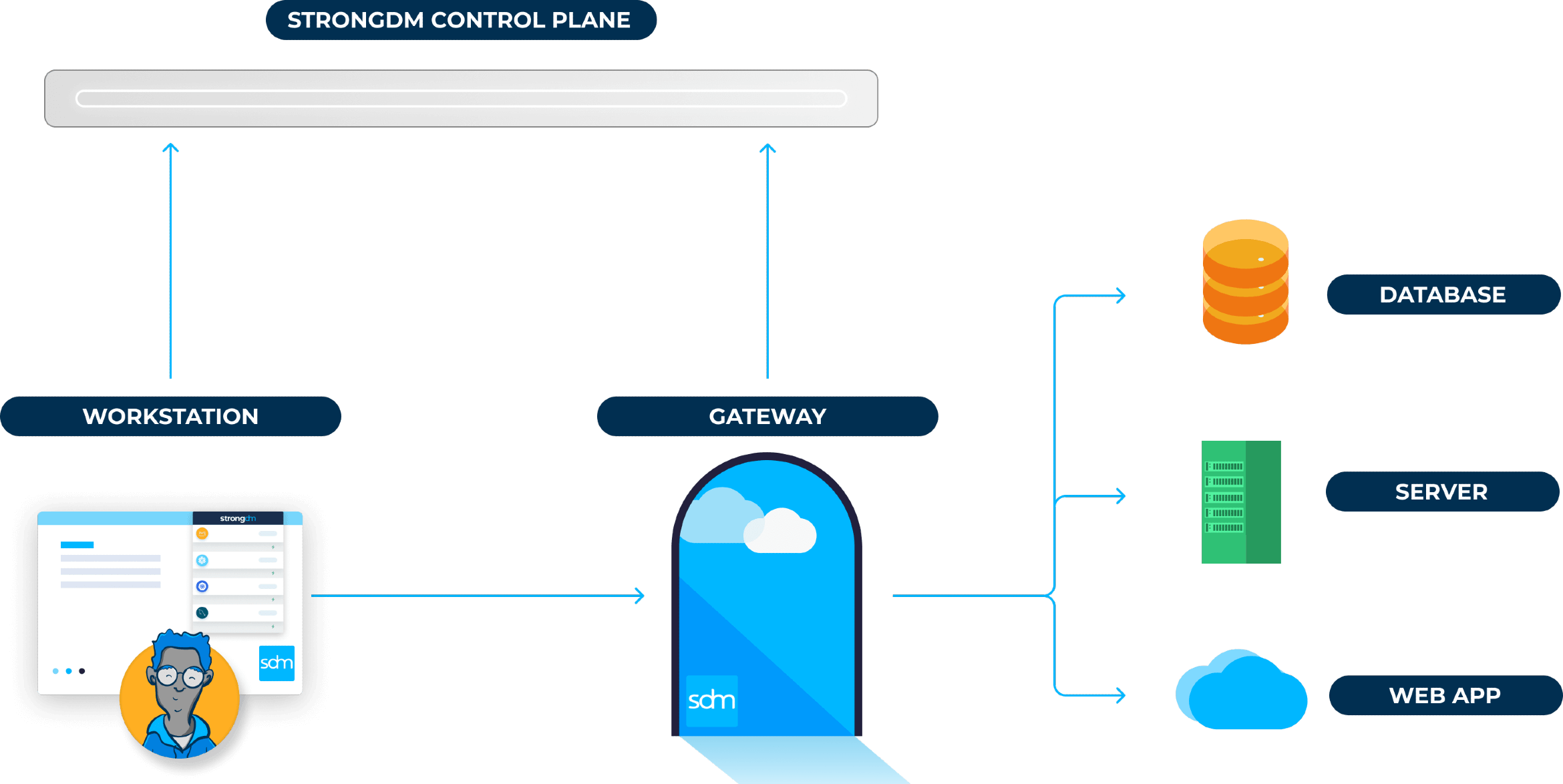
- Role-based, attribute-based, & just-in-time access to infrastructure
- Connect any person or service to any infrastructure, anywhere
- Logging like you've never seen

CyberArk and StrongDM are two distinct privileged access management (PAM) solutions designed to provide secure access to critical infrastructure. While there are some similarities in functionality their approach to securing access is different.
What Is CyberArk?
CyberArk’s Privileged Access Manager is designed to secure, manage, and monitor privileged accounts within an organization. End users are typically comprised of a small subset of the engineering or IT team and tend to be systems administrators (sysadmins) or databases administrators (DBAs). The toolset is designed primarily for legacy server operating systems, like Windows, or older database management systems, such as Oracle, Sybase, or DB2. It was originally designed to run on Windows workstations and integrate with LDAP and Active Directory. Access is typically done through a web interface or locally installed utility. Components of the system include a password vault, central policy manager, and privileged session manager. In most cases, CyberArk is able to provide an audit trail of queries and session replays.
