Secure access controls must be applied universally and consistently across all your infrastructure—from the Linux boxes in your datacenter to your Kubernetes clusters in AWS. StrongDM Dynamic Access Management is uniquely positioned to provide seamless, secure access across your entire stack, simplifying access management and compliance for your legacy systems and modern cloud stack.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Compliance
- Policy
- Databases
- SOC 2
- Authentication
- Identity and Access Management
- Team
- Compare
- Engineering
- Integrations
- Product
- Kubernetes
- AWS
- Productivity
- Podcasts
- SSH
- Observability
- HIPAA
- ISO 27001
- Role-Based Access Control
- Dynamic Access Management
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI

AWS authentication confirms the identity of users trying to access your resources, safeguarding against potential intrusions and data breaches. But weak authentication practices—like easy-to-guess passwords and single-factor authentication (SFA)—are far too common and they leave the door wide open for threat actors. Weak authentication often leads to data theft, resource misuse, financial and reputational nightmares…the list goes on. On the contrary, strong authentication measures like
So, you’ve decided to conduct an annual access audit. Now comes the obvious question: where do I start? Just like you wouldn’t embark on a mountain climbing excursion without a clear understanding of the terrain and gear you need, the starting point for an annual access audit requires an understanding of the process, people, and tools you’ll need to get started. Let’s go!
The great outdoors and your infrastructure have more in common than you might think. Both environments have diverse ecosystems and unique terrain, but they can also feel wild and untamed. In the spirit of adventuring and access, we wrote this blog to help you learn why you should conduct an annual access audit every year.

Secret vaults ensure that sensitive and privileged credentials are well protected, rotated, and only used–or checked out–when necessary. This makes them a critical and foundational tool for credential protection in modern infrastructures.

