
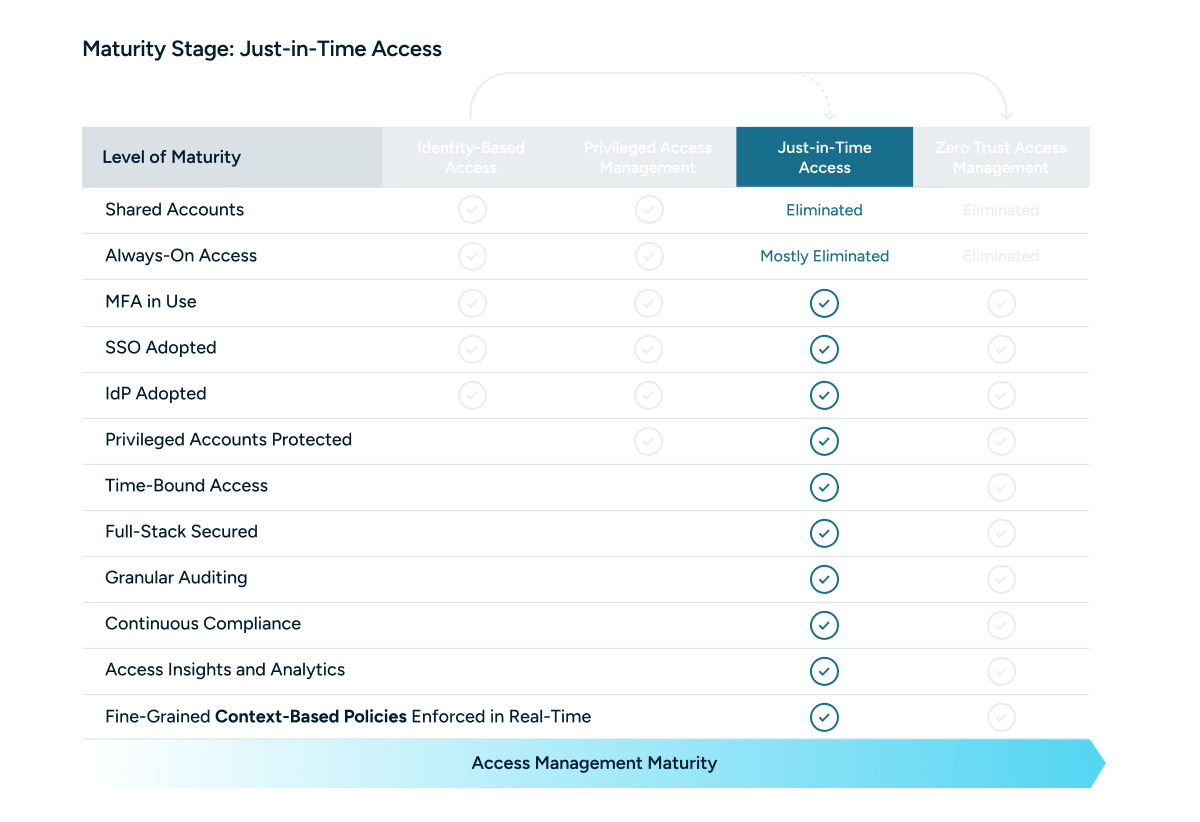
Level 3 of the maturity model is where the temporal aspect of the access lifecycle begins to come into play. This is where organizations begin to adopt Just-in-Time access (JIT), ultimately paving the way for Zero Standing Privileges (ZSP).
SAMM: Just-in-Time Access
Defining Just-in-Time Access & Zero Standing Privileges
Often, there is confusion between Just-in-Time Access and Zero Standing Privileges. The easiest way to delineate between them is keep in mind that Just-in-Time Access is a component of Zero Standing Privileges.
Just-in-Time access allows users to provision credentials when needed and de-provision them once they are no longer required. This approach minimizes the window of opportunity for unauthorized access and reduces the risk associated with long-lived credentials.
Benefits of JIT:
- Reduced Attack Surface: By limiting the time credentials exist, malicious actors have fewer opportunities to exploit them.
- Improved Compliance: Temporary access aligns with compliance requirements that mandate least privilege and access controls.
- Operational Efficiency: Automating access provisioning and deprovisioning can streamline workflows and reduce administrative overhead.
Zero Standing Privileges is an access management methodology that requires that no credentials exist in perpetuity; all access is provided in a Just-in-Time manner. It represents a more comprehensive adoption of JIT principles across the entire organization.
