Privileged Access in the Age of Cloud Authentication & Ephemeral Credentials


Written by
Fazila MalikLast updated on:
October 17, 2025Reading time:
Contents
Built for Security. Loved by Devs.
- Free Trial — No Credit Card Needed
- Full Access to All Features
- Trusted by the Fortune 100, early startups, and everyone in between
The way that people work continues to evolve, and as a result, so do the ways that they must authenticate into their organization’s resources and systems. Where once you simply had to be hardwired into the local office network, now you must expand your perimeter to include remote and hybrid workforces, on-prem and cloud environments, and take into account a growing list of factors that impact how and where people access critical company resources.
With so much shifting in the landscape, it’s no wonder that 1 in 3 cloud intrusions use compromised credentials, and that compromised credential use has skyrocketed over 300%.
Zero Trust and zero standing privileges (ZSP) aim to solve this problem–and a critical part of this is better management, or better yet, the elimination of, passwords and credentials altogether.
The Problem with Passwords and Credentials
Where to start…
- They are always on
- They can be stolen
- They can be brute forced
- They can be shared
- They can be phished
- They can be used in multiple places–so a breach can give access to many things
- You can get locked out of your account
- You can forget your credentials
- They need to be rotated
- They can be written on a sticky note
Need we go on?
One of the biggest contributors to the risk of passwords is the fact that they are “always on.” In other words, they exist in a continuous and perpetual state of being stolen or used for malicious purposes. Couple this with the practice of pairing with static roles and groups, and you’ve got a breach waiting to happen.
No More Secrets: The Era of Passwordless Authentication and Ephemeral Credentials
Addressing the password and credential problem can significantly reduce the risks that exist in the authentication of your internal applications and resources. Put simply, when passwords don’t exist, it’s not possible for them to become an attack vector. This is where passwordless authentication and ephemeral credentials deliver major advantages.
Let’s look at some definitions:
What are ephemeral credentials?
Ephemeral credentials are temporary authentication tokens, keys, or certificates that provide limited and time-bound access to resources or systems.
They enhance security by minimizing the time that access to resources or systems is available. And because they are temporary, they no longer provide access after the session or temporary grant expires.
What is passwordless authentication?
Passwordless authentication is just that–it removes the need for usernames and passwords to authenticate into resources and services.
Instead of relying on “what you know” (passwords), passwordless focuses on “who you are.” This is typically achieved through biometrics, hardware tokens, or one-time codes sent via secure means.
Taken together, passwordless authentication and ephemeral credentials start the process of eliminating the risk posed by passwords to your organization. Neither are necessarily easy to deploy, however, simply due to how passwords and credentials have traditionally been managed.
Why Legacy PAM Needs to Pay Attention
Traditional privileged access management (PAM) has long taken a secrets and secrets-based (i.e.: passwords) approach to managing access to resources and tools. The problem with this approach is that secrets and secret vaults are fundamentally at odds with Zero Standing Privileges (ZSPs). For secrets, the mere act of existing means that you have standing privileges that represent a perpetual risk to your organization and must be stored away and guarded under lock and key.
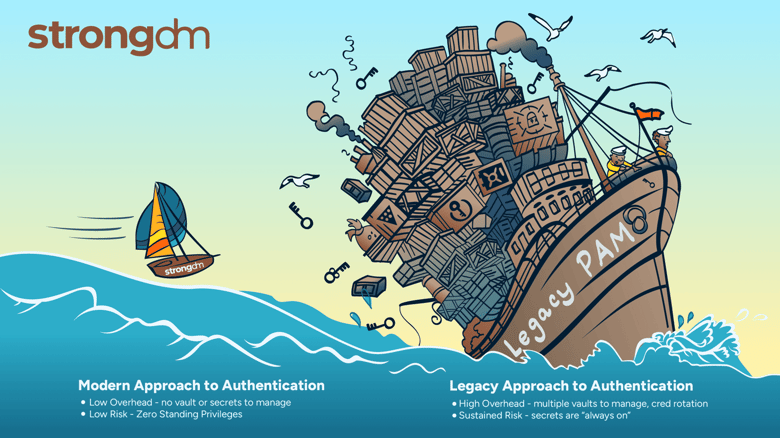
Managing secret vaults and secrets can also come with substantial overhead. In many cases, the secret vaults provided by legacy PAM vendors only cover a subset of your entire stack or only support on-premises resources and tools. In these situations, organizations can end up acquiring multiple vaults (one for on-premises, one for AWS, one for Azure, etc.), significantly increasing operational costs, complexity, and overhead associated with managing secrets and performing access auditing.
Modern methods for authentication, such as passwordless and ephemeral credentials operate across diverse platforms and for a wide range of use cases, and for IT teams, they make passwords and password management entirely obsolete.
Implementing Passwordless and Ephemeral Credentials with StrongDM
StrongDM delivers simple and secure access to critical infrastructure. It supports passwordless and ephemeral credential initiatives in these ways:
- Cloud-native authentication makes it easy for organizations to authenticate to cloud resources using their native methods, taking advantage of their ephemeral properties.. Today, StrongDM supports native cloud authentication using one of two methods:
- AWS IAM Roles for RDS Postgres and Aurora Postgres.
- Instance Profile Cluster for Amazon Elastic Kubernetes Service
- Remote Identities make it possible for users to access infrastructure and resources using their unique user profiles instead of one that is shared across multiple users. StrongDM allows users to apply their unique identifier for RDP, SSH, and Kubernetes, across AWS, Azure, GCP and on-prem
- Time is used as an additional dimension across the platform, with credentials, certificates, and tokens expiring automatically, delivering ephemerality.
With StrongDM, authentication across environments (on-premises, cloud, and hybrid) and across your stack (including legacy systems) is secure and ephemeral – which also makes it simpler and requires less overhead costs. This enables IT and security teams to deliver access in a seamless, secure, and auditable manner, while also being able to centrally manage it.
To learn more about how StrongDM can help you solve your access challenges, sign up for a demo here.
Next Steps
StrongDM unifies access management across databases, servers, clusters, and more—for IT, security, and DevOps teams.
- Learn how StrongDM works
- Book a personalized demo
- Start your free StrongDM trial

Categories:

About the Author
Fazila Malik, Sales Enablement Expert, as an accomplished Product Marketing Manager in the technology industry with over 5 years of experience, Fazila transitioned to a Sales Enablement leader position passionate about empowering go-to-market teams to excel in their roles. Throughout her career, she has worked with a range of technology products, including software applications and cloud-based solutions. Fazila is a member of the Product Marketing Alliance and an AWS Cloud Certified Practitioner. To contact Fazila, visit her on LinkedIn.
You May Also Like