What Is StrongDM?
StrongDM is a proxy that combines authentication, authorization, networking, and observability into a single product. The product is designed to unify and simplify privileged access workflows by providing low-friction connectivity to every piece of infrastructure in your stack.
- DevOps: DevOps teams can provision and deprovision access to specific instances, servers, or databases, in a matter of clicks.
- Security & Compliance: Security and compliance teams gain full visibility into “who did what when” on each system, including video playback of what individual users have executed on specific systems. For compliance, full records are kept of “who was in each system and what were they doing” at any given point in time.
- Admins: Access to critical infrastructure can be granted and revoked quickly and easily, greatly simplifying user onboarding and offboarding, provisioning for third parties, and the ability to provide access for a specified period of time. Users, roles, and access are easily managed via an Admin UI (CLI available as well).
StrongDM vs. CyberArk: What’s the Difference?
There are several key capabilities that differentiate StrongDM from CyberArk as access management solutions.
1. Agentless Architecture
StrongDM does not require agents to be installed on end resources. This means fewer administrative headaches in managing the solution and faster time-to-value for the product. CyberArk’s architecture requires seven servers, plus the CyberArk vault, to implement. Each component needs to be working in order for PAM to be implemented. This agent-based design makes it difficult to manage and exposes it to several places for failure. The complexity of deployment also requires professional services.
💡Make it easy: Agentless architecture makes it easy to deploy, manage, and maintain StrongDM. Enforce just-in-time (JIT) security policies to cloud-native and hybrid infrastructures. Try it yourself.
2. Scalability
StrongDM leverages a true cloud-first approach, making it easier to scale in a single environment across multiple regions. This is particularly important for large enterprises. CyberArk’s approach requires the installation and management of self-hosted components, and endpoint agents that add to the complexity of managing the solution and decreasing flexibility.
3. Vault Agnostic
StrongDM has its own native vault and also integrates with multiple third-party vaults. Credentials are never exposed to end users, securely encrypted and not retrievable after setup. This allows vendors flexibility in their vault vendor and leverage existing security investments. CyberArk requires companies to manage access strictly with the CyberArk Vault.
4. Breadth of Support
StrongDM has native protocol support for infrastructure on-premises or in the cloud, including cloud platforms like AWS, Azure, GCP, Kubernetes, and any cloud databases. CyberArk’s core focus is on legacy on-premises systems, such as RDP, SSH, IBM 3720, MMSQL. This limitation lacks access control and visibility into all your resources. Support for modern cloud and databases often requires plugins and professional services.
5. Just-in-Time Access
StrongDM supports Just-in-Time access to databases, cloud, servers, and clusters through Access Workflows. CyberArk is only able to support Just-in-Time access to a portion of the stack and does not support cloud managed databases or PaaS.
6. Total Cost of Ownership
StrongDM offers simple per user pricing, starting at $70/license, including secure access to all resource types. Deployment requires no professional services, and the agentless architecture makes it easy to implement, manage, and maintain. CyberArk’s products are some of the most expensive on the market, with a high total cost of ownership. CyberArk requires additional hardware costs, has high licensing costs and you need to buy Professional Services for deployment and management. Operational costs are high with multiple systems and components to maintain.
StrongDM or CyberArk: Which One is Better for You?
| StrongDM | CyberArk | |
|---|---|---|
| Completeness of Offering |
||
| Supports 100+ protocols (both cloud-native & on-prem) including DBs, Amazon EC2, MongoDB, Redis, Kubernetes, Docker & more | ✔ | ✗ |
| Ease of Use |
||
| No install on servers | ✔ | ✗ |
| Multiple and concurrent vault support | ✔ | ✗ |
| Security |
||
| Actionable Reporting (unused privileged access, sensitive resource access grants, and access review) | ✔ | ✗ |
| High Availability | ✔ | ✗ |
| Disaster Recovery | ✔ | ✗ |
| Pricing |
||
| Cost/User includes all resource types | ✔ | ✗ |
Conclusion
StrongDM is built for an organization's entire technical staff, not just developers. It’s easy to adopt by end users because it seamlessly integrates with existing tools and workflows including identity providers and vault solutions. StrongDM has superior reliability and a more cost effective pricing model. See StrongDM in action, book a demo.
About the Author
Fazila Malik, Sales Enablement Manager, as an accomplished Product Marketing Manager in the technology industry with over 5 years of experience, Fazila transitioned to a Sales Enablement leader position passionate about empowering go-to-market teams to excel in their roles. Throughout her career, she has worked with a range of technology products, including software applications and cloud-based solutions. Fazila is a member of the Product Marketing Alliance and an AWS Cloud Certified Practitioner. To contact Fazila, visit her on LinkedIn.

You May Also Like