Creating Postgres users isn't just a routine step in the complicated world of database management; it's a critical strategy that has a significant impact on how PostgreSQL databases operate and remain secure. An increasing number of organizations depend on sophisticated data systems, so it's critical to recognize the value of Postgres users. This blog post walks you through the steps of creating a Postgres user, as well as, explores the significance of these users in database administration,
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Policy
- Compliance
- SOC 2
- Authentication
- Databases
- Identity and Access Management
- Compare
- Team
- Product
- Integrations
- Kubernetes
- AWS
- Engineering
- Productivity
- Podcasts
- Observability
- SSH
- HIPAA
- ISO 27001
- Dynamic Access Management
- Role-Based Access Control
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI
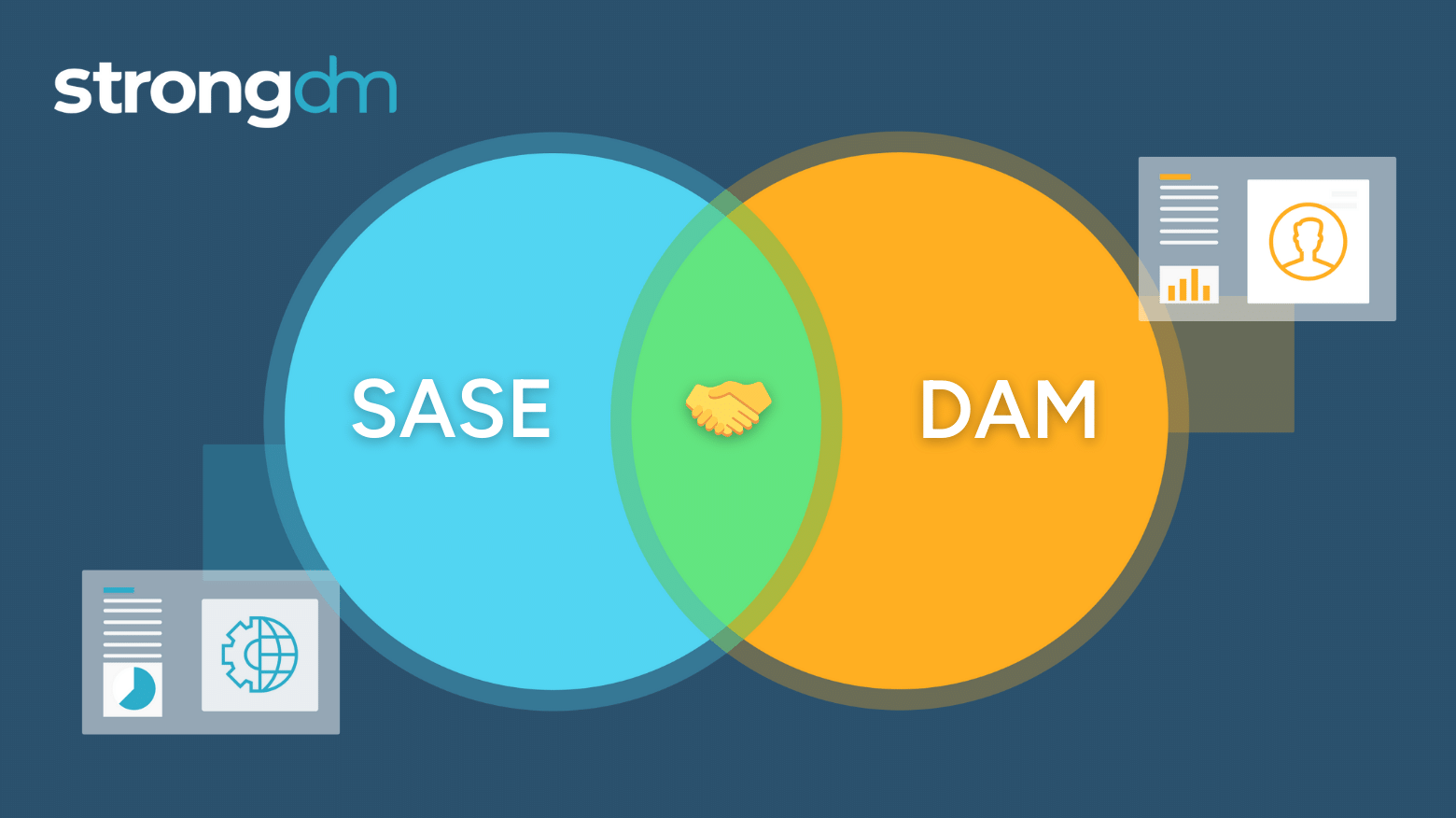
While SASE excels in providing broad network security coverage and solves broad issues for regular enterprise users, it is not equipped to address the specific requirements of privileged users who wield extensive administrator or superuser privileges. Dynamic Access Management (DAM) addresses the specific needs of privileged users by providing granular control over their access grants and sessions in real time.
The CSA CCM is a cybersecurity control framework specifically designed for cloud computing. It outlines a comprehensive set of best practices and security controls across 17 domains that are designed to ensure that cloud environments are secure and resilient against an ever expanding threat landscape. The CCM framework is structured to provide clarity and actionable guidance for the implementation of security measures in a prescriptive and adaptable way for recognized compliance standards and
![How to Prevent Credential Stuffing [9 Best Practices]](https://discover.strongdm.com/hubfs/credential-stuffing-prevention.png)
In this article, we’ll explore the risks of credential stuffing attacks, common techniques used by attackers, signs that your accounts may be compromised, and credential stuffing prevention techniques you can use to reduce your risk.

