
- Role-based, attribute-based, & just-in-time access to infrastructure
- Connect any person or service to any infrastructure, anywhere
- Logging like you've never seen

Summary: In this article, we’ll review the leading privileged access management (PAM) solutions and tools on the market. We’ll explore the pros and cons of the top privileged access management vendors so you can easily compare the best PAM solutions. By the end of this article, you’ll feel confident choosing the right privileged access management solution for your organization.
1. StrongDM

StrongDM’s Zero Trust Privileged Access Management (PAM) platform goes beyond the capabilities of a traditional PAM solution to support Zero-Trust access by unifying management of access policies and increasing accuracy and efficiency when gathering evidence for compliance reporting. Unlike other PAM vendors, StrongDM makes it easy to manage permissions and grant or revoke access—including just-in-time, single-use access—at a moment’s notice to any resource from a single, secure platform.
👀 Want to learn how StrongDM's PAM works and see it in action with an interactive tour? Visit here for more!
The cloud-first IAP solution uses a control plane to simplify monitoring and management access to databases, servers, Kubernetes clusters, and web apps. With full access control over your entire IT infrastructure, you can capture precise details of all use across every user session. This single source of truth for your access data makes it easy to maintain regulatory compliance standards, pull comprehensive reports, and search or query logs for all activity.
🕵 Investigate: Check out StrongDM’s customer reviews.
StrongDM's PAM Use Cases
- Modern Cloud PAM solution - built to support a variety of cloud networks, including public, private, multi-cloud, and hybrid.
- Comprehensive observability and visibility - log every permission change, database query, ssh & kubectl command.
- Zero Standing Permissions - grant Just-in-Time access to your critical infrastructure. Access only exists when it is needed. Protect data with customer information or production environments.
💡Make it easy: Just-in-Time Access works best when it is easy for the end user to request and receive access. It should also be auditing to map the end to end chain of events, who is requesting access, why they are requesting it, and for how long. Play the video below and see how easy StrongDM makes Just-in-Time access and try it for yourself.
- Faster onboarding - no need to provision database credentials, ssh keys, VPN passwords for each new hire.
- Secure off-boarding - suspend SSO access once to revoke all database, server access.
- Automatically adopt security best practices - least privilege, just-in-time access, audit trail.
🕵 Investigate: See how StrongDM is an essential tool for the Divvy technical team, particularly when it comes to onboarding/offboarding, JIT access for Kubernetes and datasources, and auditing user access. Read the full customer story.
- Vendor privileged access management - connect third-party vendors to resources with project-based access that automatically expires.
- Security and compliance teams - simplify HIPAA, SOC 2, SOX, ISO 27001 compliance certification.
StrongDM Pros
- Supports zero trust principles with an all-inclusive and cloud-native infrastructure access platform
- Detailed logs tracking every session to support auditing and compliance reporting for ISO 27001, HIPAA, PCI, SOC 2, SOX, and more
- Full visibility for comprehensive monitoring and logging
- Cloud-native and simple architecture makes it easy to deploy and scale across your entire infrastructure, on-premises, cloud, or hybrid environments
- Extensive automation capabilities for seamless permissions management
- Natively integrates with a wide range of tools, cloud providers, containers, databases, and servers
StrongDM Cons
- SaaS-only offering
- Requires continual access to StrongDM API for access to managed resources
Learn more about StrongDM's competitors and alternatives.
StrongDM's G2 Reviews
- 57 reviews (at the time of writing)
- 4.7 / 5 stars
Read all of StrongDM’s G2 reviews here.
Pricing Information
StrongDM offers simple per-user pricing, starting at $70/license including support for all resource types.
Users have the option to sign up for a free trial.

⚠️ Traditional PAM deployments have gaps. Learn how to protect your databases, the cloud, Kubernetes, and more with our legacy PAM augmentation guide.
2. CyberArk
CyberArk’s Privileged Access Manager offers identity and privileged access management capabilities deployed through either a SaaS or self-hosted on-premises model. This PAM tool helps organizations discover and manage privileged credentials for both human and machine identities across thousands of endpoints. CyberArk also provides adaptive, context-aware MFA and SSO to validate users.
CyberArk supports a Zero-Trust security model by providing just-in-time access for users as needed. Plus, this PAM solution provides automation capabilities that may fit well into different teams’ existing workflows.
