StrongDM’s Next-Gen Kubernetes provides secure, seamless access to Kubernetes clusters at scale. By eliminating standing privileges and enforcing Zero Trust security principles, StrongDM helps security teams maintain tight access controls without slowing down DevOps workflows.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI
Kubernetes observability is the practice of monitoring and analyzing a Kubernetes environment through metrics, logs, and traces to gain visibility into system performance and health. It enables teams to detect and resolve issues proactively, optimize resource utilization, and maintain cluster reliability through real-time insights and automated monitoring tools.
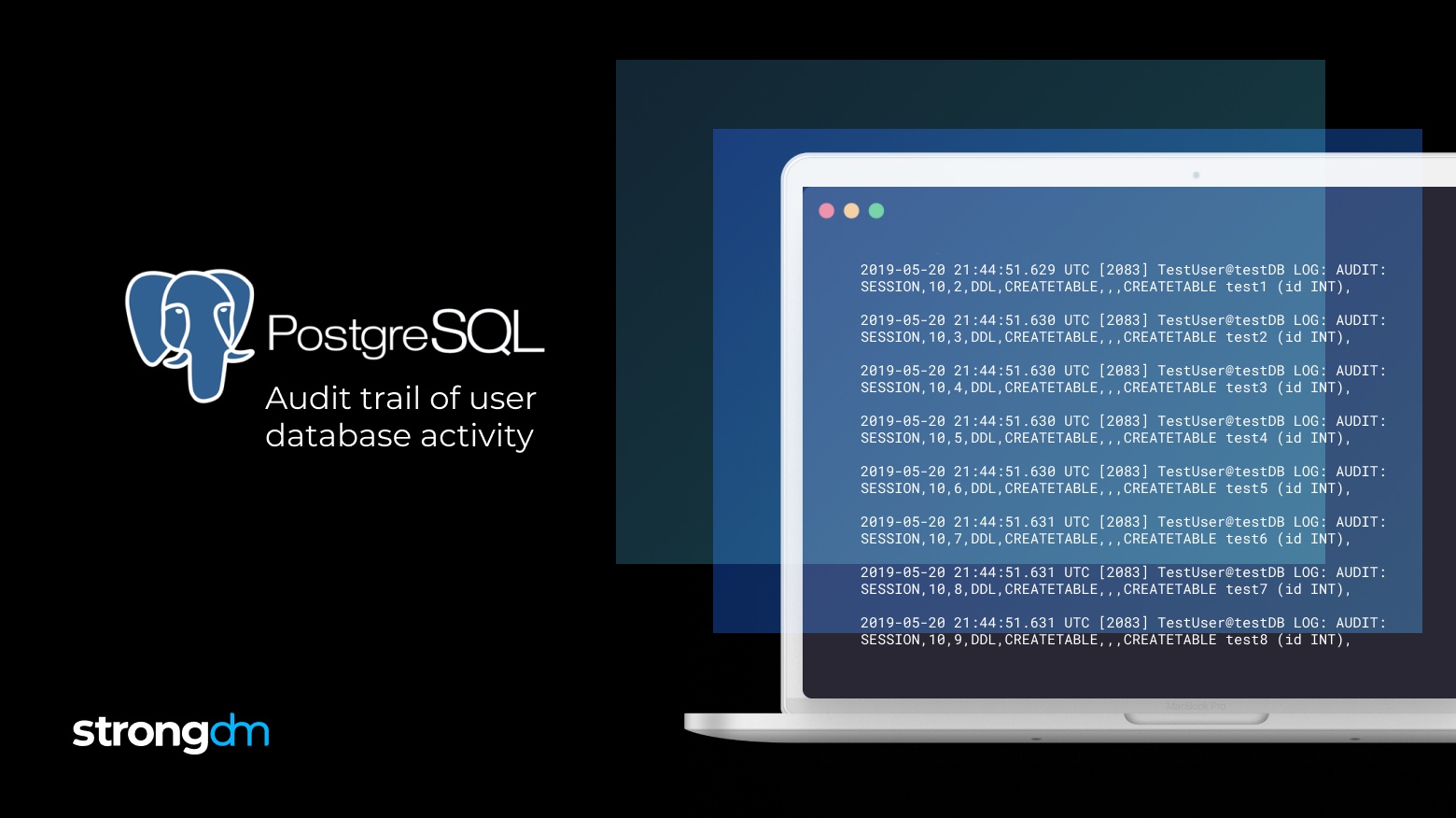
Audit logging is essential for maintaining a secure and compliant IT infrastructure. By capturing detailed records of system activities, audit logs provide insights into user actions, system events, and potential security threats. Understanding audit logging helps you identify and address vulnerabilities, ensure regulatory compliance, and enhance overall system integrity.

