Documenting and communicating policy and system changes in your organization can be an arduous task. But the effort becomes more manageable when you have a plan in place before an emergency.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI

In this episode Justin McCarthy sits down with Andrew Mulholland, head of core infrastructure at BuzzFeed to talk about security incident response, remote access policy, and a money-back guarantee for OSS.

The first step in this policy is to define the critical processes and assets necessary for you to maintain minimum business functions after a disaster.

The what, where, why and how of audit logging and review for IT security investigations and compliance requirements.

As you work through the rigorous SOC 2 requirements, it is easy to get tunnel vision because so much of your work focuses on protecting your customers and their information. But what about the vendors you work with? Do you have a third-party IT vendor management strategy to address the risks they bring to your organization?

Passwords are one of the most common targets for hackers, so it’s imperative that your company enforces a strong password policy. This policy will not only define the requirements of the password itself but the procedure your organization will use to select and securely manage passwords.
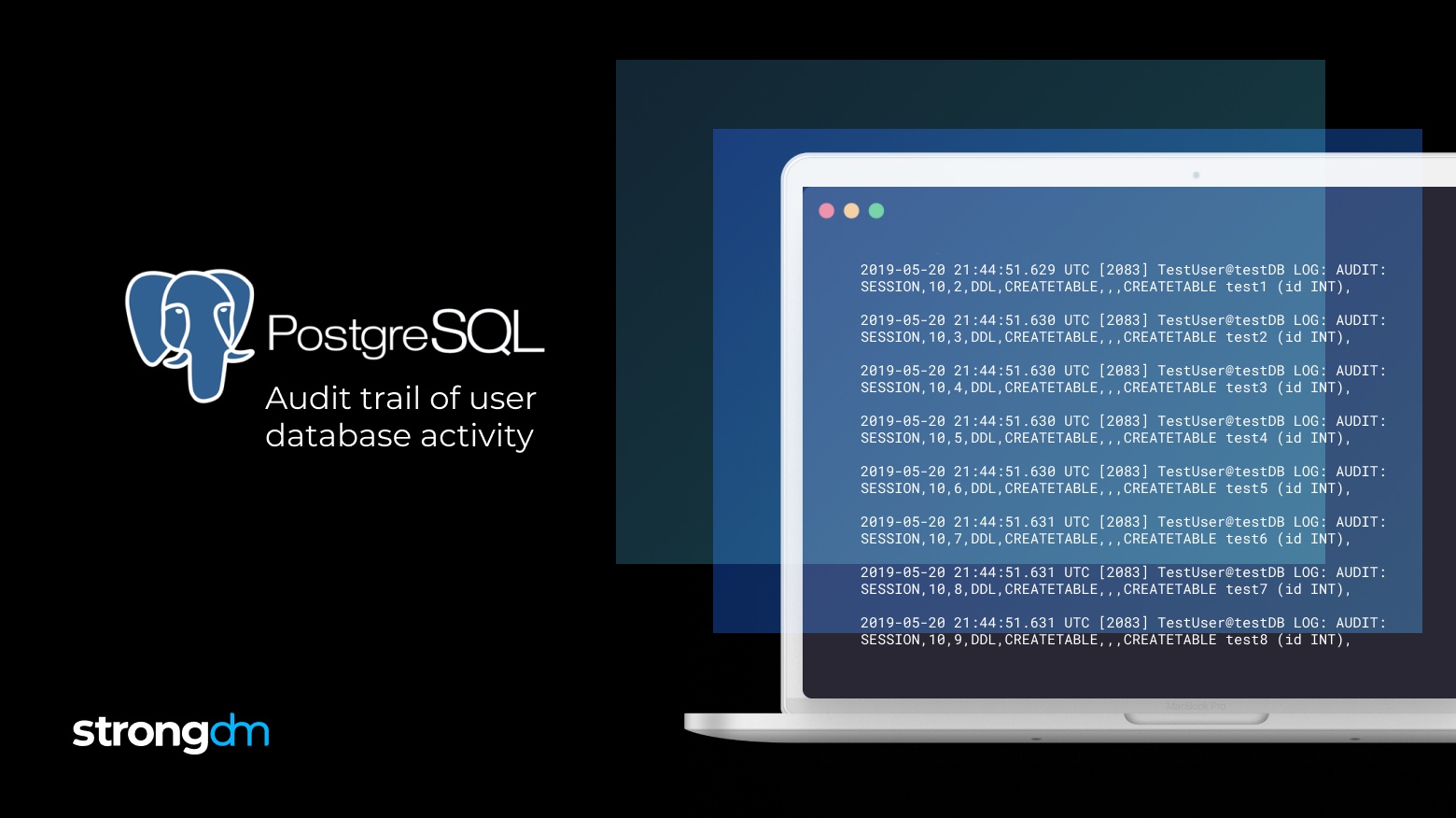
This is the first step to create an audit trail of PostgreSQL logs. Postgres can also output logs to any log destination in CSV by modifying the configuration.

The purpose of a Remote Access Policy is to keep your employees productive from anywhere without sacrificing security.

In the workstation security policy, you will define rules intended to reduce the risk of data loss/exposure through workstations.

You wouldn’t leave the house without making sure your doors and windows were locked, and that any valuables were hidden or secured in a safe. That way, if you were robbed, the burglar would have a difficult time accessing your most precious assets. In the same way, you need to make sure your organization’s critical data is well protected.
Should you host data on-premise or in the cloud? Who is responsible for security? The company who owns the data, the cloud provider, or both?
It's easy to focus on cybersecurity threats like social engineering and phishing. However, internal threats, such as human error and disgruntled employees, can be just as dangerous - and are often overlooked. A mature onboarding and termination policy that leverages least privilege access is essential to preventing a data breach.

A Business Continuity Policy is critical to your information security program & defines the critical steps your employees need to take after a disaster.