🕵 Check out CyberArk’s G2 reviews.
Despite enhancing secure access for remote employees and vendors, CyberArk doesn’t provide the comprehensive threat detection in SaaS deployments that most organizations need. That makes it difficult to detect an access breach quickly. Top-tier PAM security capabilities are available through different compatible CyberArk products, but integrating multiple separate tools often makes CyberArk implementations difficult and costly.
CyberArk Pros
- CyberArk Marketplace offers over 350 out-of-the-box software integrations
- Cloud-based SaaS and self-hosted on-premises deployment models
- Recorded user sessions for compliance reporting and auditing
- Built-in adaptive MFA and SSO capabilities
CyberArk Cons
- Complex and difficult to set up
- Expensive compared to similar PAM solutions (see How Much Does CyberArk Cost and Is It Worth It?)
- Threat detection and response features are only available for self-hosted deployments
- Slow application loading times
- Not designed to support cloud-native environments or modern infrastructure tooling
- Locked into CyberArk proprietary tools like CyberArk PAM Vault or CyberArk Conjur for credential management
Learn more about CyberArk's competitors and alternatives.
3. Okta ASA
Okta’s Advanced Server Access (ASA) offers cloud-native privileged access management for multiple servers across your multi-cloud infrastructure. With Okta’s API, organizations can customize authentication and management workflows to support their DevOps teams’ needs. ASA makes it easy to automate onboarding and offboarding for project teams, too, so organizations can improve productivity through a streamlined user experience.
That said, Okta ASA doesn’t technically authenticate individual user credentials; it assigns users to teams and applies role-based access controls (RBAC) to allow particular teams access to SSH and RDP servers. While team provisioning can save time by removing individual credentials, it doesn’t offer the granular control many companies look for in an enterprise PAM solution.
It’s also important to note that ASA only supports access to servers—not web applications, databases, Kubernetes clusters, or anything else. They don’t currently offer an overarching PAM software solution, meaning teams will have to piece together different tools within the Okta product suite to gain meaningful privileged access management capabilities.
Okta ASA Pros
- Secures access to all SSH and RDP servers
- Integrates well with traditional PAM solutions and other Okta security tools
- Automated onboarding and offboarding with team provisioning
- Simplifies compliance with detailed audit logs
- Works in any hybrid or multi-cloud environment
Okta ASA Cons
- Only applicable for servers
- No individual credential management option
- Expensive since cost is assessed per server
- No auditing capabilities for RDP and difficulty exporting some audit logs
- Complex set-up process
Learn more about Okta's competitors and alternatives.
4. HashiCorp Vault
HashiCorp’s Vault solution is a secrets manager that securely stores and controls access to encryption keys, passwords, tokens, and certificates. With Vault, HashiCorp allows organizations to generate over 10,000 unique tokens in a day and automate application delivery. This privileged access management software offers three pricing models: a free, self-managed option, a managed cloud option, and an enterprise-level self-hosted option.
Vault specializes in providing and deleting dynamic, ephemeral credentials to access infrastructure and protect against leaked passwords. Unique credentials created for each session have a lease, and once the lease expires, the credentials are destroyed. This system provides an opportunity for businesses to automate and streamline access management.
🕵 Check out HashiCorp Vault’s G2 reviews.
However, to support most common PAM use cases, customers will also want to use HashiCorp’s Boundary product for identity-based access management and session management. Vault and Boundary allow a company to automate credential brokering and provide just-in-time access across cloud environments, databases, and SSH servers. Boundary also offers session recording, logging, and monitoring to reduce the risk of a security breach.
HashiCorp Vault Pros
- Protect all data through a CLI session, API, or user interface so organizations can secure different types of secrets
- Offers just-in-time ephemeral credentials
- Platform-agnostic solution deployable in public cloud environments
HashiCorp Vault Cons
- Needs to be used with Boundary to meaningfully support PAM use cases
- Doesn’t sufficiently support end-user credential management
- Limited features for each pricing model
- Needs custom integration to fit into current workflows
- No out-of-the-box compliance reporting support
Learn more about HashiCorp Vault's competitors and alternatives.
5. Delinea (formerly Thycotic & Centrify)
Delinea—the product of a merger between Thycotic and Centrify—provides a comprehensive privileged access management solution that’s easy to install, configure, and manage. The organization offers a series of top PAM solutions companies can combine to customize access management capabilities from four functional areas: protecting data, securing endpoints and devices, controlling cloud access, and securing code.