Benefits of ZSP:
- Maximum Security Posture: Eliminating permanent credentials greatly minimizes the risk of credential misuse or theft.
- Adaptive Access Control: Access decisions are made in real-time based on current context and policies.
- Simplified Credential Management: Reduces the need to manage and rotate long-lived credentials.
|
Attributes of Level 3 Access
|
|
Limited-Scope JIT: Admin Accounts
|
Just-in-time access has started to be embraced. It is typically prioritized for accounts with elevated privileges or access to sensitive or regulated data.
Lower priority access may still be “always on,” meaning credentials and accounts are primarily de-provisioned when an organizational change occurs.
|
|
Access Workflows Simplify Provisioning and Deprovisioning
|
End-users can request and obtain access quickly and efficiently, with the process being simple, fast, and automated where appropriate, enhancing productivity and security.
|
Regarding Level 3, it is key to remember that Just-in-Time access also represents an expanded scope in the types of accounts supported. Where privileged access only supports critical accounts, Just-in-Time access begins to lay the foundation for dynamic access across your technical teams.
|
Technologies Often Used as Part of Level 3
|
|
Modern PAM or Cloud PAM
|
Your organization has adopted tools that enable dynamic provisioning and de-provisioning of credentials and provide secure access to a wider range of tools and environments than traditional PAM (such as Clouds, Kubernetes, etc.).
|
Access Lifecycle: Mixed
Level 3 has a combination of always-on access and Just-in-Time access. Fundamentally, it is a middle step on the path towards Zero Trust access, where you’re ensuring that the credentials that pose the biggest risk in the case of a breach are provisioned dynamically, and credentials with less risk continue to exist in perpetuity.
From JIT to Zero Trust Access: Achieving Zero Standing Privileges and Enforcing Context-Based Policies
The ultimate goal for access management is Zero-Trust Access, which prioritizes zero-standing privileges. Zero-trust access management means that no access exists except for the needed moments and only when the context surrounding the request deems it appropriate.
But it doesn’t stop there. Zero Trust Access also incorporates context-based policy enforcement and policy-based action control, enhancing security by dynamically adjusting access permissions based on real-time contextual information and controlling the actions users can perform once access is granted.
Context-Based Policy Enforcement
Context-based policy enforcement ensures that access decisions are not solely based on static credentials or roles but also dynamic attributes such as:
- User Identity and Role: Verifies that the user's role aligns with the access request.
- Time of Access: Restricts access to specific times of the day or week.
- Location: Considers geographic location or network origin of the request.
- Device Posture: Checks the security status of the device being used (e.g., OS version, antivirus status).
- Behavior Patterns: Monitors user behavior for anomalies compared to established patterns.
By evaluating these factors (and any others you would like to include) in real-time, organizations can enforce fine-grained policies that grant access only when all contextual conditions meet predefined security criteria. For example, a user can access a resource only during business hours from a safe corporate device within the office network.
Policy-Based Action Control*
Policy-based action control goes beyond granting or denying access—it defines what actions a user can perform once access is granted. This includes:
- Command Restrictions: Limiting the commands or queries a user can execute.
- Data Access Levels: Allowing read-only access versus read-write permissions.
- Session Controls: Setting time limits on sessions or requiring re-authentication for sensitive actions.
- Transaction Monitoring: Tracking specific activities within a session for compliance and security.
By implementing these controls, organizations can minimize the risk of unauthorized activities, data exfiltration, or accidental damage. For instance, an engineer might have access to view production databases but cannot modify data without additional approval.
*StrongDM supports Action Control for Postgres databases, with additional resource types coming in 2025.
Bringing It All Together
Zero Trust access provides the resources and tools to simplify how your end-users interact with and request access while ensuring that all access is appropriate and secure. This approach:
- Applies JIT Access Universally: Extends Just-in-Time access to everyone in your technical stack, not just privileged users.
- Enhances Audit and Compliance: Keeps all access and activities easily available for audit purposes, meeting continuous compliance requirements.
- Adapts in Real Time: It enforces fine-grained, context-based policies and action controls dynamically, adjusting to changing conditions and threats.
By integrating context-based policy enforcement and policy-based action control, organizations fully embrace Zero Trust access. This comprehensive strategy ensures that access is granted only when necessary, under the right conditions, and with appropriate limitations on user actions—making access work for you in the most secure and efficient way possible.













st.jpg?width=1200&height=916&name=Top%208%20Privileged%20Access%20Management%20Opt%20(PAM)st.jpg)