The inability to audit, track, and understand how permissions are being used (or if they’re used at all) has been non-existent. Until now. The findings are clear: organizations need visibility into privileged access and its usage to fully understand and address their total attack surface.
We’ve just launched our AWS Management Console, adding yet another supported authentication method to improve control and auditability–so you can protect your business and improve employee productivity.
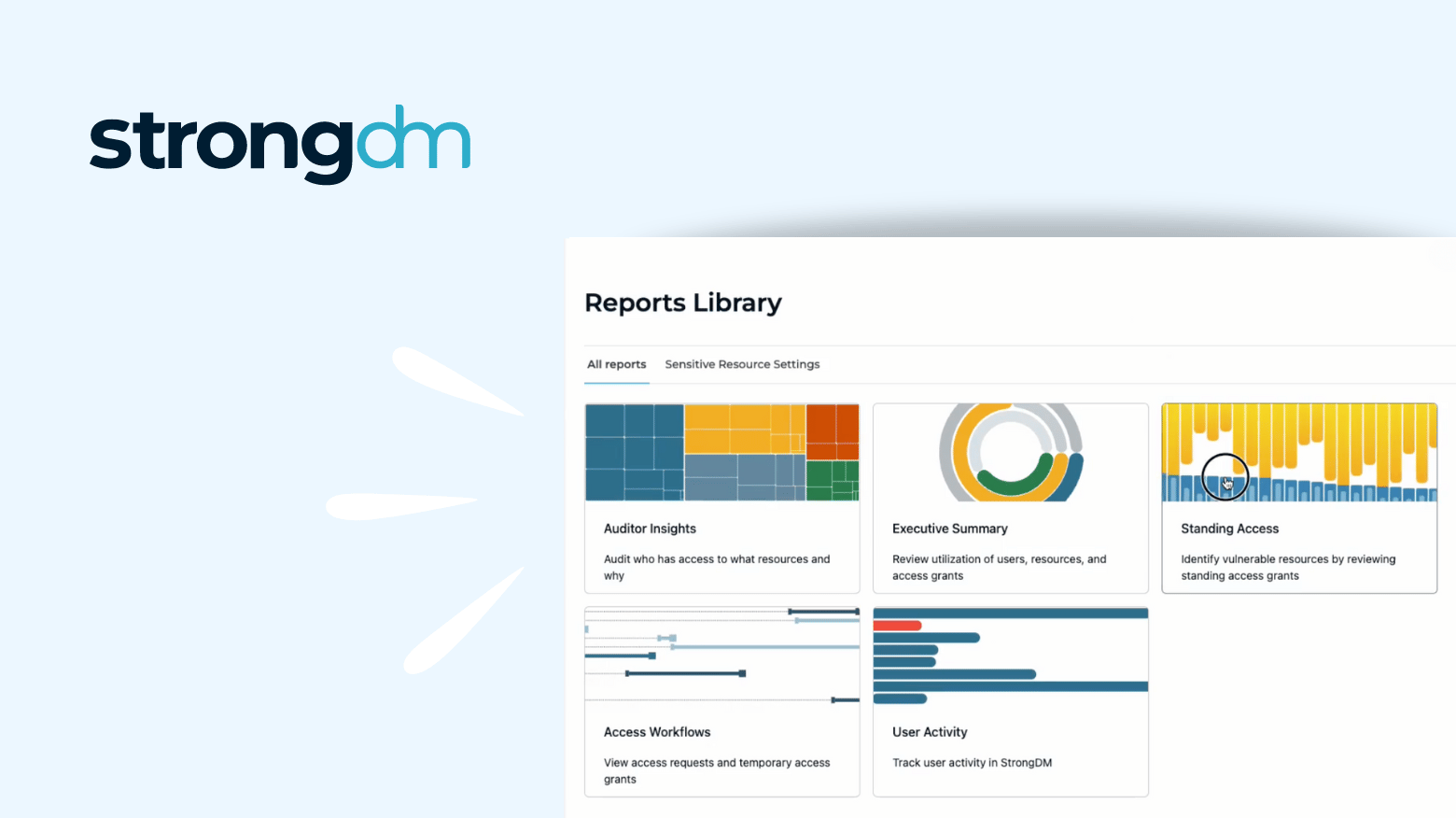
One thing is clear in the software space: New features aren’t adopted if they don’t solve specific problems for the people who actually use the product. Solving real problems means conducting research and asking hard questions. It means gathering evidence and interviewing multiple customers as well as leaders in the space to relieve the pain and positively impact the business.

Both StrongDM and Teleport are access control solutions designed to provide secure access to databases, servers, clusters, and web apps. While there are some similarities between the two solutions, there are also some key differences.
AWS Secrets Manager is a popular and highly intuitive secrets management tool that lets organizations automate secrets rotation processes and securely store, manage, and audit IT credentials. However, certain AWS Secrets Manager alternatives are available if you are looking to avoid getting tied down exclusively to AWS products or prioritize efficient user onboarding. In this product comparison guide, we evaluate AWS Secrets Manager competitors that can fill in some of its product gaps.
Microsoft Azure Key Vault is a cryptographic and secrets management solution for storing encryption keys, certificates, and passwords. While known for its interface simplicity and robust security, users should look to Azure Key Vault alternatives if they prioritize employee onboarding automation or need quick and easy implementation. This article evaluates Azure Key Vault competitors regarding security features, pricing, and usability to identify the best alternative options.
Google Cloud Secret Manager is an intuitive platform for managing API keys, user passwords, digital certificates, and other sensitive data and administering access control policies for business resources. While cost-friendly and reliable for securing Google Cloud applications, you should look to other Google Cloud Secret Manager competitors if you manage complex infrastructure and need multiple integrations.