Delinea’s Secret Server solution is an encrypted credential storage vault that can store up to 10,000 secrets on the cloud or an unlimited number of secrets on premises. Secret Server integrates with Active Directory and LDAP and uses a least-privilege policy to maintain identities with RBAC. It also supports robust reporting capabilities and some automation features like automatic password changing and checking if passwords remain active.
🕵 Check out Delinea’s G2 reviews.
While this privileged access management solution performs well in Windows environments, it doesn’t support modern cloud-native databases or Kubernetes deployments, and many common third-party integrations are notably absent.
Delinea Pros
- Available in both the on-premise and cloud versions
- Easy to install, configure, and manage
- Secures access to all SSH and RDP servers
- Pick and choose the tools you need and view multiple tools from a single dashboard
- Cloud-based SaaS and self-hosted on-premises deployment models
Delinea Cons
- Consolidated bundles lead to confusing pricing
- Does not secure access for cloud-native databases or modern infrastructure tooling
- Designed to best support Windows-based environments and legacy databases
- No native agentless recording functionality for RDP session management
Learn more about Delinea's competitors and alternatives.
6. BeyondTrust
Like Delinea, BeyondTrust offers a suite of privileged access management tools that give companies the ability to build their own comprehensive PAM solution. Together, these tools help organizations manage identities and control access across Linux, Mac, Windows, and Unix, along with cloud and network environments. This makes BeyondTrust an interesting solution for companies that need to manage a wide array of endpoints.
This PAM solution offers a generalized password management vault and a dedicated DevOps secrets safe, which can reduce common compliance or security concerns unique to DevOps teams. Plus, the Endpoint Privilege Management tool helps maintain a least-privilege policy across nearly any environment and features comprehensive analytics to monitor user behavior against existing security intelligence to detect breaches.
🕵 Check out BeyondTrust’s G2 reviews.
However, since each feature is part of different dedicated software, licensing costs quickly get expensive. Plus, BeyondTrust doesn’t integrate well with single sign-on capabilities, which are often a foundational element of a PAM security strategy.
BeyondTrust Pros
- Implement and enforce a least-privilege policy on Windows, macOS, Unix, and Linux
- Simple to deploy and manage
- Strong logging, reporting, audit, and analytics capabilities for compliance and incident response
- Enables permissions management with AD, LDAPS, RADIUS, and Kerberos
BeyondTrust Cons
- Products are purchased separately, which drives up licensing costs
- Users report a clunky interface
- Poorly rated secrets manager without native authentication capabilities
- Doesn’t integrate well with SSO
Learn more about BeyondTrust's competitors and alternatives.
7. ManageEngine PAM360
ManageEngine’s PAM360 is just one of many security products by its parent company Zoho Corp, and this PAM solution excels at discovering accounts across a company’s IT infrastructure. The all-in-one, easy-to-implement platform offers extensive user control and monitoring capabilities for network resources, especially for protecting assets during development.
Alongside familiar offerings like a privileged credentials vault and just-in-time access provisioning, PAM360 also provides strong security capabilities by leveraging AI and ML-driven anomaly detection. Combining this data with context-aware endpoint event logs can help teams better understand their users and detect a security threat faster. Plus, extensive logging, session monitoring, and reporting capabilities streamline compliance audits and help companies meet security standards.
Unlike many of the top privileged access management vendors, ManageEngine only offers PAM360 as on-premises software. ManageEngine PAM3602 does not support cloud-native environments, data container systems like Kubernetes, or Linux. Plus, this vendor offers substantially fewer features than many other similar PAM solutions, causing some users to posit that the price point doesn’t match the software’s value.
ManageEngine PAM360 Pros
- AI-based security features for breach detection, prevention, and remediation
- Strong discoverability feature finds accounts across IT infrastructure
- Easy to deploy and maintain
ManageEngine PAM360 Cons
- Only available in an on-premises deployment model
- No options to add organizational policies to strengthen password management requirements
- Not appropriate for cloud-native environments or data containers
- Session management only available with a resource-heavy HTML5 browser session emulation
Learn more about ManageEngine PAM360's competitors and alternatives.