Fine-grained access control systems determine a user’s access rights—to infrastructure, data, or resources, for example—once past initial authentication. Unlike coarse-grained access control (CGAC), which relies on a single factor, such as role, to grant access, FGAC relies on multiple factors. For example, it may consider policies (policy-based access control, or PBAC), attributes (attribute-based access control, or RBAC), or a user’s behavior in a certain context (behavior-based access

People come, and people go, and while digital identities should cease to exist after a departure, many times, this doesn’t happen. At any given time, organizations can have thousands of user identities to manage and track, so when processes aren’t automated, it’s easy for many identities to fall through the cracks. This phenomenon is called Identity Lifecycle Management, and when it comes to access and security, it’s worth the time to get it right.
The AWS Well-Architected Framework has been a staple for many years for AWS practitioners of all sorts, including cloud architects and platform engineers. It’s a blueprint for architectural and design best practices that will lay the foundation for resilience, operational efficiency, and security on the AWS Cloud.
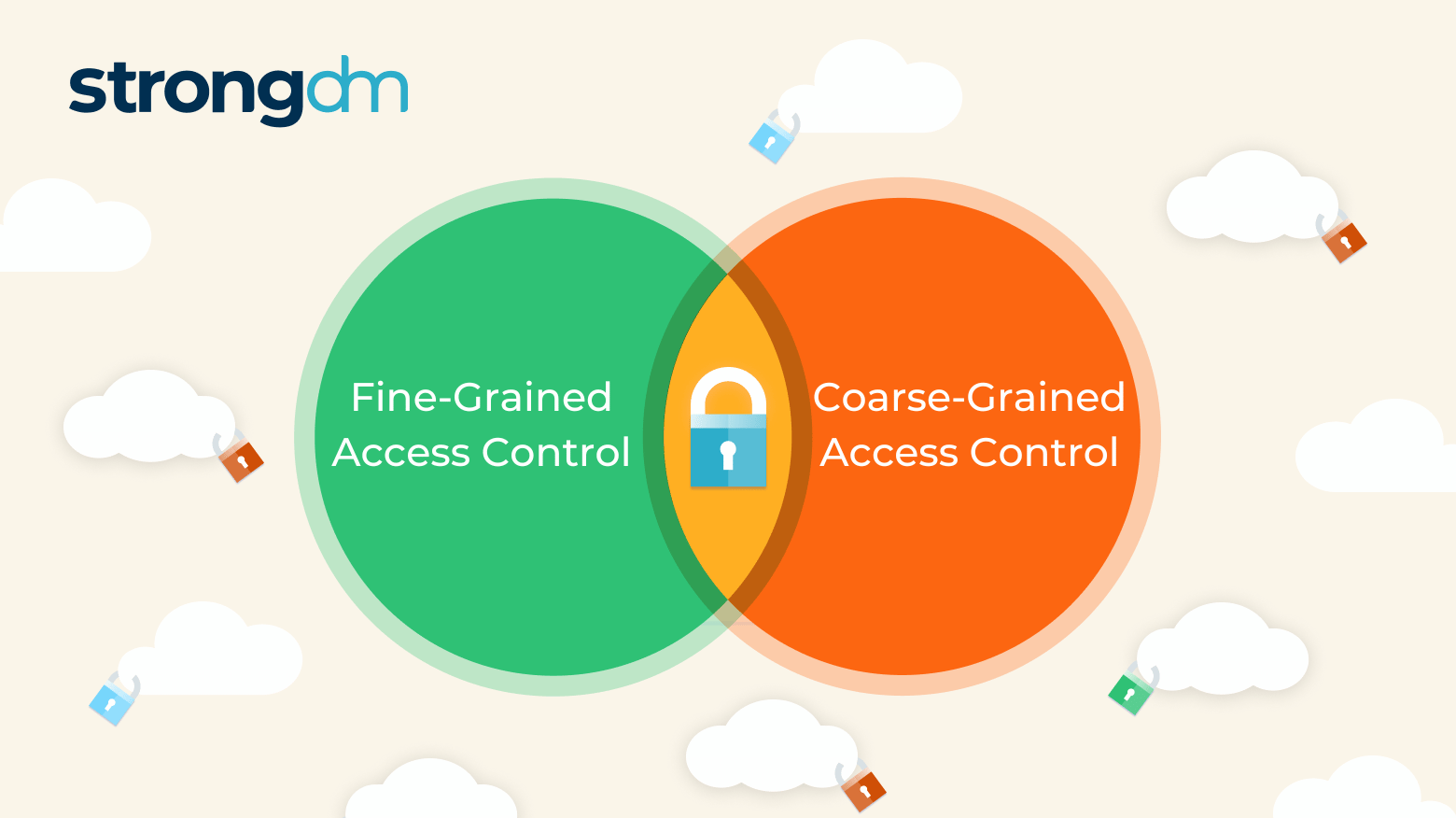
If credentials fall into the wrong hands, intruders may enter a network and launch a disastrous attack. In fact, 46% of cybersecurity incidents involve authentication credentials, according to the Verizon 2022 Data Breach Investigations Report. Organizations have two general ways to determine someone’s access rights once past initial authentication: Coarse-grained access control (CGAC), which relies on a single factor, and fine-grained access control (FGAC), which relies on multiple factors.
If you’re Kuberntes admin and you’re not familiar with the tactics outlined in the MITRE ATT&CK framework, this blog post is for you. MITRE ATT&CK framework is an extensive knowledge base of tactics and techniques employed by bad actors that defensive security experts use to help defend their organizations against attack, and many times, used by their offensive security counterparts to test their weaknesses.

