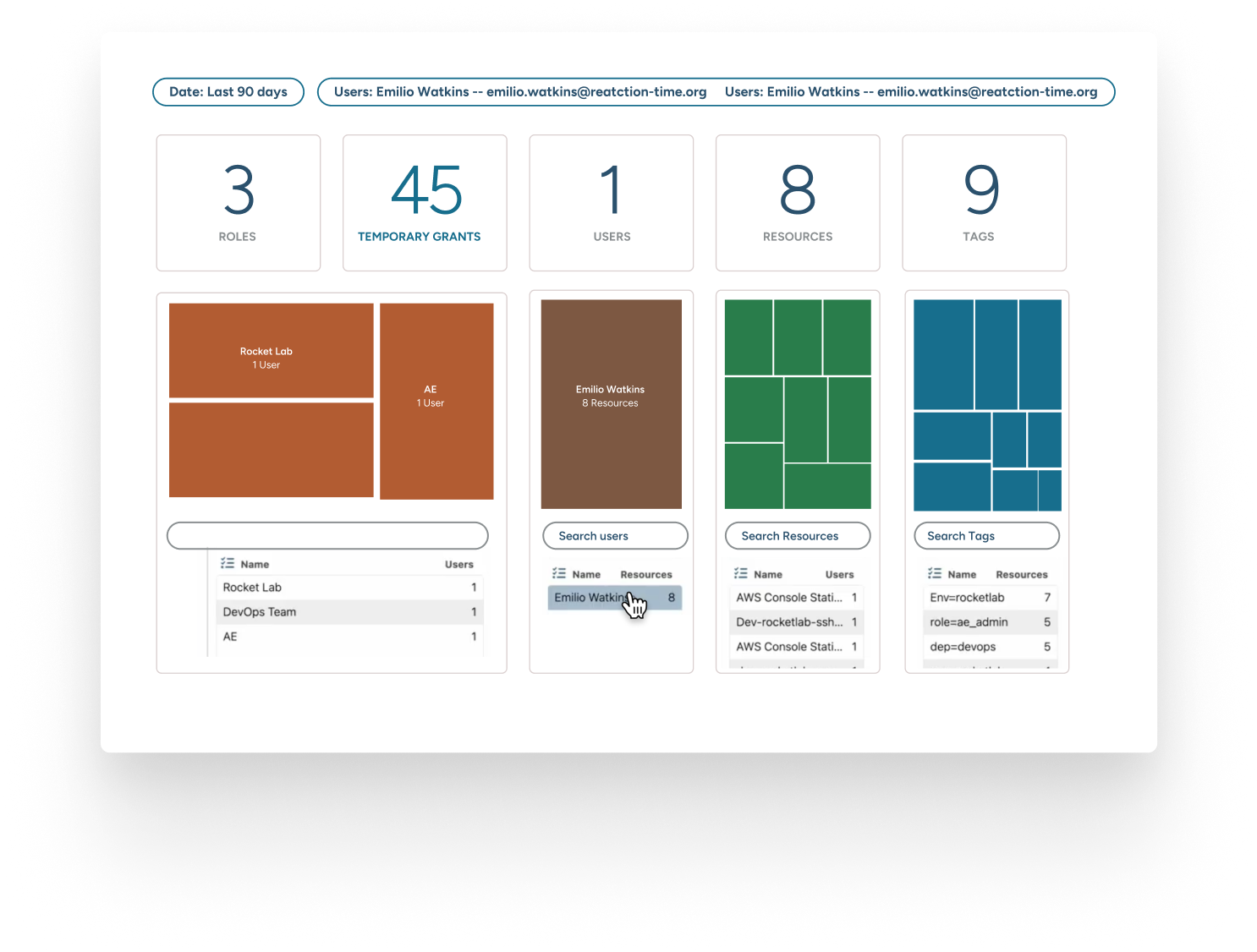
Complete Visibility
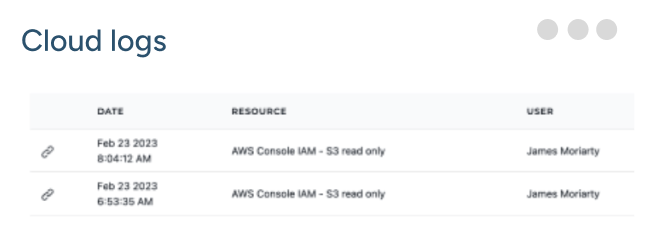
With StrongDM, you get a bird’s-eye view of your digital environment. Track who accessed what and when, ensuring transparency across your infrastructure. It’s the clarity you need to make informed security decisions.