8. Teleport
Teleport’s Access Plane works similarly to StrongDM’s Zero Trust PAM platform—by providing full access to a company’s infrastructure through a single platform. By allowing engineers to access all applications, servers, databases, and Kubernetes clusters through one integrated PAM tool, Teleport and StrongDM help organizations maintain better control and visibility into user access.
The Access Plane is a unified gateway that allows users access through synchronized role-based access controls and single sign-on through Passwordless Access—which replaces all secrets, private keys, and passwords with biometrics. Users can also gain just-in-time access by creating a list of resources needed to do their work and sending the request to elevate privileges instantly via ChatOps for approval.
Teleport's free service only supports SSH servers and Kubernetes cluster access management. Many other desirable features like moderated sessions, proxy peering, and SOC 2 or FedRAMP compliance support are only available in an enterprise plan with Teleport.
Teleport Pros
- Access to servers, databases, applications, desktops, and Kubernetes clusters
- Offers built-in SSO and MFA capabilities or allows enterprises to integrate their existing SSO solution
- Passwordless access using biometrics
- Audit logs and recorded sessions across all infrastructure to support compliance reporting
Teleport Cons
- Many features only available for enterprise customers
- Users report difficulty implementing and customizing the platform, even with customer support
- Potential single point of failure
Learn more about Teleport's competitors and alternatives.
How to Choose The Right PAM Solution
As more organizations adopt cloud services, their security needs are evolving. Now, many need to upgrade to modern cloud-native privileged access management solutions to support their privileged user accounts across their changing infrastructure. This is especially crucial for organizations seeking security certifications like ISO 27001, SOC 2, and HIPAA.
Choosing the best PAM solution starts with taking a detailed look at:
- current IT infrastructure and ease of implementation needs
- current policies around access management, including provisioning and deprovisioning access
- typical user workflows
- the kinds of credentials or secrets you need to manage
- compliance or security requirements
- overarching IAM strategy
- how much access is costing your organization
By starting with these priorities, you can begin examining the privileged access management features your organization should prioritize and search for in the right PAM solution. For example, you may already have an SSO tool that works for your organization. In this instance, it’s important to consider whether that tool integrates with your PAM solution and will allow your users to access all the resources they need.
Consider the Goals for Your PAM Solution
The best PAM software often has three goals: protect systems and resources against unauthorized access, support user workflows, and meet and maintain security compliance standards.
Keeping credentials and secrets out of the wrong hands is vital to prevent breaches, and creating a Zero Trust environment is one of the best ways to do that. That involves introducing a strong vault that integrates with user directories, SSO and MFA tools, and all your servers, databases, and tools with a single gateway.
However, asking for constant user verification to keep credentials safe can quickly interrupt a user’s work. That’s why PAM tools can’t just limit access; they must also help allow access to temporary users, ensure users don’t maintain permissions past when access is needed and make it easy to move across applications without interrupting user workflows. That’s where features like just-in-time access and automatic provisioning or deprovisioning can help.
Then, once organizations have secured their sensitive data, they need a way to both achieve compliance with regulatory and security standards and to prove their ongoing compliance. Robust reporting capabilities, detailed logs, and session recordings make auditing easier, so you can spend less time pursuing compliance and more time on the work at hand.
Get a PAM Platform You Can Count on With StrongDM
Losing control of user access management can pose a major risk to your organization. Compromised credentials are one of the leading causes of data breaches, so what are you doing to protect your secrets? Now’s the time to get started with one of the top privileged access management solutions on the market: StrongDM.
StrongDM’s Zero Trust PAMplatform is a great PAM solution to ensure all the right users get access to the right resources at the right time. Our all-in-one identity and access management solution gives you the power to manage privileged access all across your cloud-first IT infrastructure—including servers, databases, internal web applications, Kubernetes clusters, and more. And our customer support? It’s legendary.
