Infrastructure and DevOps administrators face significant barriers in managing Secure Shell (SSH) keys. In this article, we’ll explore the complexities of SSH key management. We’ll also show how to effectively authenticate users without having to manage SSH keys for individual users.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Policy
- Compliance
- SOC 2
- Authentication
- Databases
- Identity and Access Management
- Compare
- Team
- Product
- Integrations
- Kubernetes
- AWS
- Engineering
- Productivity
- Podcasts
- Observability
- SSH
- HIPAA
- ISO 27001
- Dynamic Access Management
- Role-Based Access Control
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI
Kubernetes authentication presents a unique challenge. While Kubernetes defines the concepts of both user accounts and service accounts natively, it doesn’t provide us with a single, built-in method for authenticating those accounts. Instead, we must choose from a variety of techniques involving third-party tools or resources to perform Kubernetes cluster authentication.
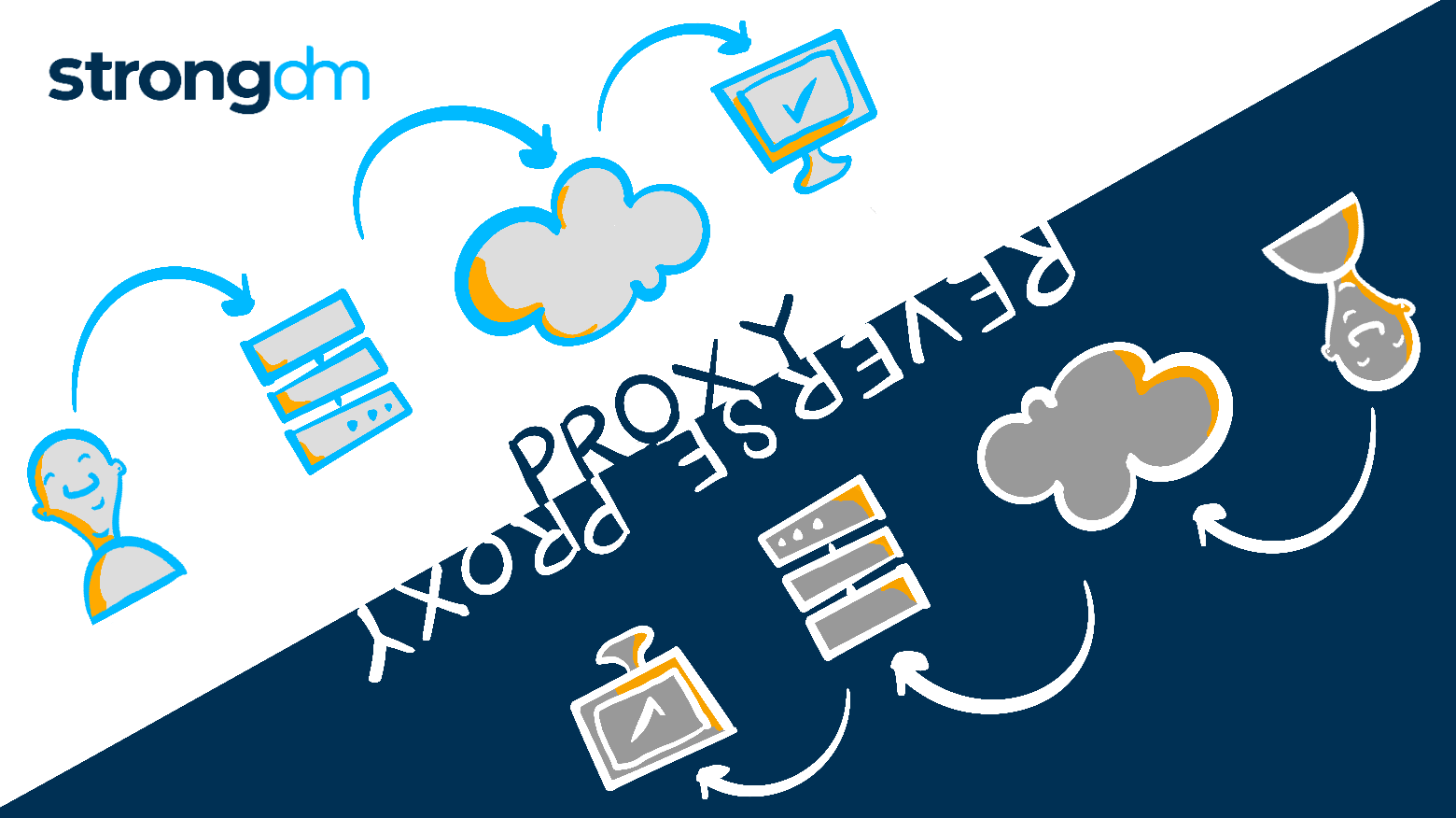
In this post, we’ll dissect the two concepts and explain how administrators can use a reverse proxy for easy access management control.

Consider this when you choose to integrate Active Directory (AD) with your databases and applications using their native APIs, connectors, or toolkits.

Find an easier way to manage access privileges and user credentials in MySQL databases. Reduce manual, repetitive efforts for provisioning and managing MySQL access and security with strongDM.

On an unmodified MySQL install, the root user account does not have a password. This is extremely insecure! As a systems administrator, we know that the easiest way to compromise a system is using the default unchanged password with admin privileges.

Configure the hosts for logging verbose data, and then send the logs to a cloud provider for long-term storage and access.

SSH audit logs allow you to determine, either retroactively or in real-time, when an unauthorized or destructive action was taken, and by whom.

Whether you’re looking to achieve SOC 2 compliance, or just want to learn more about it, your Googling is bound to lead you to a wealth of articles chock full of buzzwords and acronym soup. In this post, we will provide a guide with definitions, links and resources to gain a solid understanding of everything you need to know about SOC 2 audits.

In this post, we will help you get started with a hierarchy to follow, as well as a summary of each individual SOC 2 policy.
Should application developers have access to production database systems? This is a question as old as Vampires and Werewolves.

A software development lifecycle (SDLC) policy helps your company not suffer a similar fate by ensuring software goes through a testing process, is built as securely as possible, and that all development work is compliant as it relates to any regulatory guidelines and business needs.Here are some primary topics your software development lifecycle policy and software development methodology should cover

Gone are the days of sharing AWS root account credentials in a shared 1Password vault or worse, via email. With this in mind, one of the first steps to securing our AWS account is setting up AWS IAM.