Discover why traditional secrets management isn't enough. StrongDM Managed Secrets offers vault-agnostic, Zero Trust security with secretless access, dynamic policy enforcement, automated rotation, and unified audits—perfect for complex enterprise environments.
Posts by Category:
- Security
- Access
- DevOps
- Privileged Access Management
- Auditing
- Zero Trust
- Policy
- Compliance
- SOC 2
- Authentication
- Databases
- Identity and Access Management
- Compare
- Team
- Product
- Integrations
- Kubernetes
- AWS
- Engineering
- Productivity
- Podcasts
- Observability
- SSH
- HIPAA
- ISO 27001
- Dynamic Access Management
- Role-Based Access Control
- Secure Access Service Edge
- Webinars
- Events
- NIST
- Onboarding
- Passwordless
- Offsites
- Platform
- PCI

As teams grow and roles shift, it’s easy for permissions to get out of sync. That’s where user access reviews come in—they ensure every employee, vendor, or service account has exactly the access they need, and nothing more.Regular reviews reduce risk, prevent privilege creep, and help meet compliance requirements like SOX, ISO 27001, and HIPAA. But manual reviews? They’re slow, messy, and often incomplete.This guide breaks down the essentials of access reviews—what they are, why they matter,
Secrets management is the practice of securely storing, accessing, and controlling digital authentication credentials such as passwords, API keys, certificates, and tokens used by applications and systems. It ensures that sensitive information is protected from unauthorized access, while supporting automation, compliance, and security across modern infrastructure.

StrongDM fixes what legacy PAM vendors get wrong. Before you start swiping for a better solution, see why security teams are breaking up with their old PAM—and how StrongDM is helping them fall in love with security again.
At first glance, legacy PAM tools might seem like a safe bet. They’re familiar and established, and they’ve been getting you from here to there for years. But take a look under the hood, and you’ll see that they’re quietly draining your resources.
Let’s talk about the unsung heroes of your on-premises infrastructure: network devices. These are the routers, switches, and firewalls that everyone forgets about…and takes for granted—until something breaks. And when one of those somethings breaks, it leads to some pretty bad stuff. If your network goes down, that’s bad, bad, bad for business. But if those devices lack the necessary security, well, that can leave you exposed in an incredibly dangerous way.