In this article, we will spotlight 11 log management best practices you should know to build efficient logging and monitoring programs. You’ll learn how to establish policies and take a proactive approach to collecting, analyzing, and storing business-critical log data. By the end of this article, you’ll have a clearer understanding of how logs can help security teams detect suspicious activity, address system performance issues, identify trends and opportunities, improve regulatory compliance,

Two of the most important questions in security are: who accessed what, and when did they access it? If you have any Linux or Unix machines, you’ll likely find answers in the sshd log. sshd is the Secure Shell Daemon, which allows remote access to the system. In this article, we’ll look at how to view ssh logs.
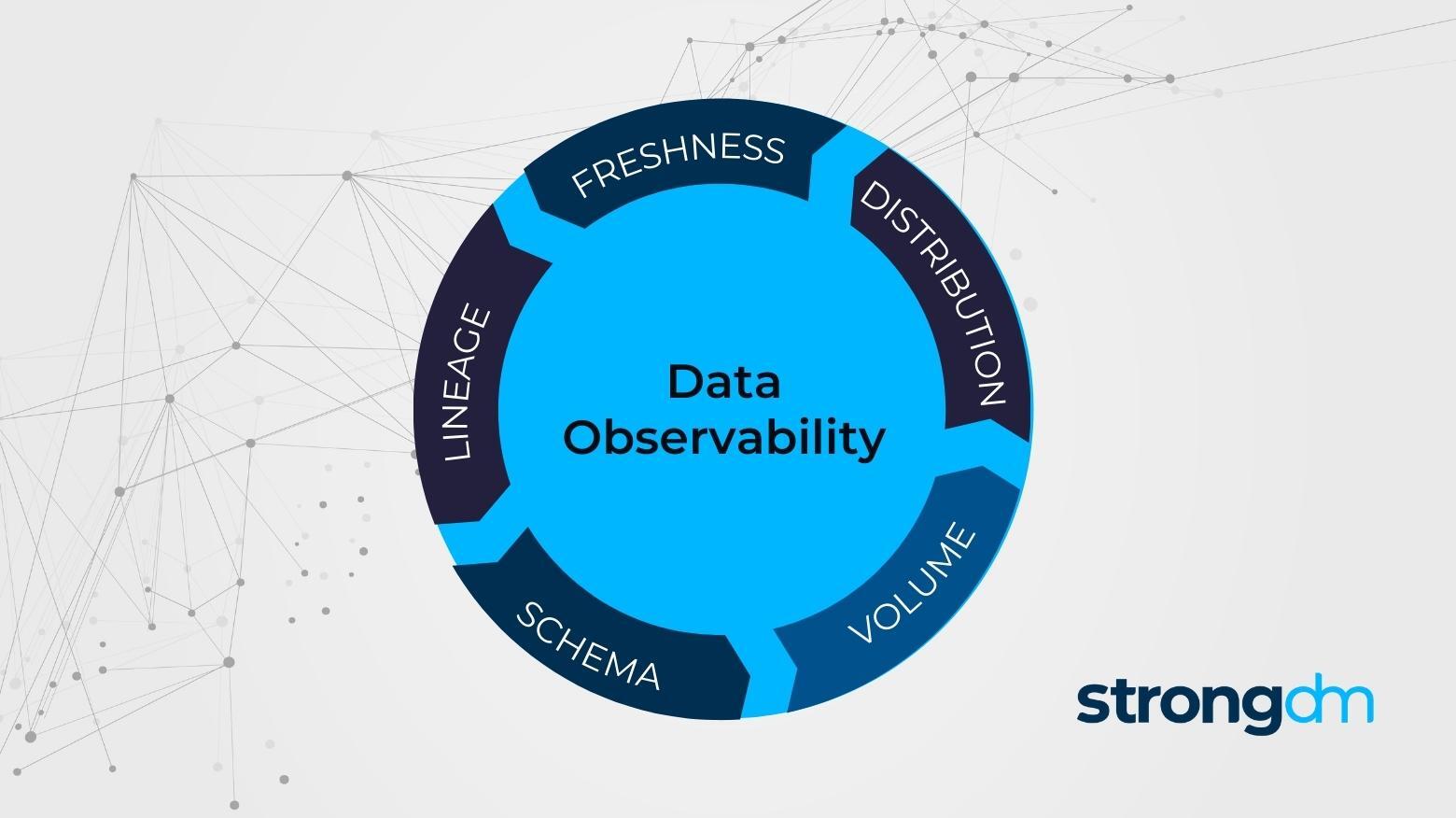
Data observability can help companies understand, monitor, and manage their data across the full tech stack. In this article, you’ll learn what data observability is, the differences between data observability, monitoring, and data quality, and what information you can track with data observability. By the end of this article, you’ll discover how to implement data observability and find the right data observability tools for your organization.

In this article, we’ll focus on the three pillars of observability. You’ll learn about the definitions, strengths, and limitations of each pillar. By the end of this article, you’ll know about their individual contributions and typical real-world challenges, tying them together for an overall view of your system.
Observability and monitoring are often used interchangeably, but there are key differences you should know between these two IT terms and the tools that enable them. In this article, we’ll explore the relationship and differences between observability vs. monitoring. Plus, you’ll learn about what makes observability and monitoring different from telemetry and application performance monitoring (APM).

What is a “mindset of cloud-native security”? 🤔 That’s a great question. That’s why Justin McCarthy, CTO and co-founder of strongDM, recently sat down with Mike Vizard at Container Journal and a panel of technology experts to discuss just that—and how to implement it without creating friction.

Configure the hosts for logging verbose data, and then send the logs to a cloud provider for long-term storage and access.

SSH audit logs allow you to determine, either retroactively or in real-time, when an unauthorized or destructive action was taken, and by whom.

The what, where, why and how of audit logging and review for IT security investigations and compliance requirements.