Agent vs. Agentless architectures is a recurring debate - covering specifics from monitoring to security. But when it comes to Access Management, some key considerations are necessary when defining the scalability of your solution and its impact on efficiency and overhead over time.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Policy
- Compliance
- SOC 2
- Authentication
- Databases
- Identity and Access Management
- Compare
- Team
- Product
- Integrations
- Kubernetes
- AWS
- Engineering
- Productivity
- Podcasts
- Observability
- SSH
- HIPAA
- ISO 27001
- Dynamic Access Management
- Role-Based Access Control
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI

Privileged Access Management doesn’t solve the whole access challenge. It’s time for PAM to evolve to support complex environments and put people first.

StrongDM takes a proxy approach to the challenge of access and authentication. It uses a local client that can run on a Mac, Windows, or Linux device; a gateway to mediate access; and an administration layer for setting policies and permissions and auditing access.

With the release of tighter integrations with Okta and Azure AD (or any SCIM-based directory service for that matter), you now have the ability to manage just-in-time, least-privilege access to your critical infrastructure right from your preferred identity provider (IdP), dramatically reducing the time needed to approve requests and grant access.
strongDM asked 600 DevOps pros about the state of infrastructure access today. Their response? It’s out of control. Here’s an overview of our results.

Discovering “who has access to what” is critical for zero trust and PAM. These six steps will get you started with Access Management.
Role & Access Discovery aims to answer “Does this person, in this role, need access to that system?” Learn why this is a critical part of access management.

Today we’re going to take a closer look at the principle of least privilege (PoLP)—what it is, why it matters, and how to implement it in your organization. Understanding the principle of least privilege is critical, as network administrators must strike a balance between ease and security—protecting network access without causing friction for users. If access is too restrictive, employees won’t be able to do their jobs. Too lax, and the door to attack is open.

Concerned that bad actors could gain access to your digital resources using stolen credentials? Don't worry, there’s a way to safeguard your employees’ account details. Modern credential management tools and policies can give you precise control over who can view keys to access your systems and how much access they may have. The information in this article will help you conquer your biggest credential management challenges. With the right knowledge and tools, you can significantly mitigate the
It’s easy to assume that individuals with privileged access will inherently do the right thing, or simply know what they’re doing when accessing systems. That isn’t always the case. Similarly, how often do you check in on your systems with privileged access to understand what they're up to?

This article will introduce several best business VPN alternatives to help you secure remote access using the infrastructure you already have. You’ll see how teams of all sizes—from three-person startups to large organizations like Peloton—have replaced outdated VPN architecture with secure, scalable, auditable solutions built for modern computing.
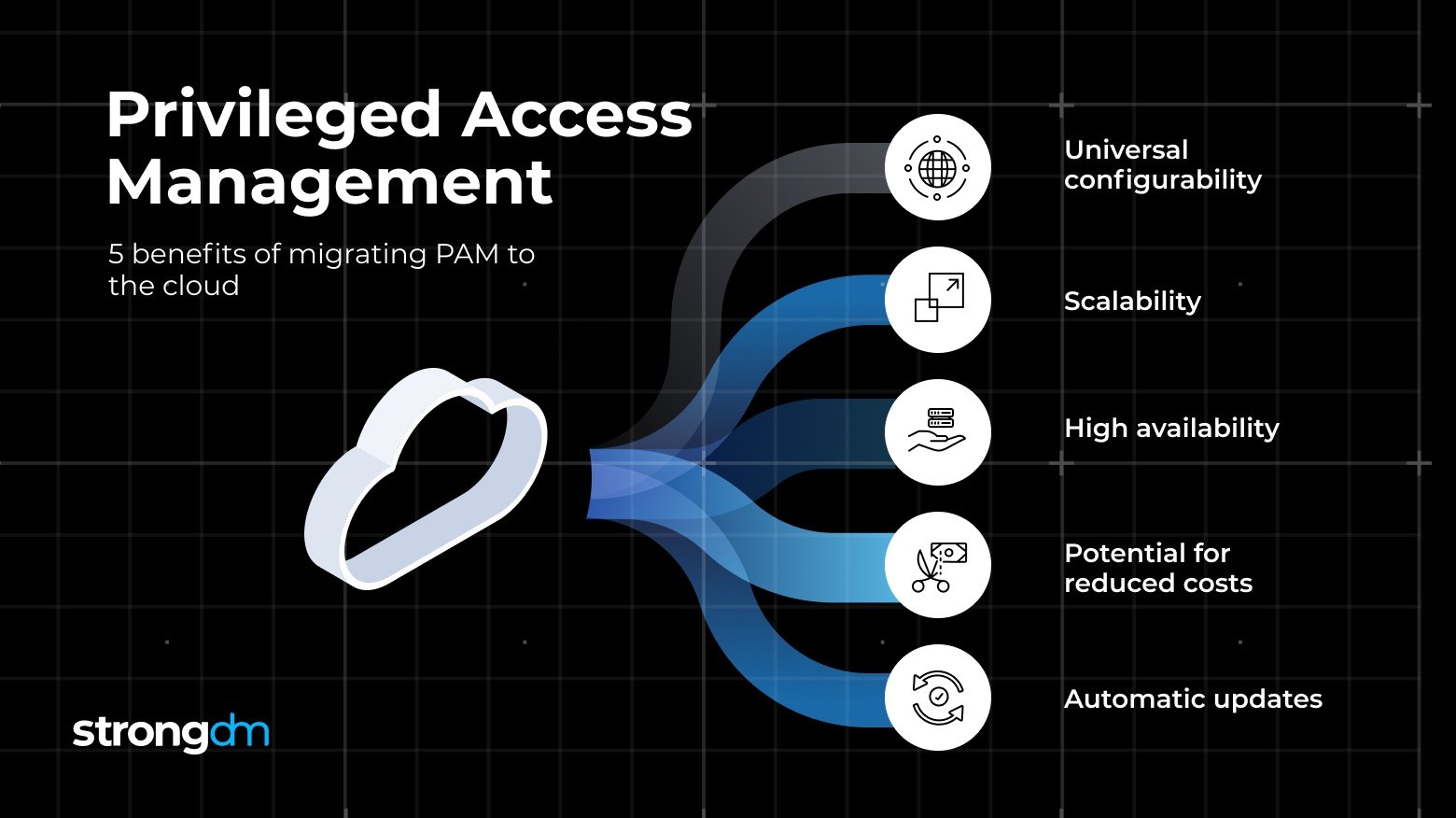
You’re moving to the cloud, but your PAM solution won’t migrate. Everyone needs access. It’s time to rethink your access management strategy.
Should application developers have access to production database systems? This is a question as old as Vampires and Werewolves.


