Whether you’re looking to achieve SOC 2 compliance, or just want to learn more about it, your Googling is bound to lead you to a wealth of articles chock full of buzzwords and acronym soup. In this post, we will provide a guide with definitions, links and resources to gain a solid understanding of everything you need to know about SOC 2 audits.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Policy
- Compliance
- SOC 2
- Authentication
- Databases
- Identity and Access Management
- Compare
- Team
- Product
- Integrations
- Kubernetes
- AWS
- Engineering
- Productivity
- Podcasts
- Observability
- SSH
- HIPAA
- ISO 27001
- Dynamic Access Management
- Role-Based Access Control
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI

In this post, we will help you get started with a hierarchy to follow, as well as a summary of each individual SOC 2 policy.

It has never been easier for your company to build new infrastructure. In just a few clicks, you can spin up shiny new servers and databases in the cloud and start using them in seconds. However, in the rush to deploy new services so quickly, companies often let information security be an ...

BYOD lets employees use their own smartphones, tablets, or laptops to access company resources and perform work-related tasks, allowing them to work from anywhere. This practice offers advantages like increased productivity and company savings on hardware costs. Employees are often more proficient with their own devices, which can mean a more comfortable work environment and result in higher job satisfaction.

At Token Security our goal is to teach the core curriculum for modern DevSecOps. Each week we will deep dive with an expert so you walk away with practical advice to apply to your team today. No fluff, no buzzwords. This week Jeff Burkhart, Senior Engineering Director at Zymergen talks code reviews, code review fatigue, and what to do when agile becomes tedious.

Despite thousands of articles, there’s shockingly little actionable advice to help startups complete SOC 2. One area that usually requires some remediation is access controls. Most teams don’t have answers when auditors ask “who has access to a specific database or server and what queries did they execute?” That’s why we started strongDM- to manage and monitor access to every database, server, & environment.
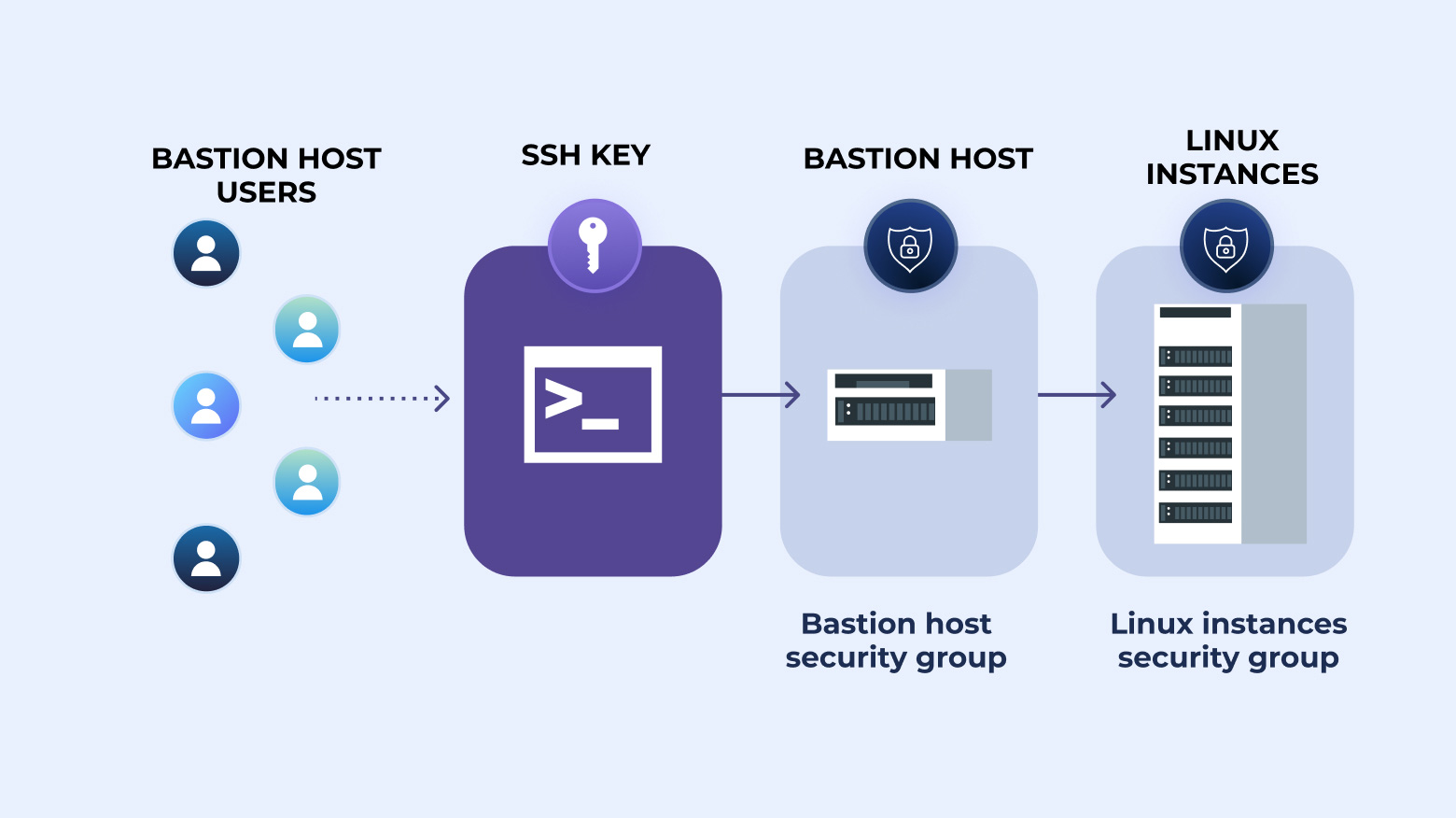
How to create an SSH key for your bastion host and ways you can streamline the bastion host login process without compromising the security of the key.

A staggering amount of cybersecurity breaches are caused by software vulnerabilities. From the early worms of the 1980s through the early 2000s - like Blaster, Code Red, and Melissa - to the notable Petya and WannaCry of the past few years, these vulnerabilities are all rooted in software flaws that allowed systems to be exploited. A software development lifecycle (SDLC) policy helps your company not suffer a similar fate by ensuring software goes through a testing process, is built as securely
This episode Max Saltonstall sits down in Manhattan with Quiessence Phillips, Deputy CISO and Head of Threat Management, City of New York and Colin Ahern, Deputy CISO, City of New York.
Documenting and communicating policy and system changes in your organization can be an arduous task. But the effort becomes more manageable when you have a plan in place before an emergency.

The what, where, why and how of audit logging and review for IT security investigations and compliance requirements.
Confusing a SOC 1 vs SOC 2 audit is easy. While both compliance frameworks attest to the controls used within your organization, the frameworks differ in focus. SOC 1 looks at your organization’s financial reporting, while SOC 2 focuses on how you secure and protect customer data. This blog post will focus on exploring the differences between SOC 1 vs SOC 2.

In the workstation security policy, you will define rules intended to reduce the risk of data loss/exposure through workstations.

You wouldn’t leave the house without making sure your doors and windows were locked, and that any valuables were hidden or secured in a safe. That way, if you were robbed, the burglar would have a difficult time accessing your most precious assets. In the same way, you need to make sure your organization’s critical data is well protected.