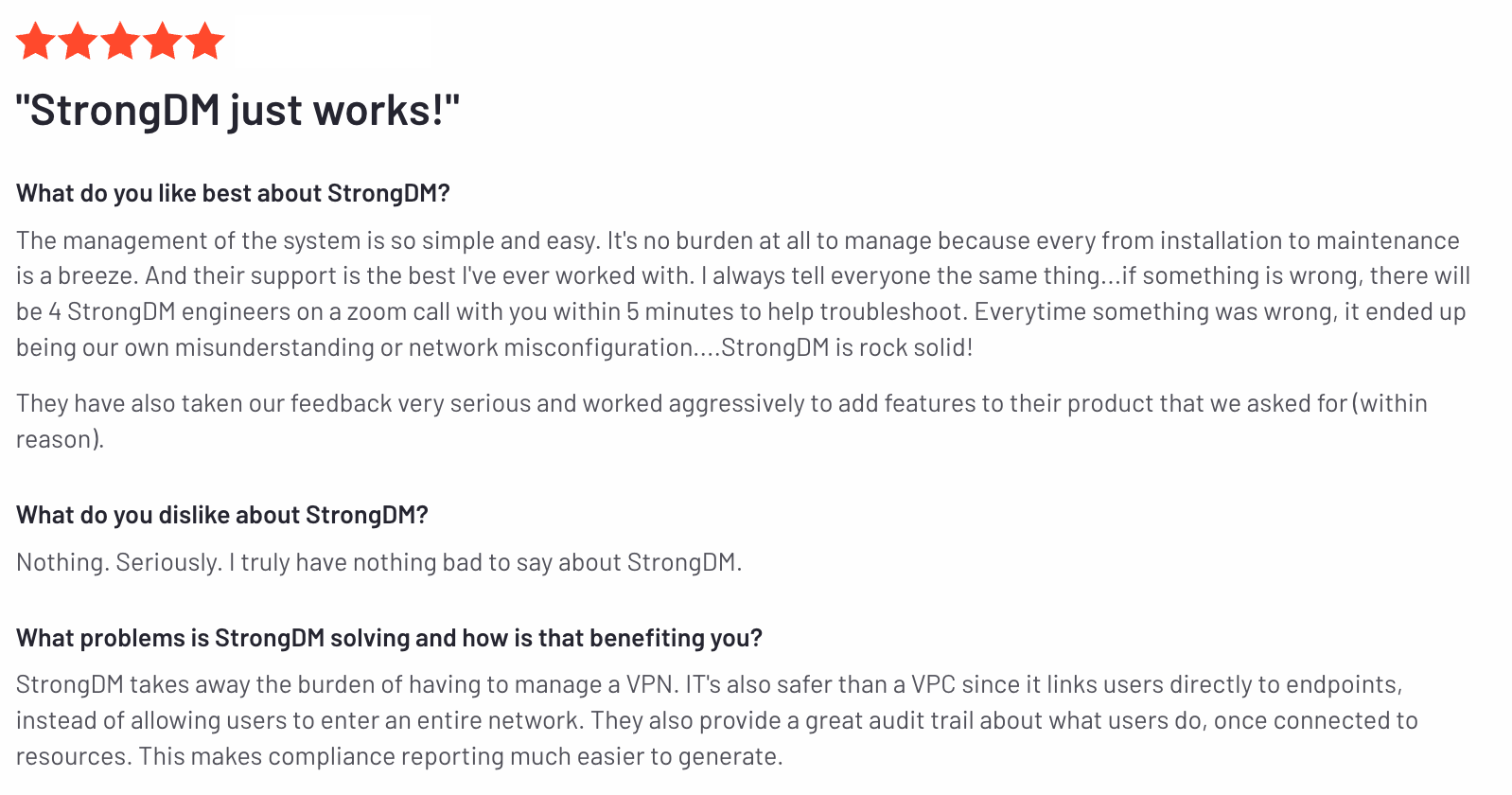
✨ The management of the system is so simple and easy. It's no burden at all to manage because every from installation to maintenance is a breeze. And their support is the best I've ever worked with.
- Gerry L. on G2 (read the full review)
Ready to give StrongDM a try? Sign up for a free 14-day trial of StrongDM today.
About the Author
John Martinez, Technical Evangelist, has had a long 30+ year career in systems engineering and architecture, but has spent the last 13+ years working on the Cloud, and specifically, Cloud Security. He's currently the Technical Evangelist at StrongDM, taking the message of Zero Trust Privileged Access Management (PAM) to the world. As a practitioner, he architected and created cloud automation, DevOps, and security and compliance solutions at Netflix and Adobe. He worked closely with customers at Evident.io, where he was telling the world about how cloud security should be done at conferences, meetups and customer sessions. Before coming to StrongDM, he lead an innovations and solutions team at Palo Alto Networks, working across many of the company's security products.

You May Also Like