Privileged Identity Management (PIM) is a complex cybersecurity approach. But it’s the only proven method you can use to lock down access and protect your precious resources. It can help you keep cybercriminals out and ensure that even your trusted users can’t accidentally—or intentionally—jeopardize your system’s security.
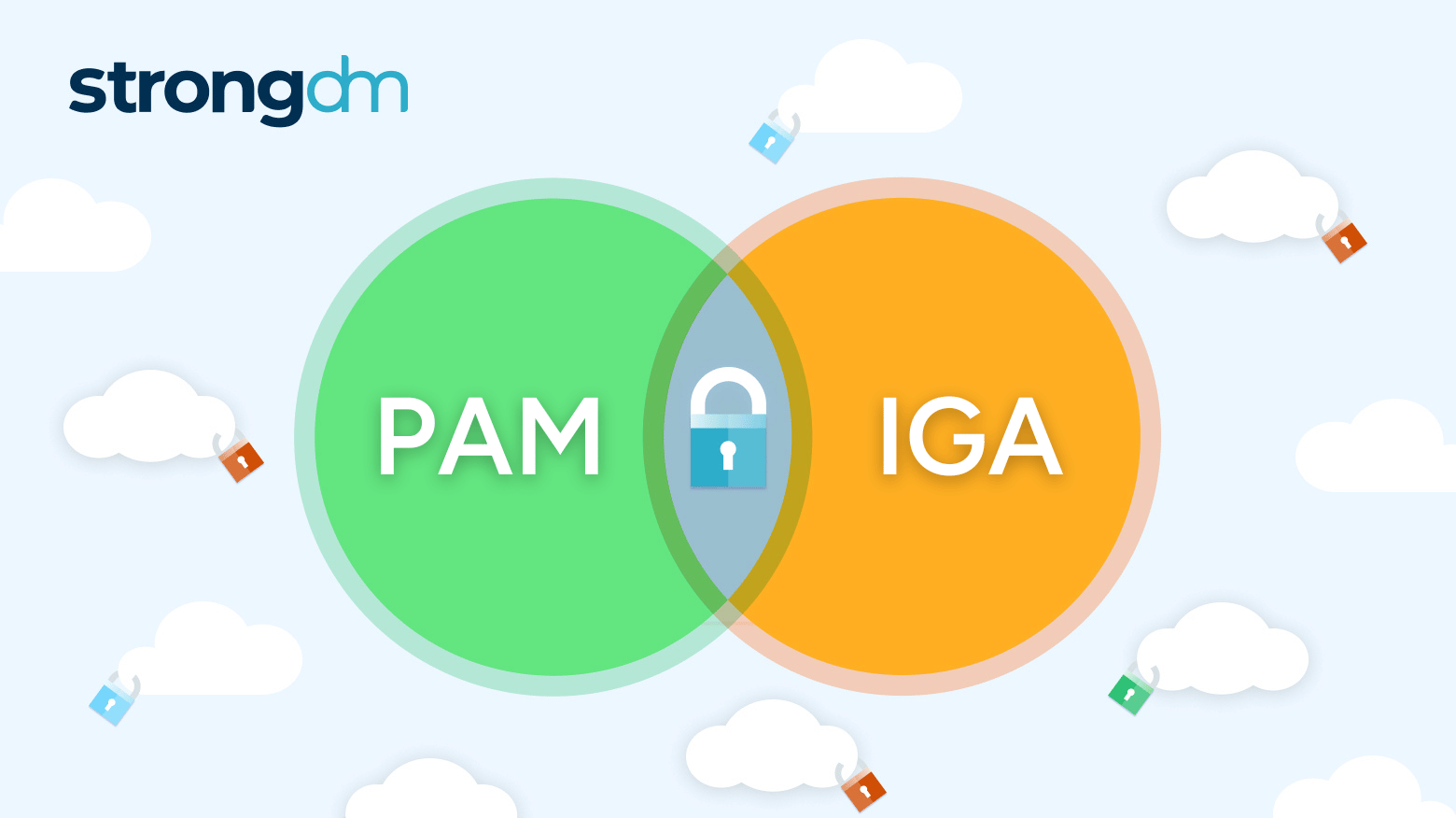
IGA (Identity Governance and Administration) manages user identities and access across the organization, ensuring proper access and compliance. PAM (Privileged Access Management) secures privileged accounts with elevated permissions by using measures like credential vaulting and session monitoring to prevent misuse. While IGA handles overall user access, PAM adds security for the most sensitive accounts.

In essence, legacy PAM solutions over-index on access. StrongDM uses the principles of Zero Trust to evaluate and govern every action, no matter how minor - where each command, query, or configuration change is evaluated in real-time against dynamic policies that adapt to the context of the user, the sensitivity of the action, and the prevailing threat landscape.
The way that people work continues to evolve, and as a result, so do the ways that they must authenticate into their organization’s resources and systems. Where once you simply had to be hardwired into the local office network, now you must expand your perimeter to include remote and hybrid workforces, on-prem and cloud environments, and take into account a growing list of factors that impact how and where people access critical company resources.

Understanding the pillars of access control and following best practices for PAM gives you a roadmap to an implementation that is secure and comprehensive with no security gaps. This article contains nine essential privileged access management best practices recommended by our skilled and experienced identity and access management (IAM) experts.

Vendor Access Management (VAM) is the systematic control and oversight of vendor access to an organization's systems, applications, and data. It involves processes such as onboarding and offboarding vendors, utilizing solutions for Just-in-Time access, ensuring security, and streamlining workflows to minimize operational inefficiencies.
The New York Department of Financial Services (“NYDFS”) Cybersecurity Regulation is a set of comprehensive cybersecurity requirements that apply to financial institutions operating in New York. The goal of the regulation is to ensure that the cybersecurity programs of financial institutions have robust safeguards in place to protect customer data and the financial sector.