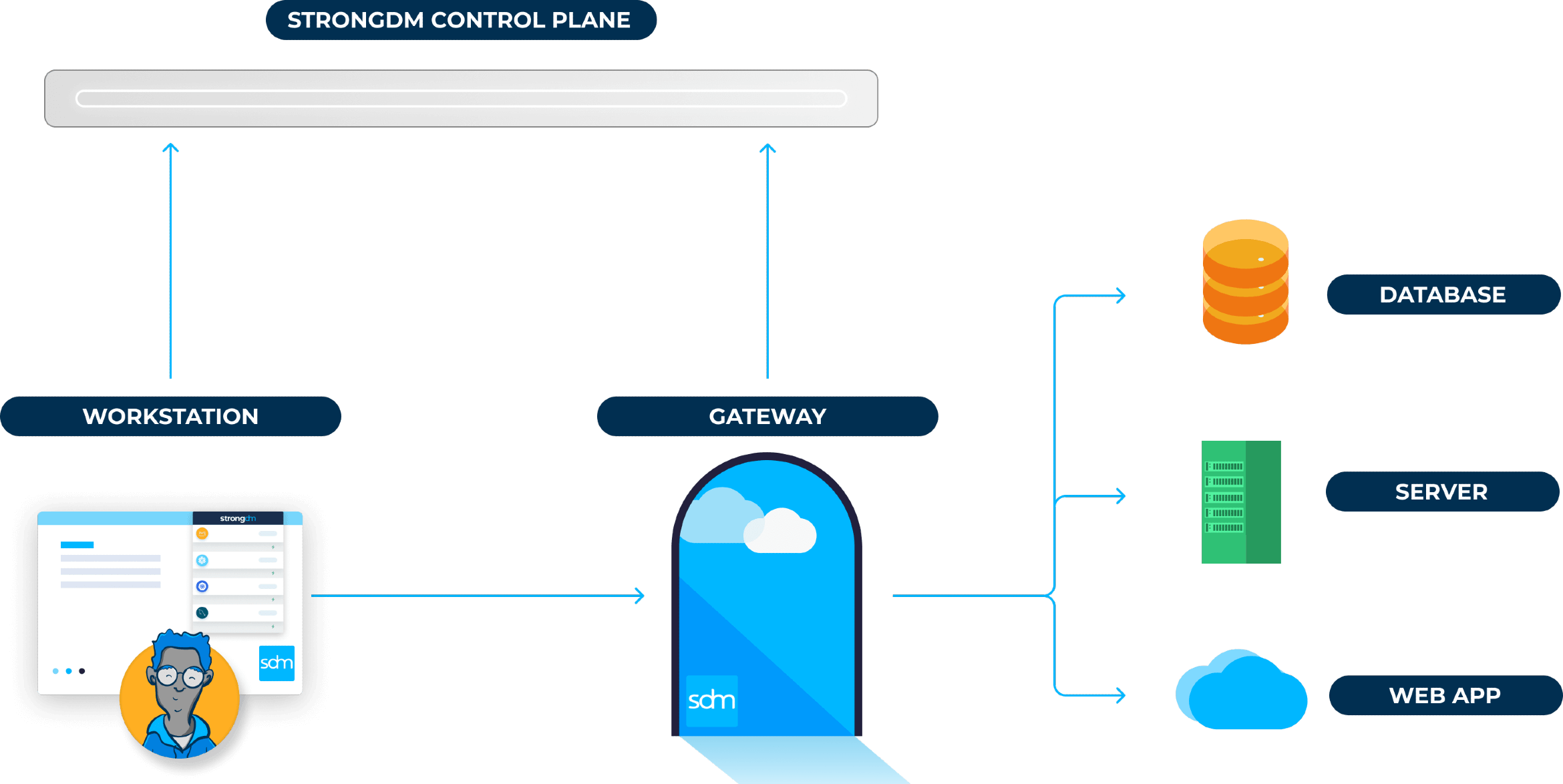
- Role-based, attribute-based, & just-in-time access to infrastructure
- Connect any person or service to any infrastructure, anywhere
- Logging like you've never seen

Both StrongDM and Teleport are access control solutions designed to provide secure access to databases, servers, clusters, and web apps. While there are some similarities between the two solutions, there are also some key differences in terms of product capabilities and overall value.
What Is Teleport?
Teleport provides access management for cloud-native infrastructures by acting as an access and authentication proxy for SSH and Kubernetes APIs. It's intended as a replacement for the remote login protocol, sshd, and it works with existing OpenSSH clients and servers as-is. The Teleport solution gives administrators the ability to set up access for groups of users to groups of servers, called clusters, and implements role-based access control (RBAC) to allow differing levels of access to different clusters. Teleport does not provide individual server credentials to users, which reduces the administrative impact of rotating and removing credentials.
What Is StrongDM?
StrongDM is a Zero Trust PAM platform that extends the capabilities of traditional privileged access management (PAM) to support all modern infrastructure, including databases, servers, Kubernetes clusters, clouds, and web applications. StrongDM combines authentication, authorization, networking, and observability into a single platform, providing secure and auditable access for the precise amount of time that access is needed. The product is designed to unify and simplify privileged access workflows by providing low-friction, dynamic connectivity to virtually every piece of infrastructure in your stack.
- DevOps: DevOps teams can provision and deprovision access to specific instances, servers, or databases, in a matter of clicks.
- Security & Compliance: Security and compliance teams gain full visibility into “who did what when” on each system, including video playback of what individual users have executed on specific systems. For compliance, full records are kept of “who was in each system and what were they doing” at any given point in time.
- Admins: Access to critical infrastructure can be granted and revoked quickly and easily, greatly simplifying user onboarding and offboarding, provisioning for third parties, and the ability to provide access for a specified period of time. Users, roles, and access are easily managed via an Admin UI (CLI available as well).
