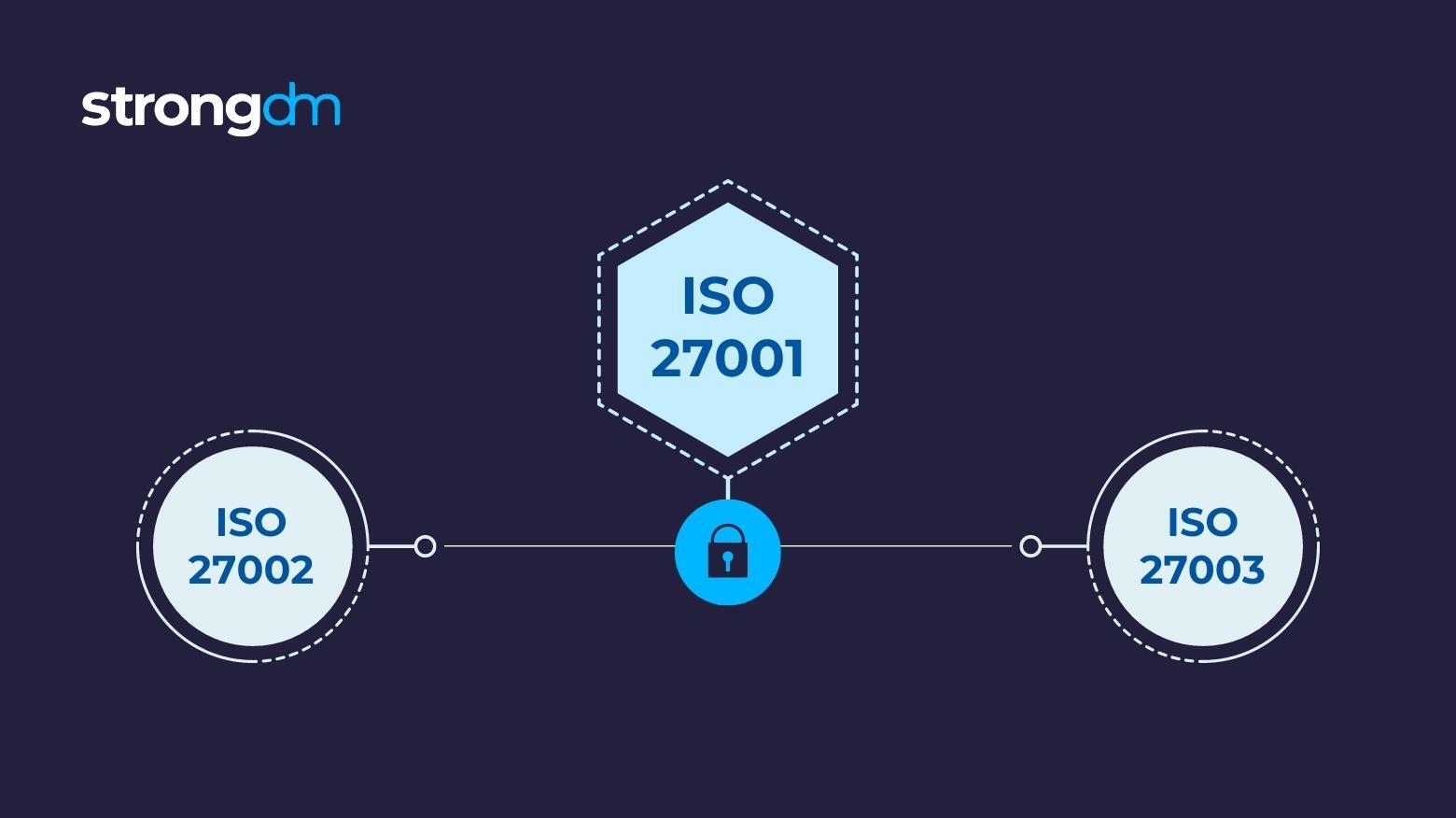
Organizations around the world rely on the standards set in the ISO 27000 series for information security management best practices. In this article, we’ll compare the first three standards in the ISO/IEC 27000 family: ISO 27001 vs. 27002 vs. 27003. By the end, you’ll have a better understanding of what each standard covers, how they differ from one another, and when to use them.
Posts by Category:
- Security
- Access
- DevOps
- Auditing
- Privileged Access Management
- Policy
- Zero Trust
- Compliance
- SOC 2
- Authentication
- Databases
- Identity and Access Management
- Compare
- Team
- Product
- Integrations
- Kubernetes
- AWS
- Engineering
- Productivity
- Podcasts
- Observability
- SSH
- HIPAA
- ISO 27001
- Dynamic Access Management
- Role-Based Access Control
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI

In this article, we’ll walk you through the ISO 27001 checklist you’ll use en route to your cybersecurity certification. From assigning roles to implementing controls, assessing risks, and documenting your processes for future audits, you can use the ISO 27001 compliance checklist to ensure you’re on the right track for your official audit.
In this article, we’ll look at the overall price tag for one International Standards Organization certification (ISO 27001), along with some of the factors that impact costs and why they vary across organizations. You’ll learn about different ISO 27001 certification costs, from the audit, with its ISO 27001 exam cost, to implementation and maintenance. By the end of this article, you’ll get a sense of the factors involved in ISO 27001 certification and be able to compare quotes to decide your

SOC 2 and ISO 27001 both provide companies with strategic frameworks and standards to measure their security controls and systems against. But what’s the difference between SOC 2 vs. ISO 27001? In this article, we’ll provide an ISO 27001 and SOC 2 comparison, including what they are, what they have in common, which one is right for you, and how you can use these certifications to improve your overall cybersecurity posture.
Data loss prevention (DLP) can save organizations millions of dollars on data breaches every year. In this article, we will take a big-picture look at data loss prevention and discover how DLP tools and processes strengthen an enterprise’s security posture.

There are several different levels of SOC (Service Organization Control) reports and types, so it is easy to get them confused. This post will focus on outlining the path to SOC 2 Type 2.

Ways to narrow your SOC 2 audit scope to save your company time and money so you receive your SOC 2 report with fewer migraines.