This article will cover statistics highlighting the extent of these cloud security breaches, who is most affected, how much money this is costing everyone, what the conduits of the security breaches are, and what people intend to do about it.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Policy
- Compliance
- SOC 2
- Authentication
- Databases
- Identity and Access Management
- Compare
- Team
- Product
- Integrations
- Kubernetes
- AWS
- Engineering
- Productivity
- Podcasts
- Observability
- SSH
- HIPAA
- ISO 27001
- Dynamic Access Management
- Role-Based Access Control
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI

In this article, we’ll explore what data exfiltration is, the difference between exfiltration of data and data leakage, and how to detect data exfiltration. You’ll learn the dangers of data exfiltration in cybersecurity, data exfiltration examples, and the types of exfiltrated data that malicious actors target most. By the end of this article, you’ll know what causes data exfiltration, common data exfiltration tactics, and how to prevent data exfiltration in your organization.
This article covers everything you need to know about anomaly detection and why anomaly detection is important for your organization’s security. You’ll learn about common challenges companies face when detecting anomalous data, types of anomaly detection, and anomaly detection methods your company can leverage. By the end of this article, you’ll know how to find anomalies in data and prevent irregular data incidents with practical anomaly detection models.
In this article, we cover the sensitive data definition and the main risks associated with it. You'll see real sensitive information examples and learn how sensitive data differs from personal data. By the end of this article, you'll understand what data is sensitive and how to protect it against cyber risks and exposures.
In this article, you’ll what a honeypot is what honeypots are used for, and the benefits and risks associated with them. You’ll also learn about the different types and examples of honeypots and how they work. By the end of the article, you’ll have a deeper understanding of honeypots in cyber security, and how a secure infrastructure access platform can help you safeguard your network, systems, and apps without using a honeypot.
As cyber threats have increased in recent years, more organizations are turning to cyber insurance to mitigate their financial risks. In this article, we’ll review cyber insurance basics, including what cybersecurity insurance is, how it works, what it covers, and what it costs. By the end, you will understand the different types of cyber insurance, the benefits of coverage, and how cyber insurance fits into a comprehensive security strategy.