StrongDM vs. Teleport: What’s the Difference?
StrongDM offers several key capabilities that differentiate it from Teleport as an access management solution. This includes:
1. Support a Greater Breadth of Resources
StrongDM supports a much larger variety of systems and protocols, including older systems that enterprises still rely on. StrongDM allows users to authenticate using credentials, cloud-native authentication, or certificate-based authentication. Teleport's solution, however, lacks support for legacy systems and authentication protocols means that they are a point solution for modern cloud architecture. Teleport only supports more modern systems that will allow their certificate-based authentication.
The Teleport agents run as root in every server you want to audit, creating a new attack vector and a new surface to protect. This also limits user access to critical infrastructure in the event that Teleport goes down. While Teleport does offer an agentless mode, it offers very limited features that do not include role-based access controls or granular auditing.
2. Leverage Your Existing Security Investment
StrongDM can leverage existing integrations with your vault, PAM, or IGA solutions and give you time to transition on your own schedule. Teleport does not integrate with other elements of the security ecosystem, forcing you to replicate your investment in IGA, device posture, etc.
3. Reliability
StrongDM updates daily without any downtime. Whereas, Teleport cloud is unreliable and availability numbers are inaccurate. When Teleport requires an update it results in downtime which means you can lose access to your critical systems for up to 6 hours. When there is a partial outage customers also lose all access to audit data putting compliance at risk.
4. Simplify Identity Lifecycle Management
StrongDM supports SCIM integration with identity providers to sync user and group provisioning, and this automates joiner, mover, leaver workflows. Teleport only supports certificates and cloud provider IAM authentication, and this greatly limits the systems they can connect to and your freedom of operation.
5. Easier to Adopt, Manage, and Maintain
StrongDM does not require agents to be installed on end resources. This means fewer administrative headaches in managing the solution and faster time-to-value for the product. With Teleport, you need to deploy an agent on every target resource as well as two different Teleport services (proxy and authentication).
The Teleport agents run as root in every server you want to audit, creating a new attack vector and a new surface to protect. This also limits user access to critical infrastructure in the event that Teleport goes down. While Teleport has an agentless mode, it offers very limited features that do not include role-based access controls or granular auditing.
💡Make it easy: Agentless architecture makes it easy to deploy, manage, and maintain StrongDM. Enforce just-in-time (JIT) security policies to cloud-native and hybrid infrastructures. Agents cannot be deployed on cloud-managed databases limiting Teleport’s agent design to provide JIT to all resources. Try it yourself.
StrongDM updates daily without any downtime, whereas Teleport places the burden of configuration management and high availability on the customer. Teleport cloud is unreliable, and availability numbers are inaccurate. When Teleport requires an update, it results in downtime, which means you can lose access to your critical systems for up to 6 hours. When there is a partial outage, customers also lose all access to audit data putting compliance at risk.
6. Secure and Auditable
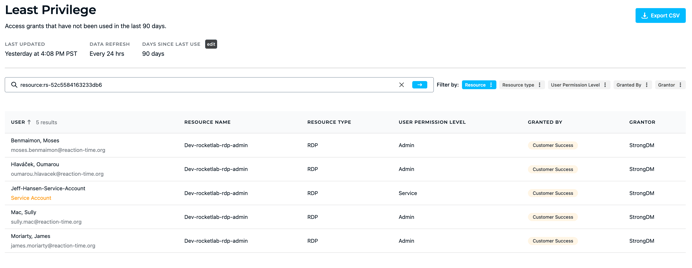
StrongDM provides Advanced Insights to report on unused privileged access, sensitive access grants, and an overall access review at any point in time. Teleport has no such capability, making it impossible to prove to an auditor who had access to which systems when.
💡Make it easy: Out-of-the-box reports quantify your access permissions. Track metrics to enforce least privilege, prove security policies are enforced, answer access audit questions efficiently, and simplify incident investigations. Try it yourself.
7. Context-based Policy Control
StrongDM allows customers to define context-aware policies against StrongDM resources and enforce them with a centralized configuration. Teleport offers an access graph for comprehensive visibility of policies without centralized access management capabilities.
8. Pricing
StrongDM offers simple pricing, with the essentials package starting at $70/user. Teleport offers licensing by user and by resource, making costs add up quickly.
StrongDM or Teleport: Which One is Better for You?
| StrongDM | Teleport | |
|---|---|---|
| Completeness of Offering |
||
| Identity Lifecycle Management | ✔ | ✗ |
| Context-based Policy | ✔ | ✗ |
| Ease of Use |
||
| No install on servers | ✔ | ✗ |
| Multiple and concurrent vault support | ✔ | ✗ |
| High Availability | ✔ | ✗ |
| Disaster Recovery | ✔ | ✗ |
| Security |
||
| Actionable Reporting (unused privileged access, sensitive resource access grants, and access review) | ✔ | ✗ |
| Pricing |
||
| Cost/User includes all resource types | ✔ | ✗ |
Conclusion
StrongDM is built for an organization's entire technical staff, not just developers. It’s easy to adopt by end users because it seamlessly integrates with existing tools and workflows including identity providers and vault solutions. StrongDM has superior reliability and a more cost-effective pricing model. See StrongDM in action, book a demo.
About the Author
Fazila Malik, Sales Enablement Manager, as an accomplished Product Marketing Manager in the technology industry with over 5 years of experience, Fazila transitioned to a Sales Enablement leader position passionate about empowering go-to-market teams to excel in their roles. Throughout her career, she has worked with a range of technology products, including software applications and cloud-based solutions. Fazila is a member of the Product Marketing Alliance and an AWS Cloud Certified Practitioner. To contact Fazila, visit her on LinkedIn.

You May Also Like