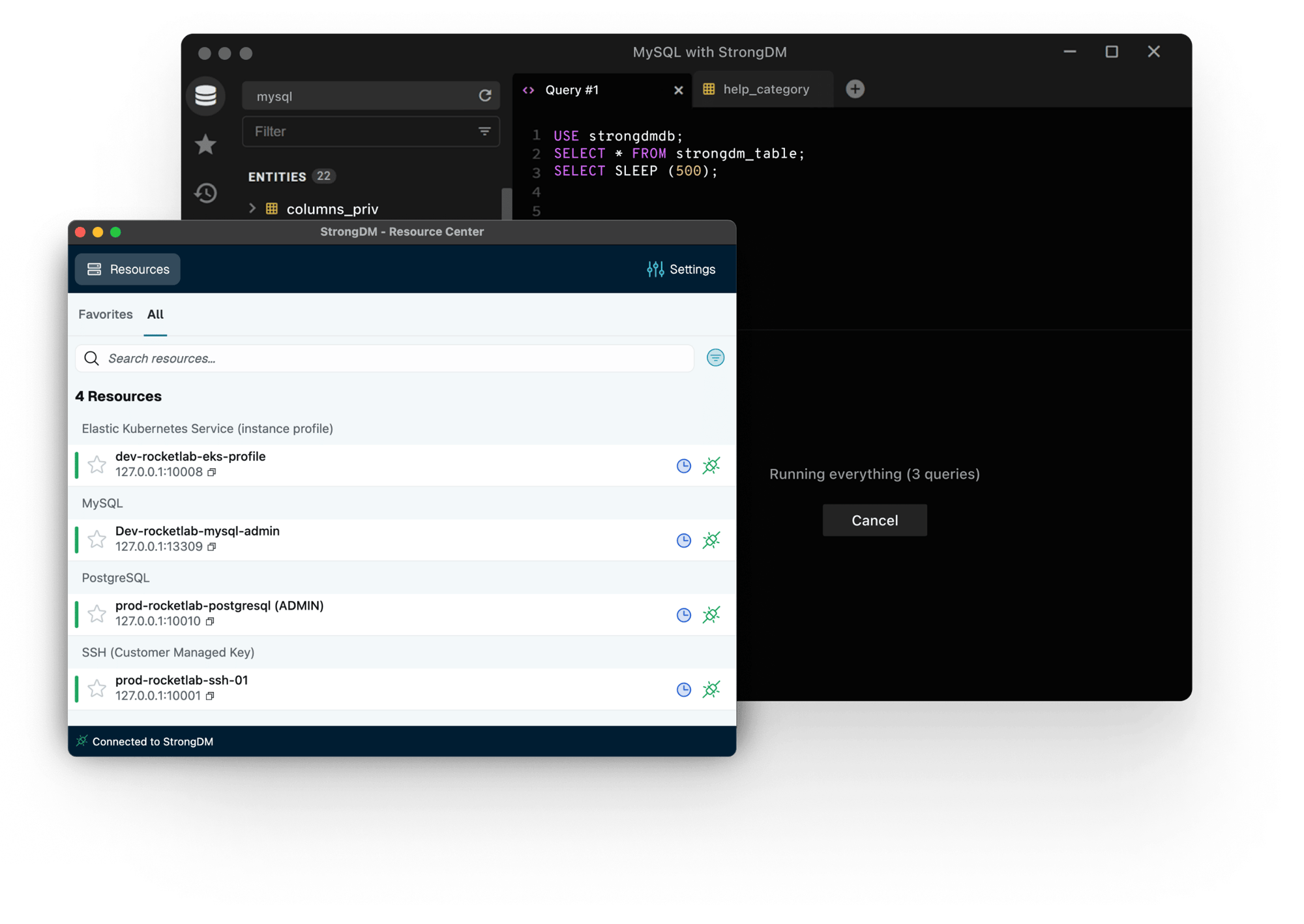
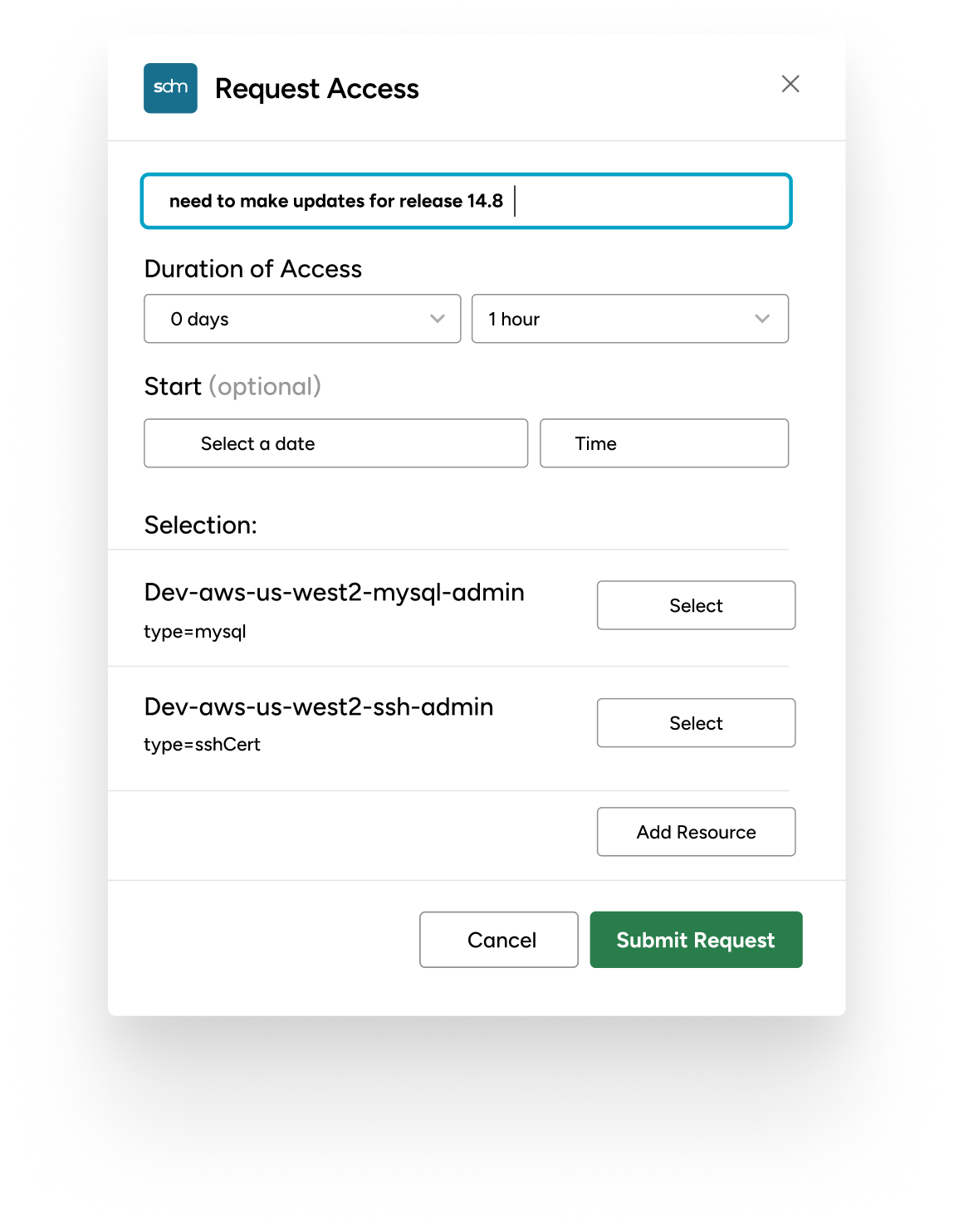
Workflows for Just-in-Time Access
Our workflows empower your team with just-in-time access, reducing the attack surface without hindering productivity. Access is granted when needed and pulled back when done, all automatically.