A continuous integration, continuous delivery pipeline—or CI/CD pipeline—is a process workflow companies use to streamline and automate software development. A CI/CD pipeline automatically builds and tests code changes to detect bugs before the new code is merged and deployed.
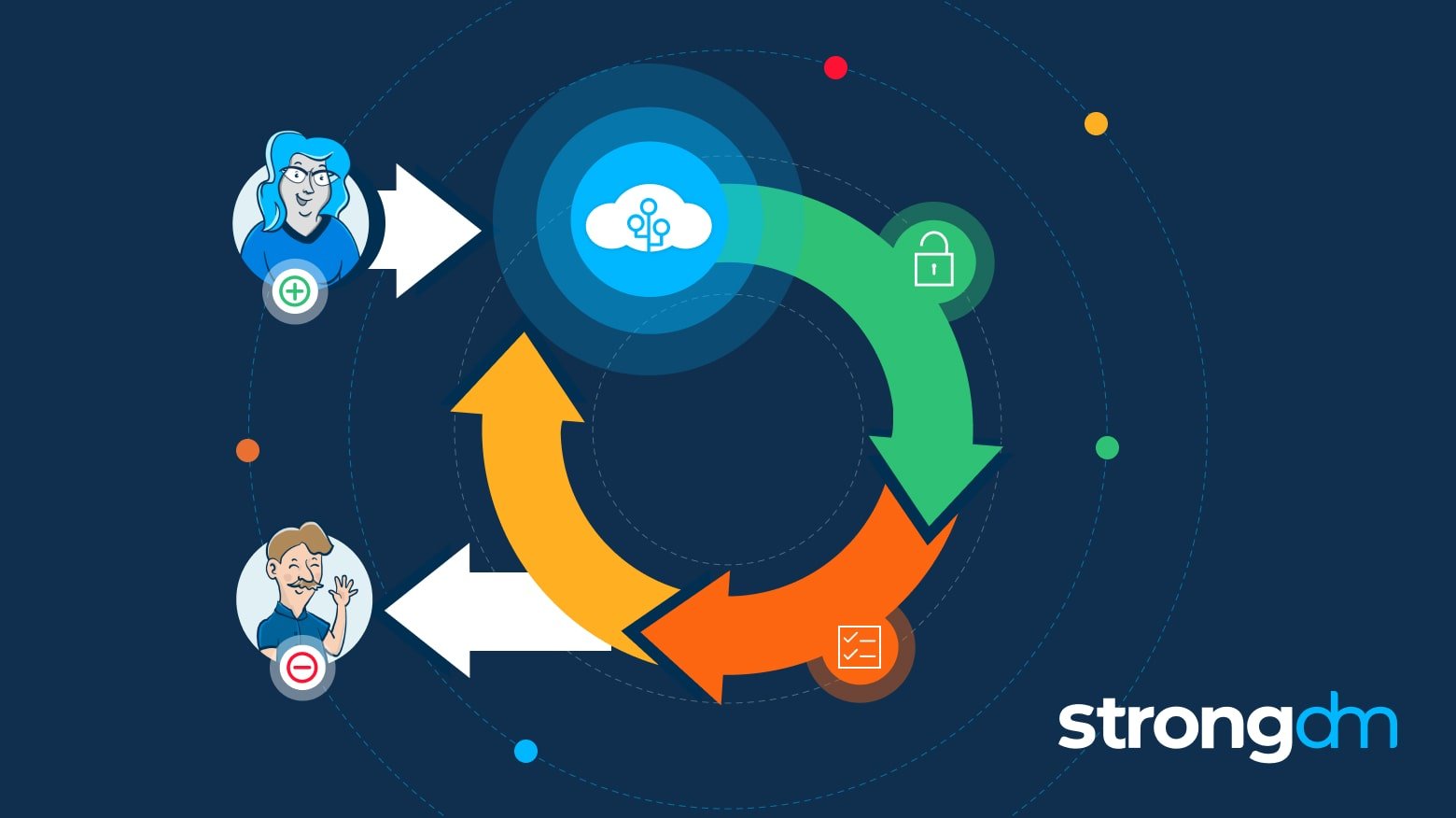
In this article, we will define SCIM and cover the basics of SCIM security. You’ll learn what SCIM stands for, how SCIM provisioning works, and why SCIM SSO is essential. By the end of this article, you will have a clear understanding of what SCIM means and how auto-provisioning via SCIM streamlines cloud identity management, increases employee productivity, and reduces IT costs.