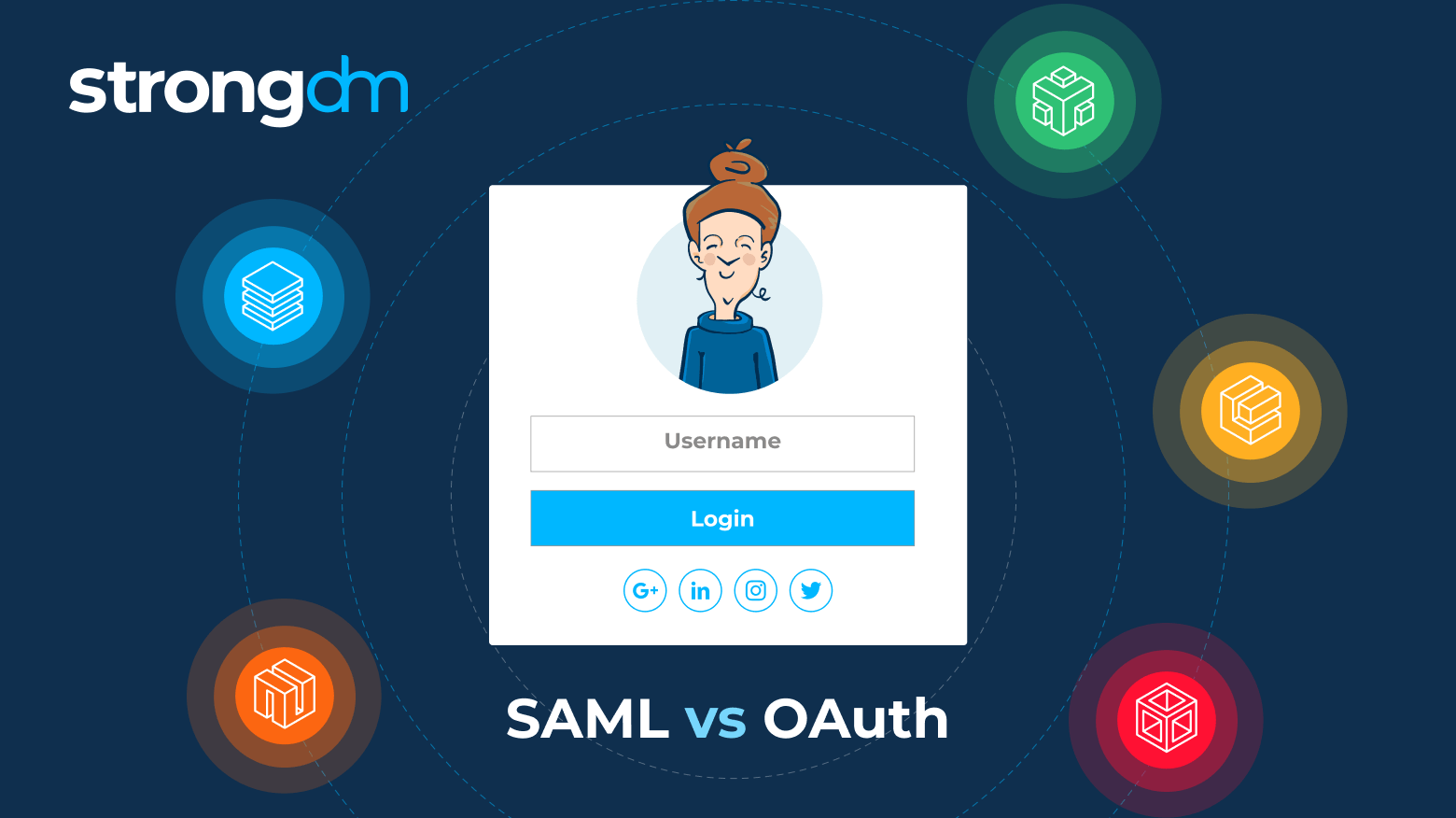
In this article, we will provide a high-level overview of the Security Assertion Markup Language (SAML) and Open Authorization (OAuth) information access frameworks. You’ll learn about the key similarities and differences between SAML and OAuth, the unique benefits of each framework, and specific use cases for each. By the end of this article, you’ll have a clear understanding of SAML and OAuth to help you determine which is right for your organization.
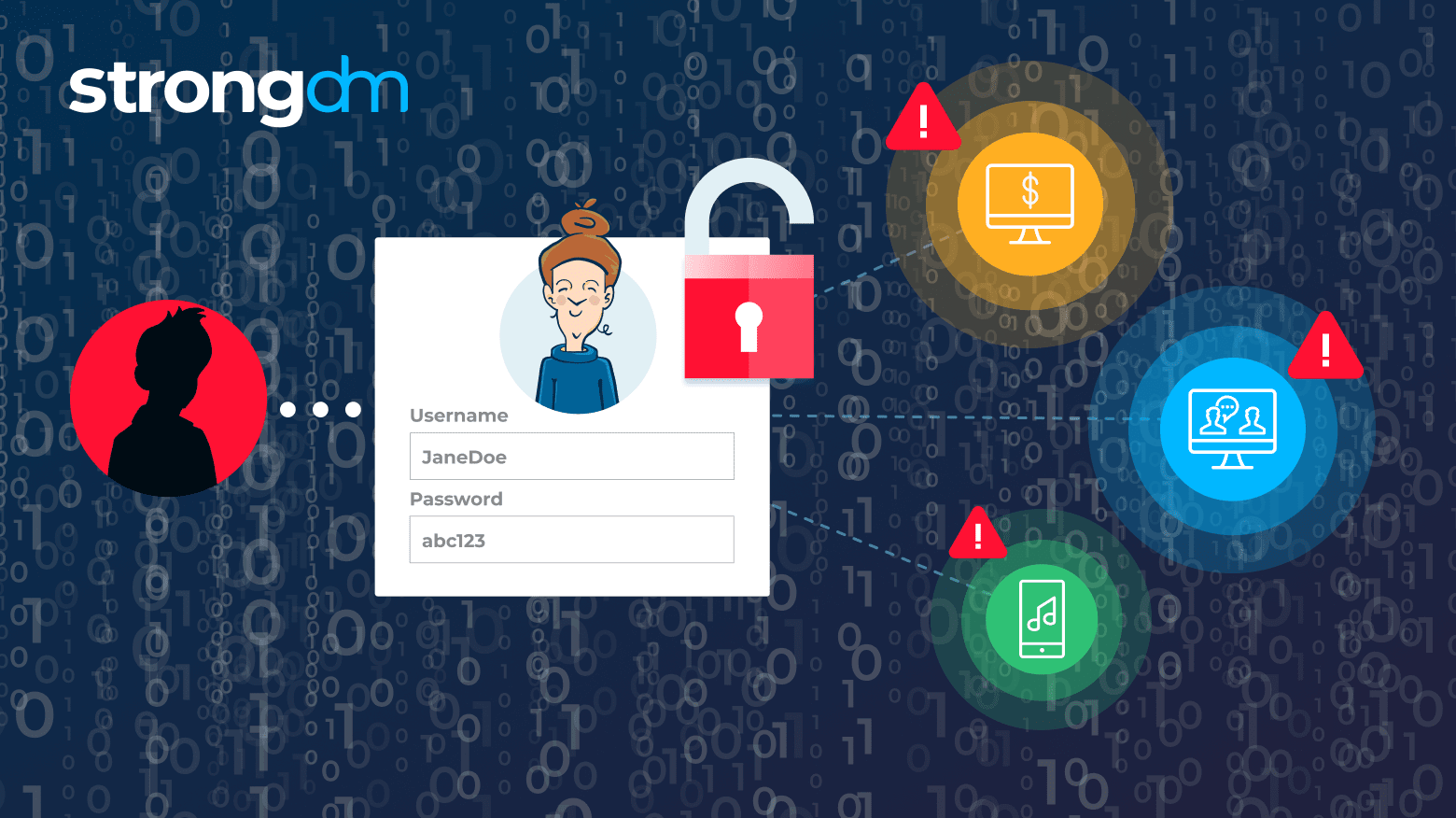
In this article, we’ll define credential stuffing and explain the risks that credential stuffing attacks pose to organizations and customers. We’ll cover recent examples of credential stuffing attacks and discuss how to detect and prevent them. By the end of the article, you should understand the full scope of credential stuffing, including how to protect your customers’ and employees’ account credentials with the right tools.
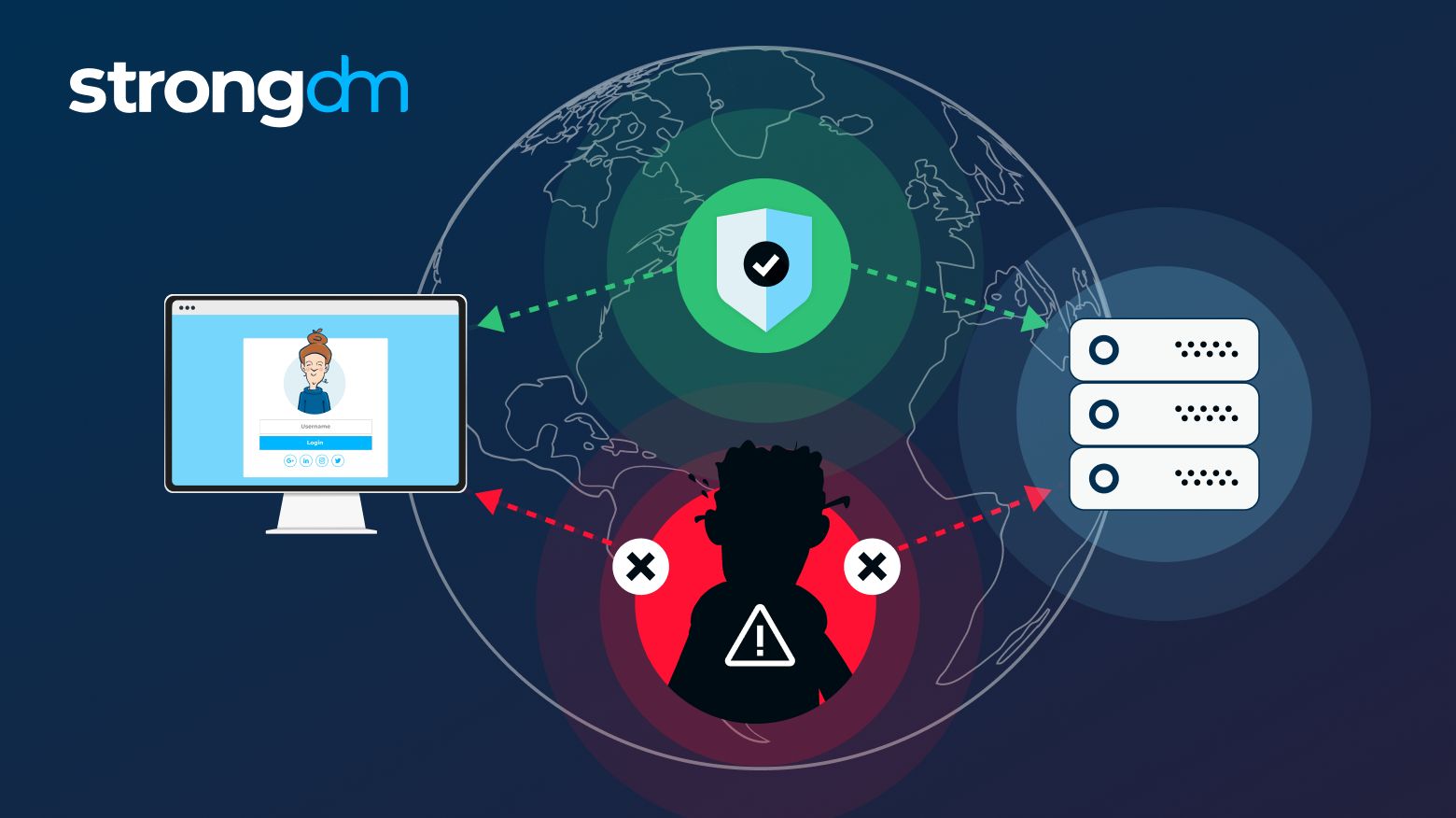
In this article, we go over the man-in-the-middle attack definition and discuss the different types of these attacks. We'll take a deep dive into the dangers of man-in-the-middle attacks and address some examples. By the end of this article, you'll have a complete understanding of how a man-in-the-middle attack works and how to detect and prevent one.
In this article, we’ll take a look at insider threats in cyber security and the dangers they pose. You’ll learn the insider threat definition, who the insiders are, the types of insider threats to be aware of, and how to detect threats. By the end of this article, you’ll have a clearer understanding of the entire insider threat ecosystem and the best practices you can use to protect your organization, data, and systems.
In this article, we’ll take a comprehensive look at brute force attacks: what they are, how they work, and the different shapes they can take. You'll learn about popular tools utilized by hackers and examples of brute force attacks in action. By the end of this article, you'll be able to understand critical prevention measures for brute force attacks.
Advanced threat protection is a type of cybersecurity dedicated to preventing pre-planned cyberattacks, such as malware or phishing. ATP combines cloud, file sharing, email, network, and endpoint security.
SASE is a cloud-based network security solution, whereas SD-WAN is a network virtualization solution. SASE can be delivered as a service, making it more scalable and resilient than SD-WAN. Additionally, SASE offers more comprehensive security features than SD-WAN, including Zero Trust security and built-in protection against Distributed Denial-of-Service (DDoS) attacks.