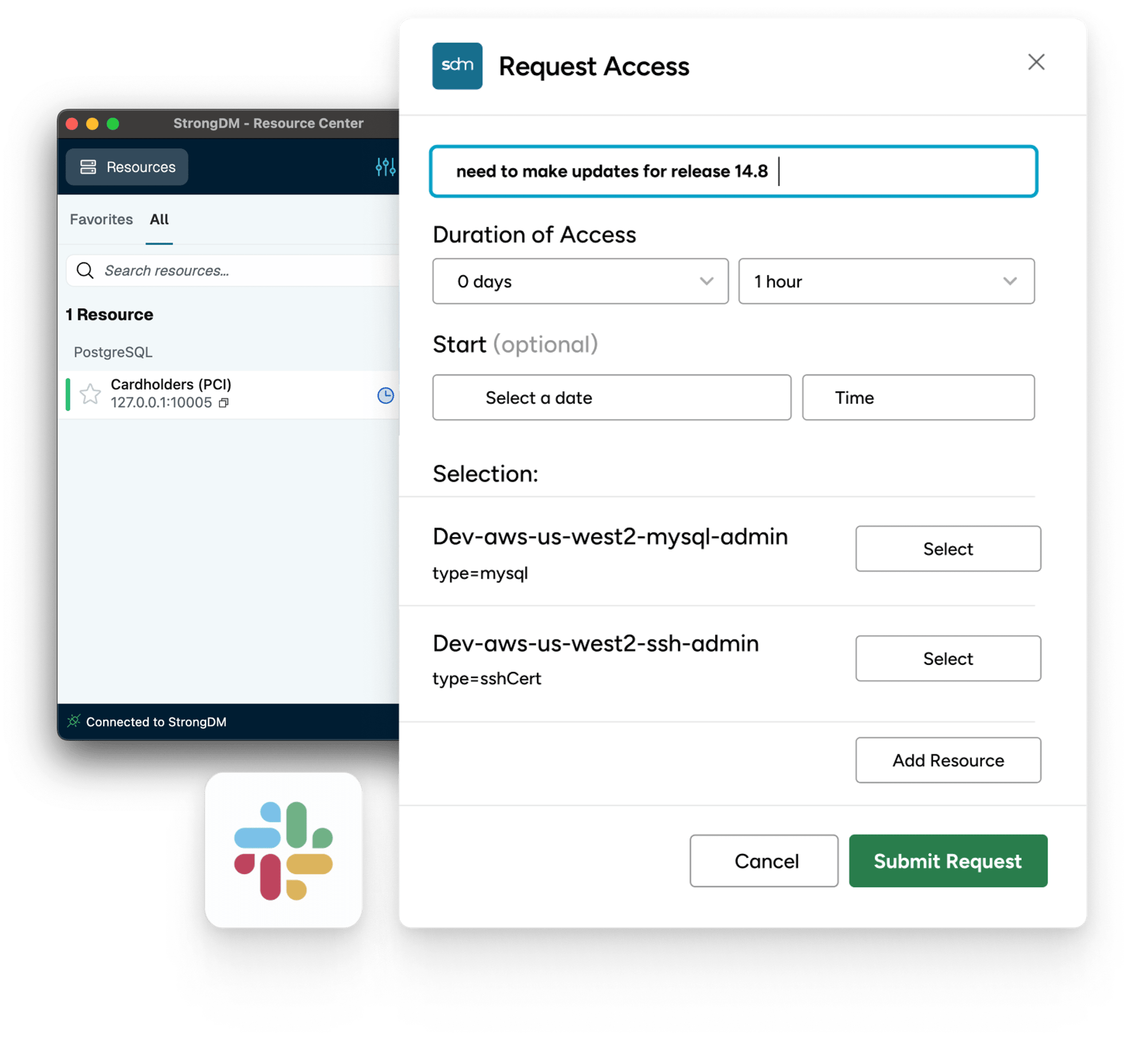
No Migration or Coding Needed
Want to keep using your existing vaults or secret stores? Go for it. StrongDM integrates with existing tools and the policies can be applied without requiring you to recode your apps or move your secrets.