To embark on a successful Zero Trust journey, it's crucial to articulate and implement policies that align seamlessly with your business model. The Kipling Method serves as a guiding light in this endeavor. Let's delve into the six fundamental questions it poses.

Since Amazon Web Services first announced it in 2011, AWS IAM has evolved to become the gateway to the AWS Cloud. Organizations cannot interact with their cloud resources and its many services without it. Identity, not networking, is the real access boundary.

Identity management (IAM) and privileged access management (PAM) are crucial tools for your cybersecurity. But both need to be approached with the best practices that: 1. Keep threats away; 2. Don’t interrupt or ruin customer experiences or production. In this article, we will go over the risks of ...
In today's rapidly evolving digital landscape, the concept of cyber resilience has taken center stage. This resilience refers to an organization's capacity to not only withstand but thrive in the face of cyber emergencies, such as the escalating menace of cyber attacks. This article delves into the critical importance of cyber resilience, shedding light on the ever-growing challenges and threats faced by organizations today, and how the right framework, like StrongDM, can fortify an
Identity and access management (IAM) and privileged access management (PAM) are critical security tools for modern organizations. However, they can sometimes bar users from accessing critical systems and services, potentially impacting production, customer experience, and cybersecurity. In urgent cases, a method of bypassing normal security controls to regain access—called “break glass”—is needed. In this post, we’ll walk you through the break-glass process—what it is, why it’s important, and