.png?width=626&height=470&name=Frame%20660235427%20(3).png)

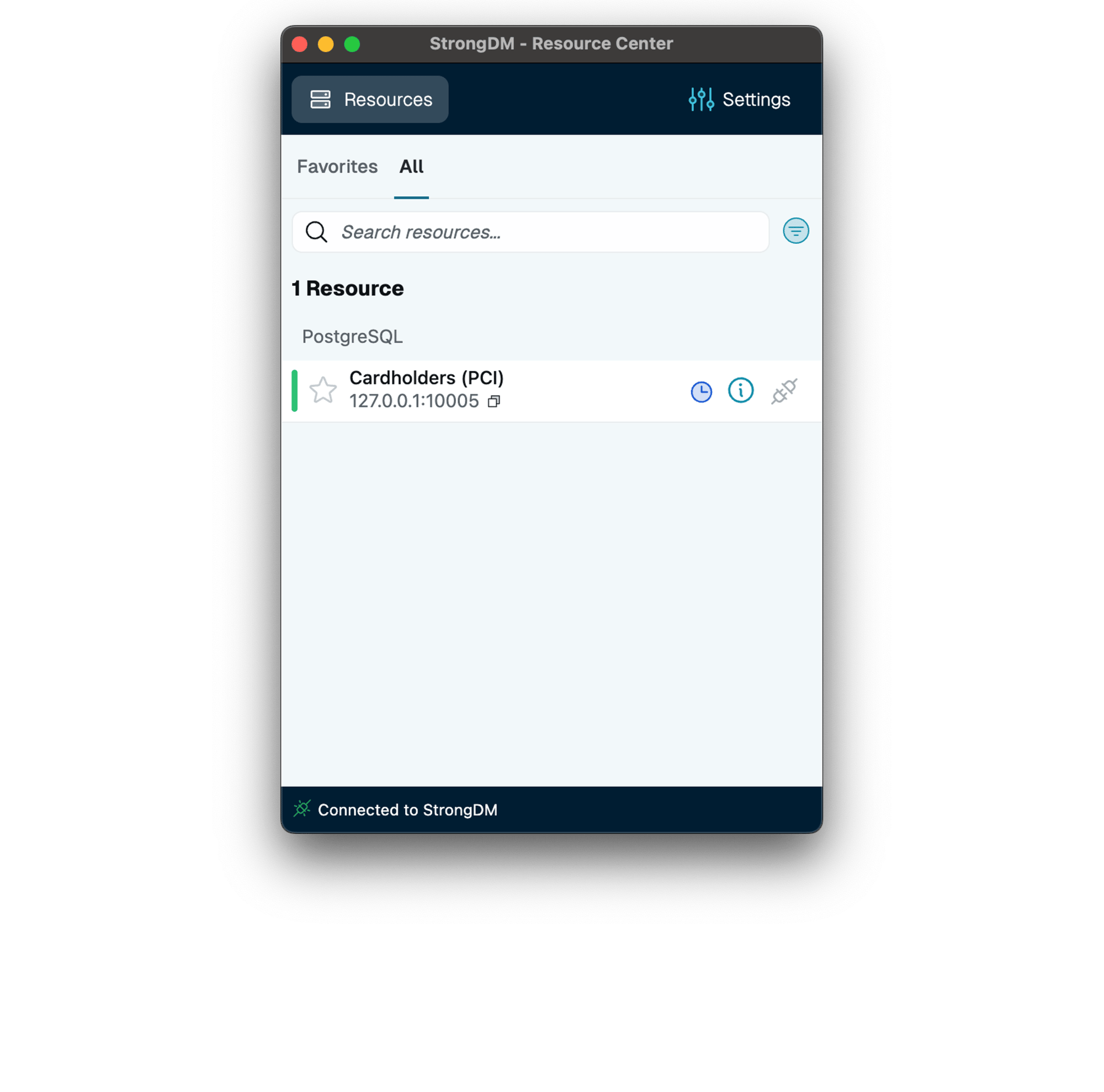







See the StrongDM Difference
Before StrongDM
After StrongDM
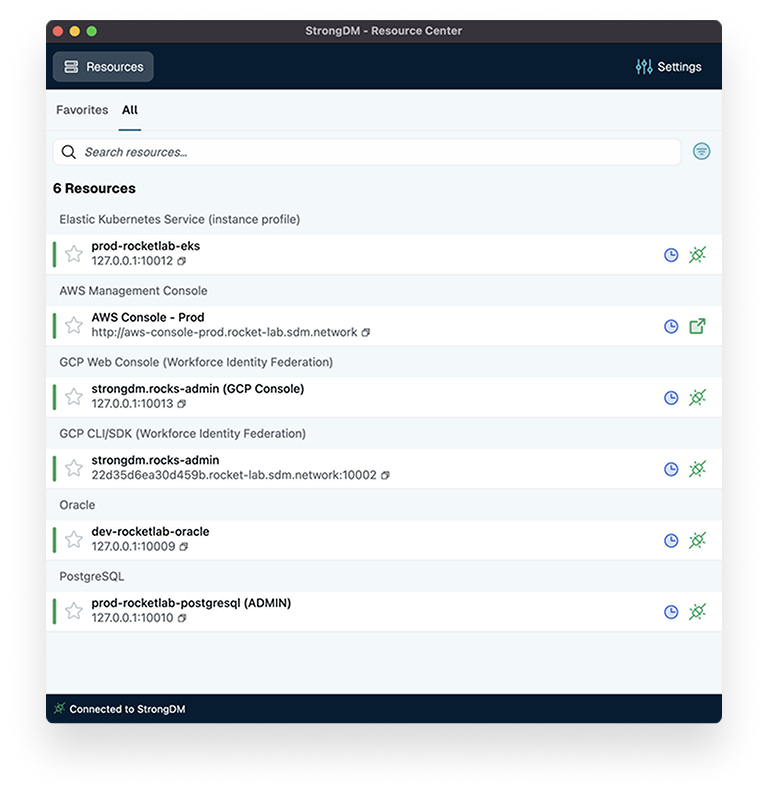
Backed by a world-class customer experience
“Security is a necessary part of day-to-day life. In terms of how we go forward, StrongDM will continue to be part of that story. It has all the mechanisms in place for database access control that we require, and I haven’t found a competitor yet that does the same thing.”
Wes Tanner
VP Engineering, ZEFR
“We chose StrongDM because the solution is the one solution to rule them all. You simply integrate all your data sources into StrongDM; you integrate all your servers into StrongDM; you integrate all your Kubernetes clusters into StrongDM. You give your developers one simple tool they need to connect using SSO, and they have access to what they own.”
Jean-Philippe Lachance
Team Lead - R&D Security Defence, Coveo
“Clearcover remains committed to the industry’s best security practices. StrongDM provides us with better insights to bolster our security posture.”
Nicholas Hobart
Senior Engineer, SRE Team, Clearcover
“I would urge all other CISOs to adopt StrongDM as their database proxy platform. It's been amazing for all of our users. When we first got StrongDM, we implemented within, I think a day. And within a week we saw more and more users requesting access to it, once they saw how easy it was to access databases.”
Ali Khan
CISO, Better
“With StrongDM, people don't have to maintain usernames and passwords for databases. With servers, they don't have to have keys. For websites, they don't have to have passwords. And so when you start eliminating the need for passwords and you start looking at things like Zero Trust, I believe that the attack surface is completely reduced.”
David Krutsko
Staff Infrastructure Engineer, StackAdapt



A Tailored Solution Just for Your Organization
Your technology stack is unique. Whether your infrastructure spans multiple clouds, utilizes diverse databases, or relies on critical applications, StrongDM seamlessly integrates with technologies you trust.
StrongDM is designed to fit your environment, not the other way around.




